Software supply chain insecurity
Society has a software problem. Our watches have file systems; combat aircraft come with software updates; and every organization from the Internal Revenue Service to an Etsy storefront relies on software to serve its users. No longer confined merely to computers, embedded software now controls the operation of complex power generators, medical hardware, and planetary scale datasets. A generation of Western defense systems relies on the benefits of Commercial Off-the-Shelf (COTS) technologies and the long chains of software that follow from high-bandwidth satellite data links to a growing dependence on open-source software (OSS) in machine learning applications and logistics networks. As one commentator put it, “software is eating the world.”
Despite all of its significance, software supply chain security remains an underappreciated domain of national security policymaking. While a physical system is rarely modified once it leaves the factory, software is continually updated, meaning that the supply chain for software is long and depends on users to trust their vendors and developers. This is a major source of national security risk in the threat posed to both public and private-sector organizations.
This project evaluates an open dataset of one hundred and sixty-one software supply-chain attacks and vulnerability disclosures collected from public reporting over the past ten years to show that software supply chain attacks are popular, impactful, and used to great effect by states. These attacks are impactful, giving attackers access to critical infrastructure. States like Russia, China, North Korea, and Iran attack the software supply chain as part of their offensive cybersecurity efforts. Our most recent report profiles one of these efforts, the Sunburst campaign, and draws lessons for policymakers and cybersecurity practitioners.
Policymaking for software supply chains
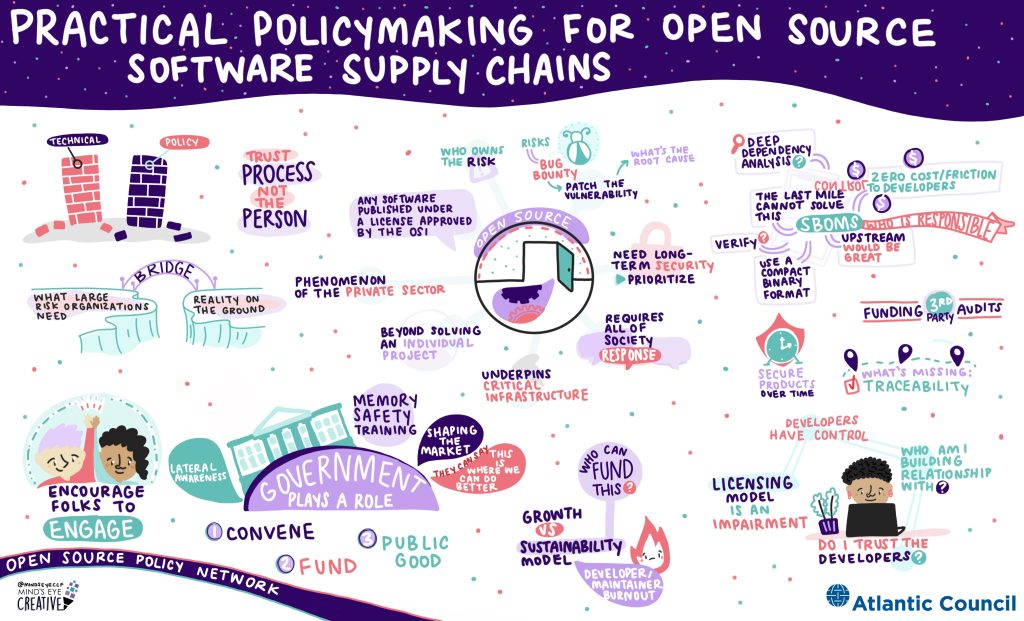
In-depth research
Short-form content
Software supply chain attack & disclosure dataset
Presented by

The Atlantic Council’s Cyber Statecraft Initiative, part of the Atlantic Council Technology Programs, works at the nexus of geopolitics and cybersecurity to craft strategies to help shape the conduct of statecraft and to better inform and secure users of technology.





