As Russia continues its assault on Ukraine, the Atlantic Council’s Digital Forensic Research Lab (DFRLab) is keeping a close eye on Russia’s movements across the military, cyber, and information domains. With more than seven years of experience monitoring the situation in Ukraine—as well as Russia’s use of propaganda and disinformation to undermine the United States, NATO, and the European Union—the DFRLab’s global team presents the latest installment of the Russian War Report.
Security
Russian army presses on in Bakhmut despite losses
Russia enacts “e-drafting” law
Drone imagery locates new burial site east of Soledar
Russian hackers target NATO websites and email addresses
Russian army presses on in Bakhmut despite losses
The General Staff of the Ukrainian Armed Forces recorded fifty-eight attacks on Ukrainian troop positions on April 9 and 10. Of these attacks, more than thirty were in the direction of Bakhmut, and more than twenty were in the direction of Marinka and Avdiivka. Russian forces also attempted to advance toward Lyman, south of Dibrova.
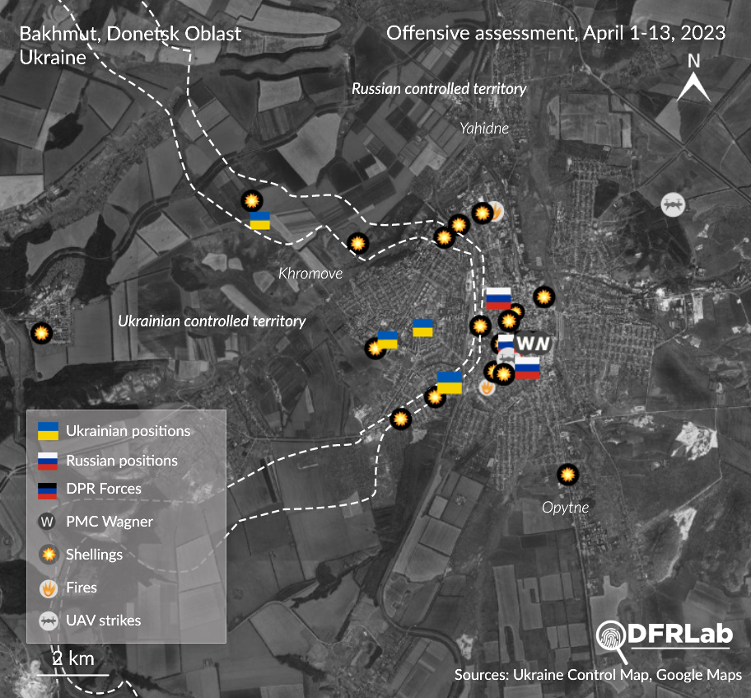
On April 10, Commander of the Eastern Group of Ukrainian Ground Forces Oleksandr Syrskyi said that Russian forces in Bakhmut increasingly rely on government special forces and paratroopers because Wagner units have suffered losses in the recent battles. Syrskyi visited Bakhmut on April 9 to inspect defense lines and troops deployed to the frontline. According to the United Kingdom’s April 10 military intelligence report, Russian troops are intensifying tank attacks on Marinka but are still struggling with minimal advances and heavy losses.
On April 13, Deputy Chief of the Main Operational Directorate of Ukrainian Forces Oleksiy Gromov said that Bakhmut remains the most challenging section on the frontline as Russian forces continue to storm the city center, trying to encircle it from the north and south through Ivanivske and Bohdanivka. According to Ukrainian estimates, during a two-week period, Russian army and Wagner Group losses in the battle for Bakhmut amounted to almost 4,500 people killed or wounded. To restore the offensive potential in Bakhmut, Russian units that were previously attacking in the direction of Avdiivka were transferred back to Bakhmut.
On April 8, Commander of the Ukrainian Air Forces Mykola Oleshchuk lobbied for Ukraine obtaining F-16 fighter jets. According to his statement, Ukrainian pilots are now “hostages of old technologies” that render all pilot missions “mortally dangerous.” Oleshchuk noted that American F-16 jets would help strengthen Ukraine’s air defense. Oleshchuk said that even with a proper number of aircraft and pilots, Ukrainian aviation, which is composed of Soviet aircraft and missiles, may be left without weapons at some point. He noted the F-16 has a huge arsenal of modern bombs and missiles. The commander also discussed the need for superiority in the air and control of the sea. Currently, Russian aviation is more technologically advanced and outnumbers Ukraine, meaning Ukraine cannot adequately protect its airspace. In order for the Ukrainian army to advance and re-capture territory occupied by Russia, it will require substantial deliveries of aviation and heavy equipment like tanks, howitzers, and shells.
April 10, Ukrainian forces reported they had spotted four Russian ships on combat duty in the Black Sea, including one armed with Kalibr missiles. Another Russian ship was spotted in the Sea of Azov, along with seven in the Mediterranean, including three Kalibr cruise missile carriers.
Meanwhile, according to Ukrainian military intelligence, Russia plans to produce Kh-50 cruise missiles in June. If confirmed, this could potentially lead to increased missile strikes against Ukraine in the fall. The Kh-50 missiles in the “715” configuration are intended to be universal, meaning they can be used by many Russian strategic bombers, including the Tu-22M3, Tu-95MS, and Tu-160.
—Ruslan Trad, Resident Fellow for Security Research, Sofia, Bulgaria
Russia enacts “e-drafting” law
On April 11, the Russian State Duma approved a bill reading allowing for the online drafting of Russian citizens using the national social service portal Gosuslugi. One day later, the Russian Federal Council adopted the law. The new law enables military commissariats, or voenkomat, to send mobilization notices to anyone registered in the Gosuslugi portal. Contrary to the traditional in-person delivery of paper notices, the digital mobilization order will be enforced immediately upon being sent out to the user; ordinarily, men drafted for mobilization could dispute the reception of the notice during the twenty-one-day period after the notice was sent. As of 2020, 78 million users were reportedly registered in the Gosuslugi portal, nearly two-thirds of the Russian population.
Alongside the adoption of the digital mobilization notices are newly adopted restrictions regarding unresponsive citizens. Those who fail to appear at their local military commissariat in the twenty-day period following notice will be barred from leaving the country and banned from receiving new credit or driving a car. Of the 164 senators who took part in the vote, only one voted against the bill; Ludmila Narusova argued that the law had been adopted exceptionally hastily and that the punishments against “deviants” who do not respond to the notice are “inadequate.”
As explained by Riga-based Russian news outlet Meduza, the law also states that reserves could be populated with those who legally abstained from military service until the age of twenty-seven, due to an amendment in the bill that allows for personal data to be shared with the Russian defense ministry in order to establish “reasonable grounds” for mobilization notices to be sent out. Several institutions across the country will be subject to the data exchange, including the interior ministry, the federal tax office, the pension and social fund, local and federal institutions, and schools and universities.
–Valentin Châtelet, Research Associate, Security, Brussels, Belgium
Drone imagery locates new burial site east of Soledar
Images released by Twitter user @externalPilot revealed a new burial site, located opposite a cemetery, in the village of Volodymyrivka, southeast of Soledar, Donetsk Oblast. The DFRLab collected aerial imagery and assessed that the burial site emerged during the last week of March and the first week of April. The city of Soledar has been under Russian control since mid-January. The burial site faces the Volodymyrivka town cemetery. Drone footage shows several tombs with no apparent orthodox crosses or ornaments. Analysis of the drone imagery indicates around seventy new graves have been dug on this site. A DFRLab assessment of satellite imagery estimates the surface area of the burial site amounts to around thirteen hectares.
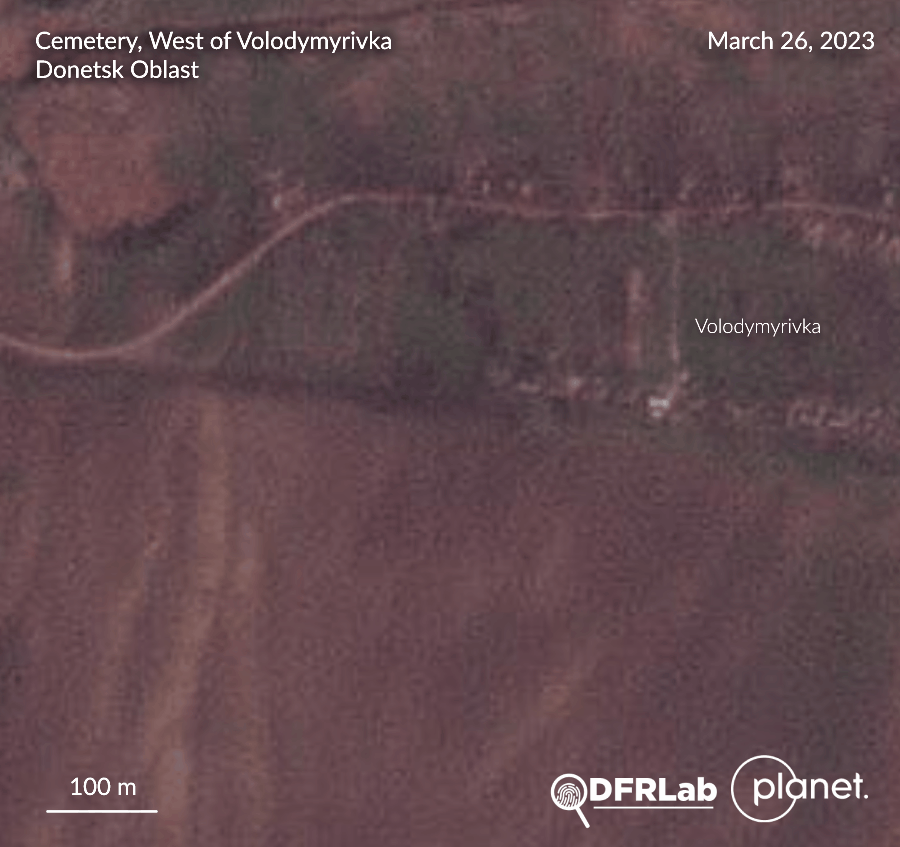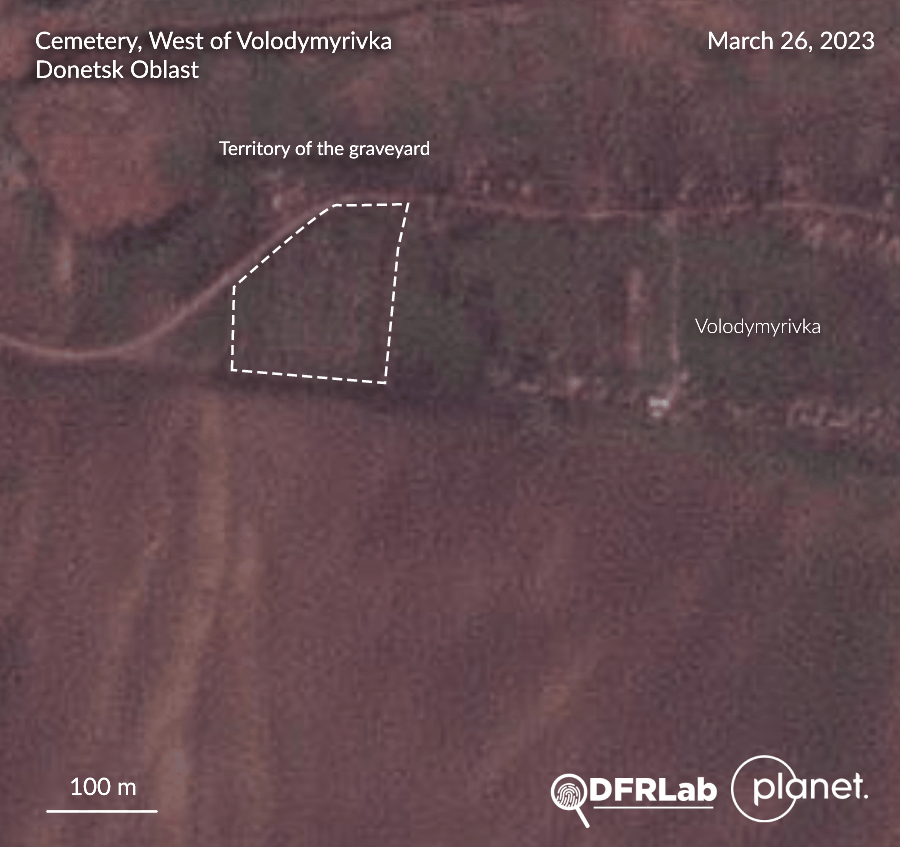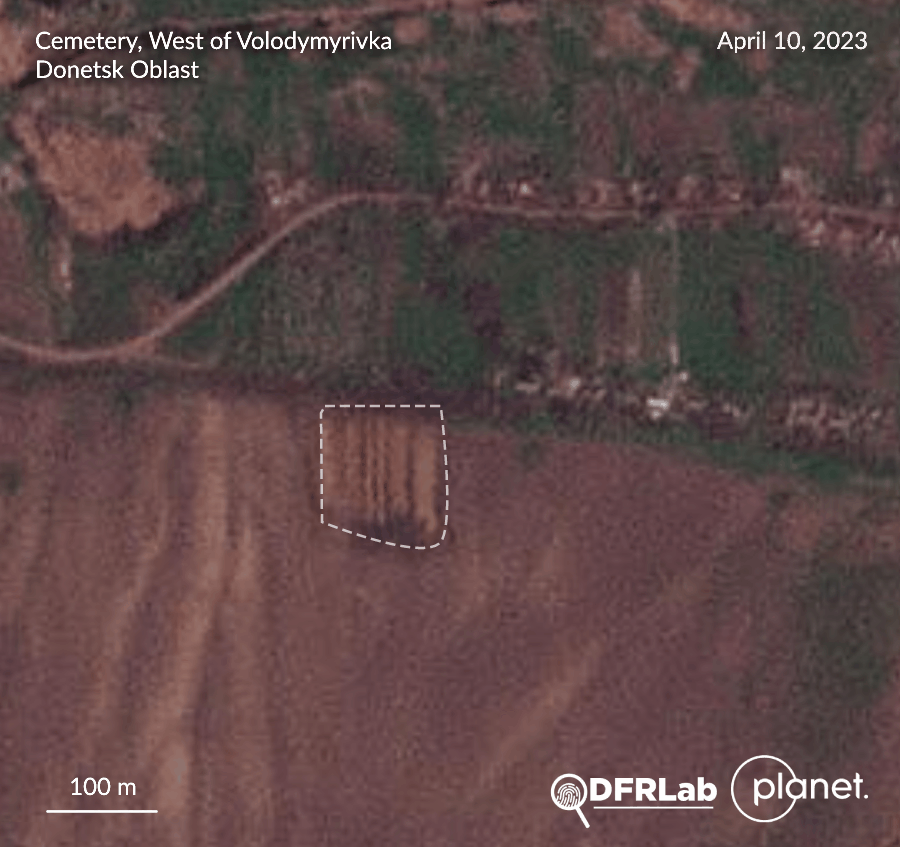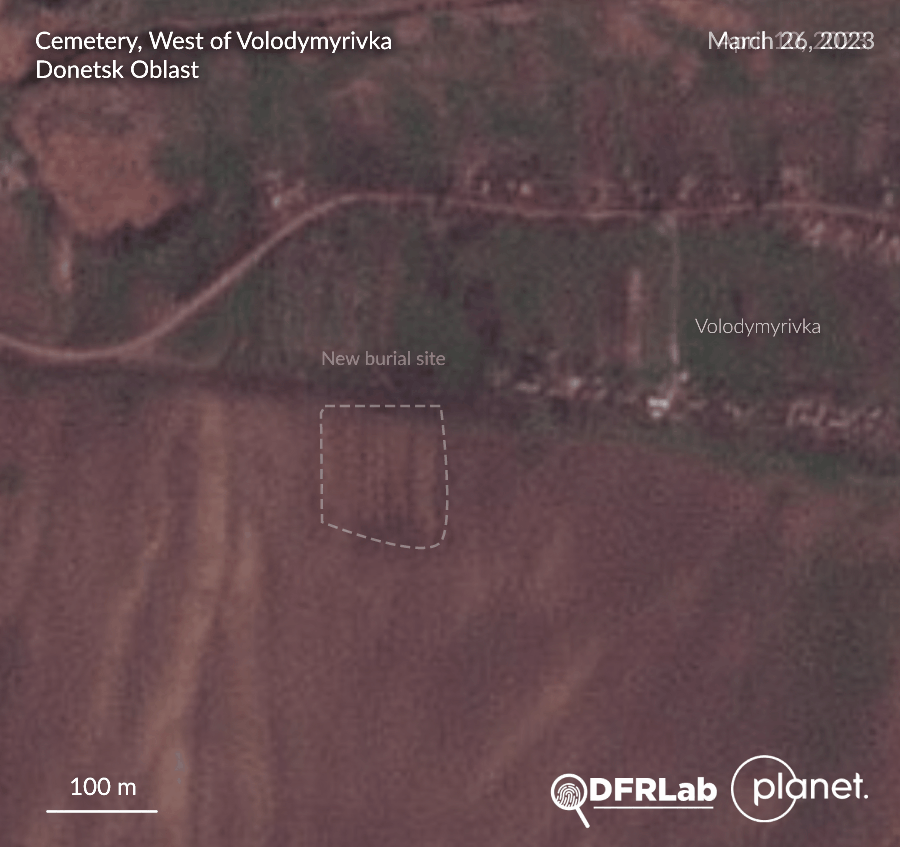
–Valentin Châtelet, Research Associate, Security, Brussels, Belgium
Russian hackers target NATO websites and email addresses
On April 8, the pro-war Russian hacktivist movement Killnet announced they would target NATO in a hacking operation. On April 10, they said they had carried out the attack. The hacktivists claimed that “40% of NATO’s electronic infrastructure has been paralyzed.” They also claimed to have gained access to the e-mails of NATO staff and announced they had used the e-mails to create user accounts on LBGTQ+ dating sites for 150 NATO employees.
The hacktivists forwarded a Telegram post from the KillMilk channel showing screenshots of one NATO employee’s e-mail being used to register an account on the website GayFriendly.dating. The DFRLab searched the site for an account affiliated with the email but none was found.
Killnet also published a list of e-mails it claims to have hacked. The DFRLab cross-checked the e-mails against publicly available databases of compromised e-mails, like Have I been Pwned, Avast, Namescan, F-secure, and others. As of April 13, none of the e-mails had been linked to the Killnet hack, though this may change as the services update their datasets.
In addition, the DFRLab checked the downtime of the NATO websites that Killnet claims to have targeted with distributed denial of service (DDoS) attacks. According to IsItDownRightNow, eleven of the forty-four NATO-related websites (25 percent) were down at some point on April 10.
—Nika Aleksejeva, Resident Fellow, Riga, Latvia
