Power’s Out, Election in Doubt

Scenario Summary
This scenario takes place from September to November of 2020, shining a light on a dire possibility–how can the United States respond to a cyberattack on the power grid , and on Election Day? The scenario unfolds by highlighting the rise of cyber mercenaries–making attribution challenging and imposing political constraints–and the acuteness of the attack on democratic legitimacy. The scenario ends with the President calling for a military response against Venezuela for their alleged role in election interference.
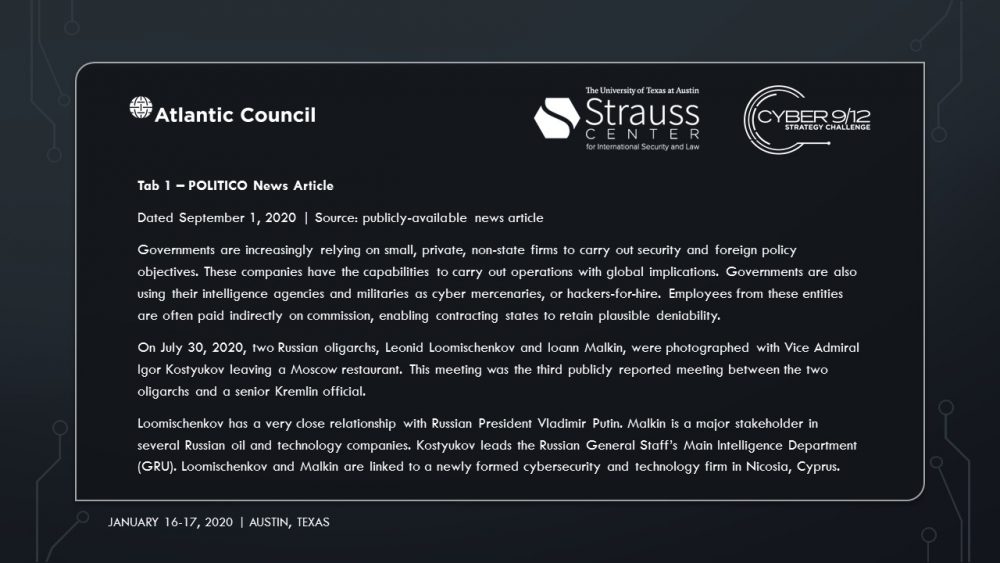
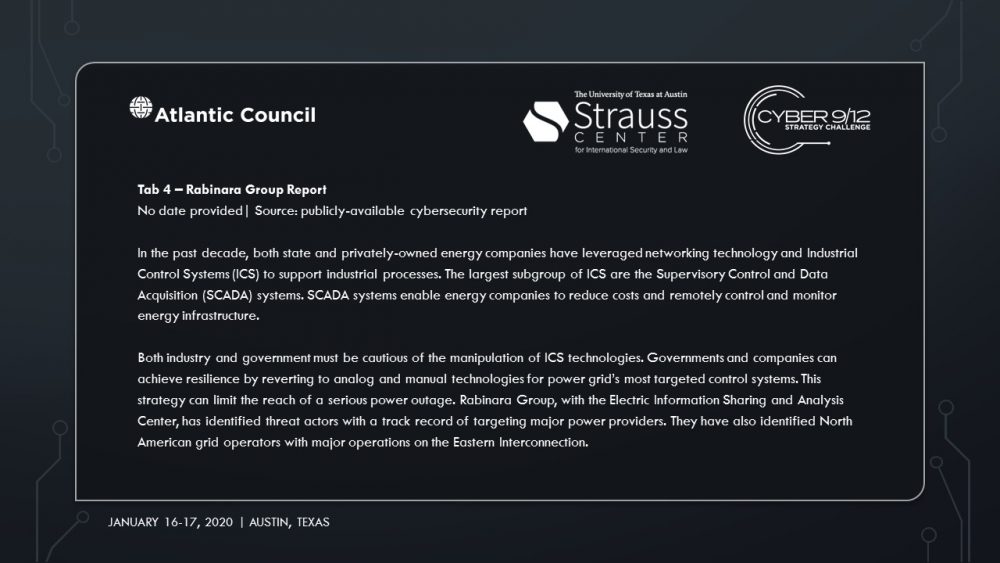
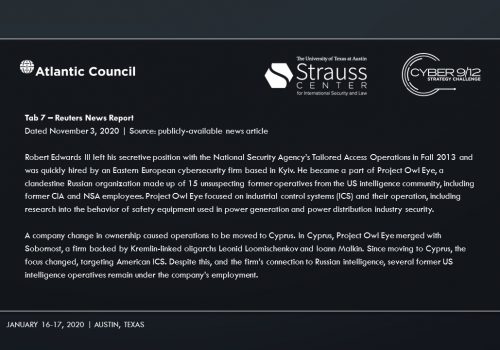
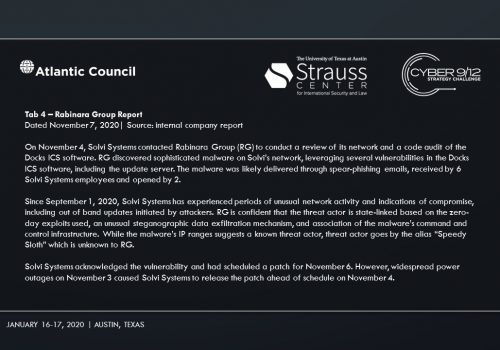
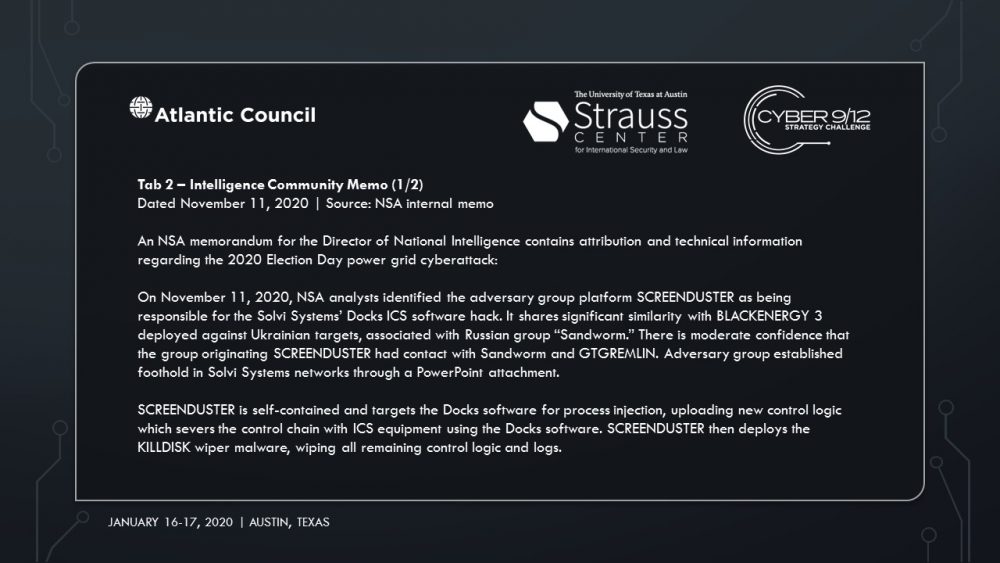
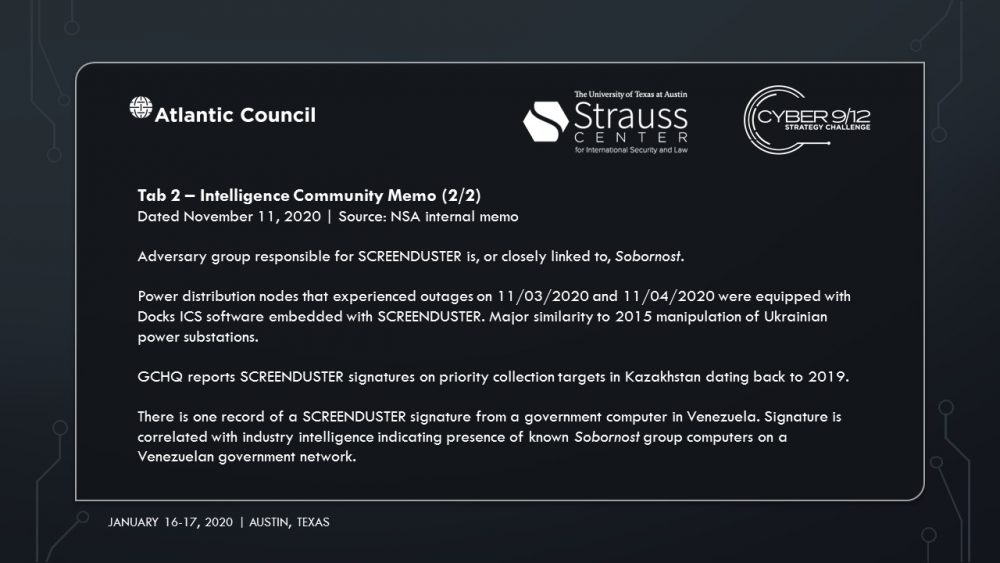
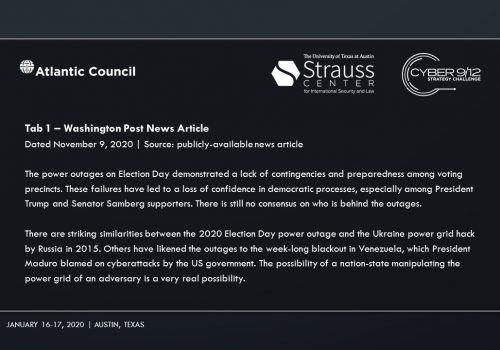
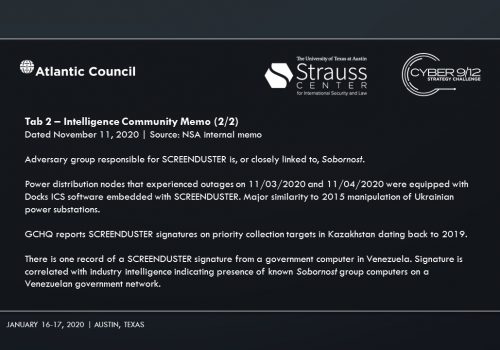
The main suspect is Sobornost, a private cyber organization that specializes in tracking “enemies of the state.” Several news reports indicate Sobornost is funded by Russian oligarchs with ties to the Kremlin. The National Security Agency (NSA) posits that Sobornost is highly likely to be responsible for creating ‘SCREENDUSTER,’ a program exploiting several vulnerabilities in the Docks industrial control system (ICS) used by power plants around the US. SCREENDUSTER was inserted by a spear-phishing attack into the network of Solvi Systems, the developer of Docks ICS. Threat actors were then able to overwrite powerplant software controls and shut out rescue attempts to incapacitate swaths of US energy infrastructure.
The scenario takes place in three Intelligence Reports – the first delivered to competitors about a month before the competition begins, the second provided to semi-finalist teams at the end of competition Day 1, and the third is given to finalist teams 15 minutes before the final round on Day 2.
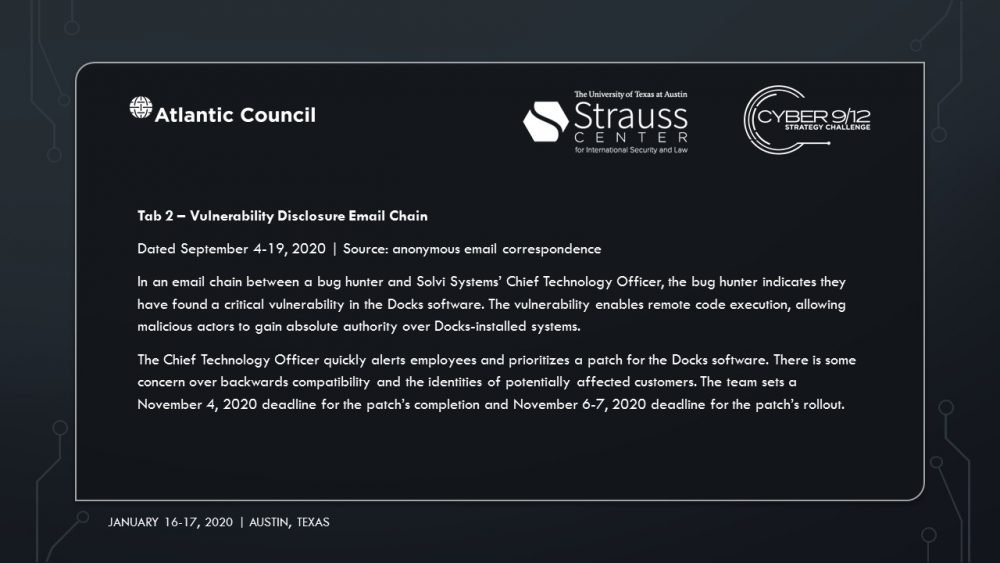
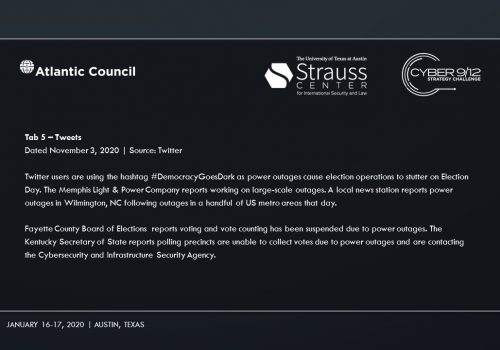
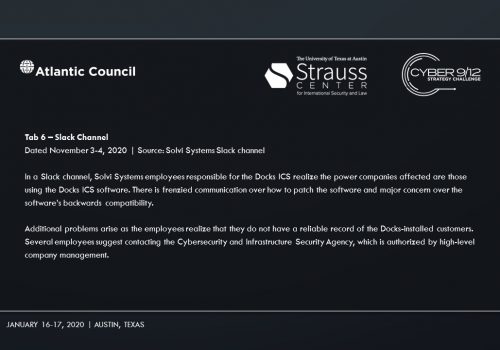
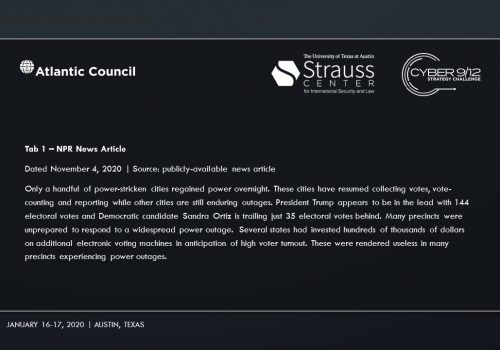
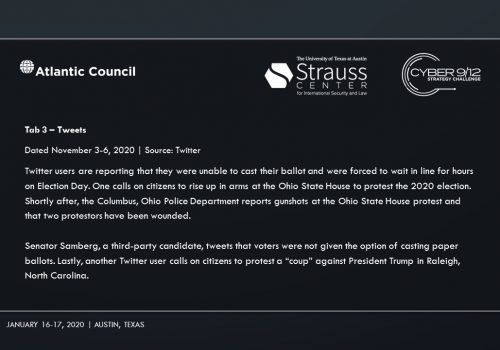
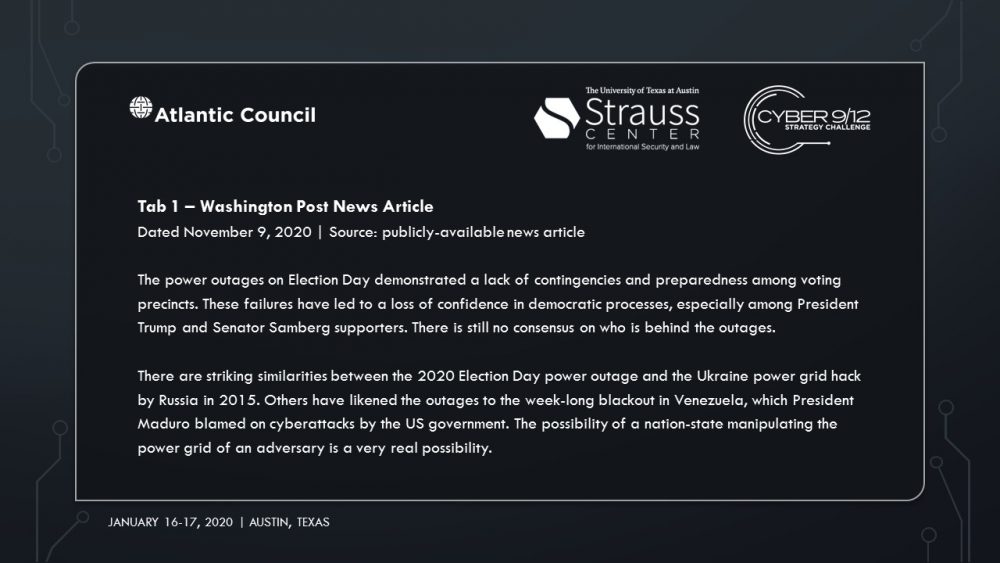
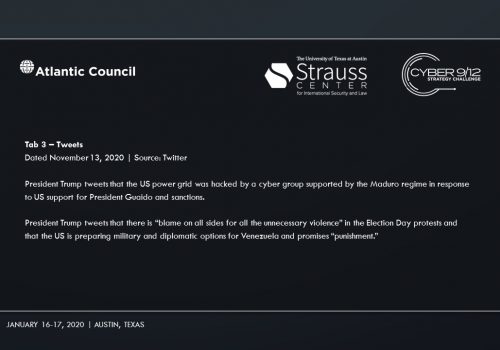
Intelligence Report I explores the emergence of cyber mercenaries and alludes to a security researcher-disclosed software vulnerability in Docks. An employee group chat transcript showing a frantic rush to patch the vulnerability—and their inability to do so–conveys the gravity of the vulnerability’s exploitation. A news report suggests that former US intelligence officers now employed by foreign firms have developed hacking tools that could take down American power grids. A collection of tweets and news articles portray the reality of power outages across the United States on Election Day. A news article lays out the allegations that Russia, likely through a private entity, may be behind the catastrophic presidential election interference. Finally, the severity of the attack on America’s democratic institutions becomes clear, as well as how it may impact the US government’s legitimacy.
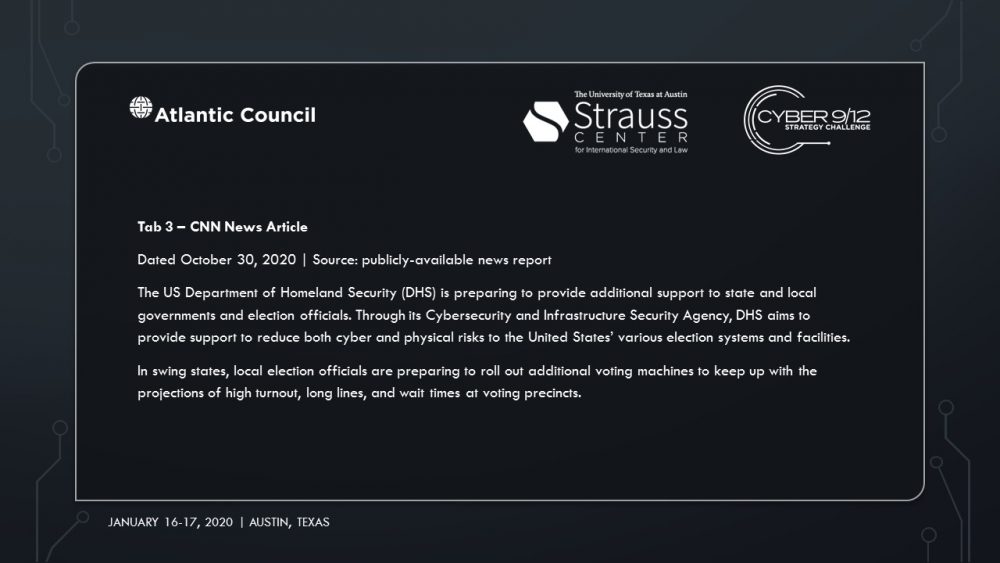
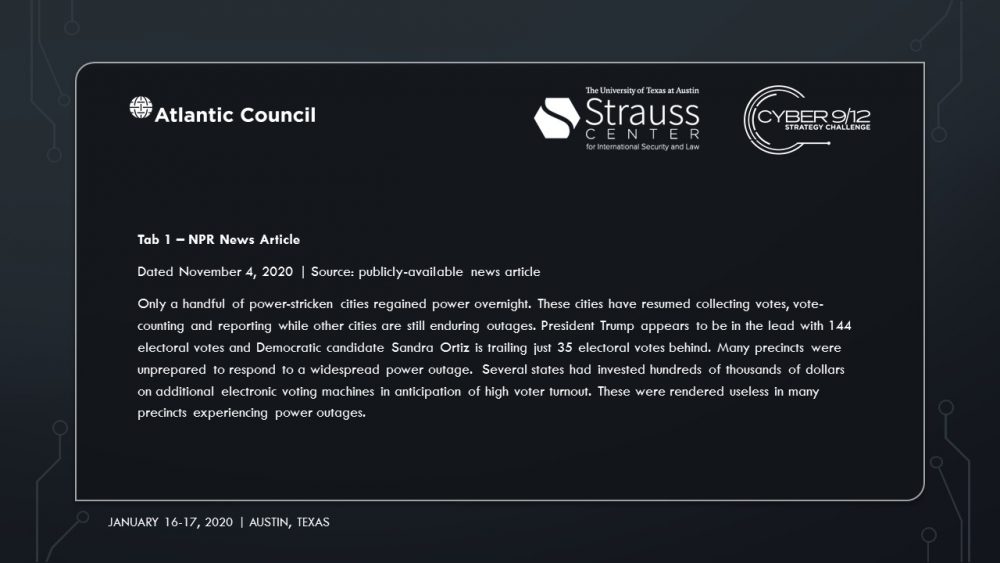
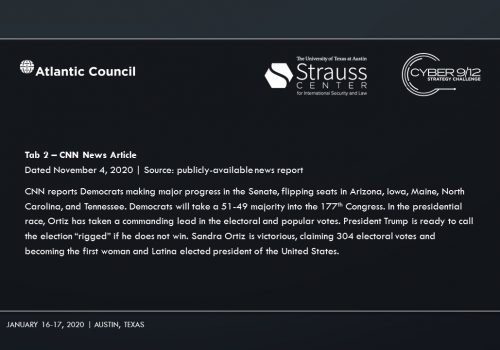
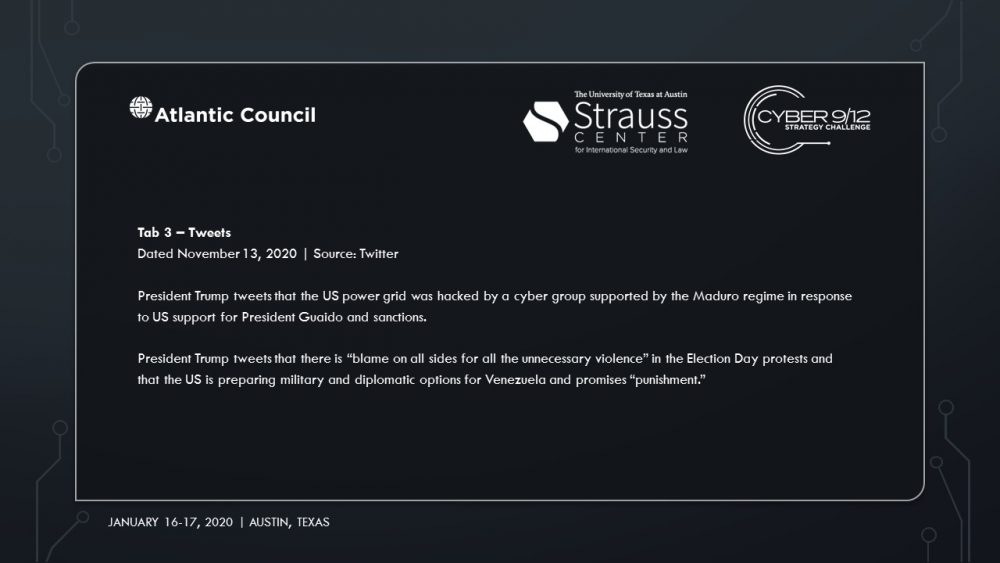
Intelligence Report II makes Sobornost’s involvement in the attacks progressively clear. On November 4, 2020, CNN determines the Democratic candidate, Sandra Ortiz, has won the election over President Trump. Social unrest foments across the US as citizens claim votes were uncounted due to the power outages.
In Intelligence Report III, an NSA investigation reveals the specific plan of attack by Sobornost, leveraging vulnerabilities in the Docks ICS with SCREENDUSTER. The scenario takes an unexpected turn when it is reported that there are traces of SCREENDUSTER in a government computer in Venezuela. The scenario concludes with President Trump suggesting the US take military action against Venezuela for its role in the power grid attack and election interference.
Throughout the three rounds of the competition, students must analyze how they can best A) ensure the security of US critical infrastructure, B) respond to the attack appropriately, and C) restore public faith in the integrity of the presidential election.
Below, we feature the analysis and recommendations of three teams from Lewis University, Texas A&M University, and the US Military Academy. These three teams not only succeeded in advancing to the semi-final and final rounds of the 2020 Austin, Texas competition, but they were also capable of analyzing large swaths of information provided to them by the competition organizers and developed novel and effective policy recommendations.
Find the complete scenario here.
Intelligence Report I
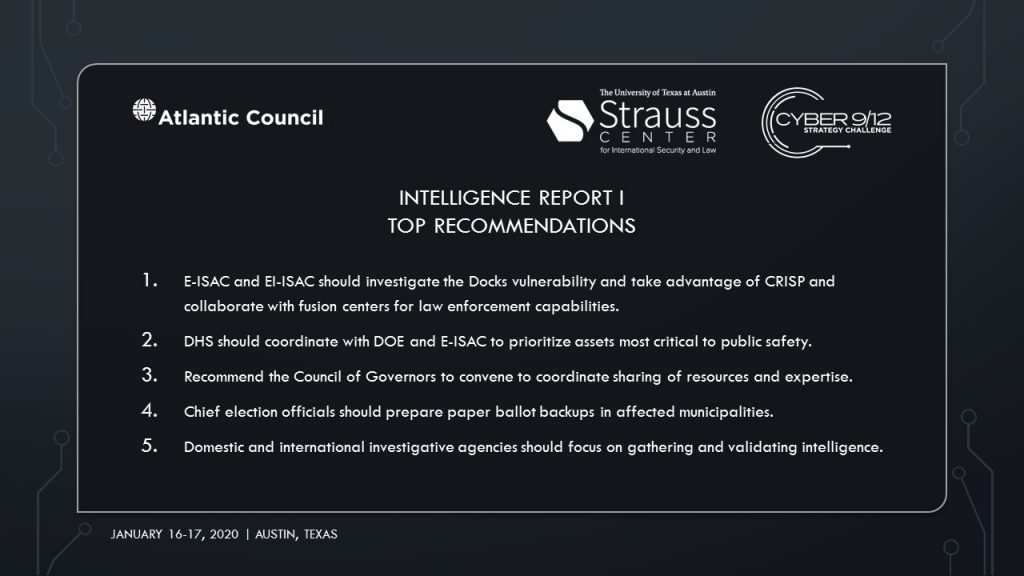
Intelligence Report I Top Recommendations
Intelligence Report I Policy Options

United States Military Academy
Blackjacks
Read Blackjacks’ Intelligence Report I decision document.
Team Blackjacks of the United States Military Academy propose a two-pronged approach, along with three additional policy actions for the National Security Council’s (NSC) consideration. The first of the two prongs, titled “Declaring a “significant cyber incident,” directs the US Department of Homeland Security (DHS) to mobilize the Industrial Control System Cyber Emergency Response Team (ICS-CERT) to coordinate with local authorities to restore power, instructs the Federal Bureau of Investigation (FBI) to investigate power grid interference with the National Cyber Investigative Joint Task Force (NCIJTF), and calls on the NSA for intelligence support.
The second prong, titled “Augmenting the Cyber UCG,” recommends the Council of Governors convene to coordinate sharing of resources and expertise, the NSA execute a Foreign Intelligence Surveillance Act (FISA) warrant to determine if former intelligence officers have disclosed classified information, and enjoin the DHS to coordinate with the Department of Energy (DOE) and Electricity Information Sharing and Analysis Center (E-ISAC) to prioritize protection of critical assets.

Lewis University Flyers
Read Lewis University Flyer’s Intelligence Report I decision document.
Lewis University Flyers recommends the NSC explore one of their four policy options. To understand the threat landscape, cross-agency actions must be taken immediately pursuant to the National Cyber Incident Response Plan (NCIRP). Both domestic and international investigative agencies must focus on gathering intelligence. Additional resources must be directed to the DHS and the DOE for long-term critical infrastructure resilience. And to maintain public order, the president should address the nation to reassure citizens that election integrity was maintained.
The NSC may then either try to de-escalate the situation through international agreements and outreach or launch a retaliatory campaign. For de-escalation, the president will condemn the use of cyber mercenaries, explore options for a re-vote, and establish information-sharing agreements with Russia. For retaliation, the president will instruct the Department of Defense (DoD) and Cyber Command (CYBERCOM) to launch offensive operations against the perpetrators. Using diplomatic leverage, the US Government (USG) will demand Russian cooperation in the election interference investigation. The USG may also choose to deploy economic sanctions and conduct covert operations to prevent future cyber threats.

Texas A&M University Gig’Em
Read Gig’Em’s Intelligence Report I decision document.
Team Gig’Em of Texas A&M University recommends a “policy of restraint” and refrains from retaliatory measures. The proposal calls on the E-ISAC and the Elections Infrastructure Information Sharing Analysis Center (EI-ISAC) to communicate with energy sector and election infrastructure stakeholders. E-ISAC and EI-ISAC will also investigate the Docks vulnerability and bolster information sharing through CRISP and fusion centers.
Chief election officials will assess election integrity, collaborate with ISACs and prepare paper ballot backups. Lastly, a media campaign will be launched to reassure the American public. The Elections Infrastructure Government Coordinating Council (EI-GCC) will be responsible for selecting the spokesperson(s).
Intelligence Report II
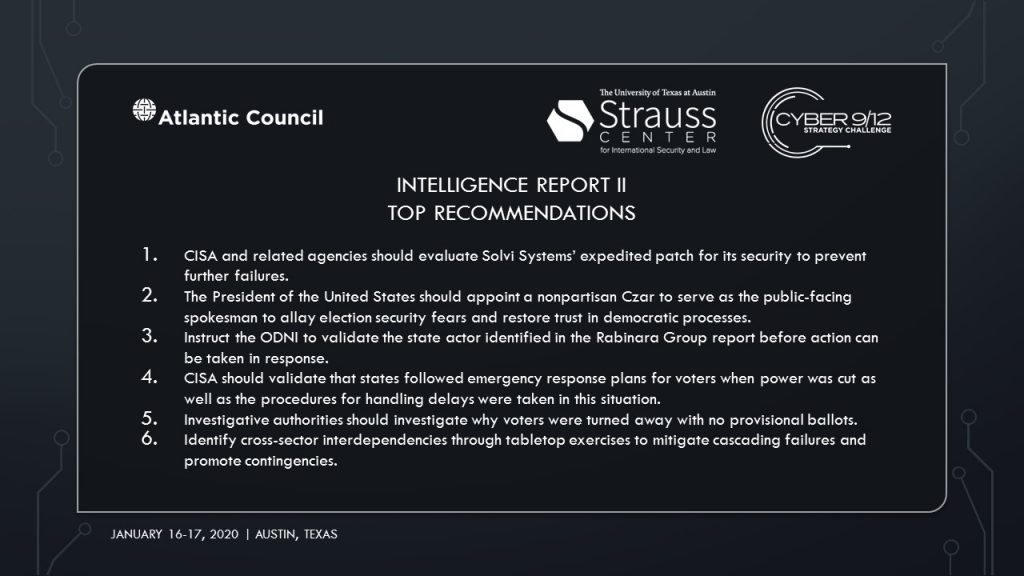
Intelligence Report II Top Recommendations
Intelligence Report II Policy Options

United States Military Academy Blackjacks
Read Blackjacks’ Intelligence Report II decision document.
Team Blackjacks of the United States Military Academy prioritizes three immediate actions: reaffirm the validity of US election systems to ease public tensions, induce the threat actor to cease interfering with democratic processes, and fix endemic critical infrastructure flaws. To coordinate these objectives, a Cyber United Coordination Group (UCG) will be established. DHS will mobilize the ICS-CERT to conduct penetration testing of power grid networks. The FBI will direct the NCIJTF to collect cyber forensics evidence for attribution. The Office of the Director of National Intelligence (ODNI) will direct the Intelligence Community (IC) to provide information to federal agencies to inform local agencies.
To ensure long-term election security, the President will appoint a nonpartisan Czar to serve as the public-facing spokesperson. The Election Assistance Commission should reform current election infrastructure and develop contingency procedures. The government should strengthen public-private partnerships to better defend against adversaries. To deter future attacks, USG should propose new international norms to address ICS attacks and election interference, and levy sanctions on those meddling in US processes. NSA should collaborate with the Five Eyes to collect intelligence and work with CYBERCOM to coordinate cyber defense. Lastly, to bolster critical infrastructure defenses, USG should increase funding for Sector Coordinating Councils (SCCs). DHS should develop flexible emergency communications systems and identify cross-sector interdependencies through tabletop exercises to prevent cascading failures.

Lewis University Flyers
Read Lewis University Flyers’ Intelligence Report II decision document.
The Lewis University Flyers recommend cross-agency actions to delegate response efforts and to maintain public order. DHS will lead asset response according to the NCIRP. The Department of Justice (DOJ) will conduct investigations through the FBI and communicate with the NCIJTF. The Cybersecurity and Infrastructure Security Agency (CISA) will verify whether states followed contingency plans during Election Day blackouts. DHS and FBI will address the ongoing political violence. The DOE should work with CISA to explore long-term critical infrastructure regulatory standards and promote the use of analog failover systems. The ODNI will verify the Rabinara Group’s attribution.
Following those actions, the Secretary of State should condemn the use of cyber mercenaries but withhold attribution until there is high confidence of which state or nonstate actor was responsible. Finally, appropriate resources should be provided to domestic agencies to support the mitigation process.

Texas A&M University Gig’Em
Read Gig’Em’s Intelligence Report II decision document.
Team Gig’Em of Texas A&M University recommends “a position of careful strength,” boiled down to three concrete actions. The FBI, state attorney generals, and state secretaries of state must investigate why voters were turned away with no provisional ballots. They must also investigate the extent of the critical infrastructure damage. CISA, FBI, and CYBERCOM must evaluate the expedited Docks patch to verify its integrity and investigate “Speedy Sloth.” Lastly, election officials, FBI, and state officials must reassure the public by announcing government responses through addresses and social media. The federal government should support the governor of Ohio respond to ongoing violence and coordinate with other governors to prevent further violence.