What is cloud computing?
Cloud computing describes a collection of information technologies (IT) which have reshaped the technology marketplace and the cybersecurity landscape. Cloud computing challenges the certain existing policy consensus as well as traditional political boundaries. Cloud computing providers are more than companies, they are magnificent engines of complexity which govern vast utility infrastructure, society scale datasets, and modern digital battlefields. In competition and cooperation, cloud computing is the canvas on which states conduct significant political, security, and economic activity.
In-depth research
Need some tunes?

Core cloud concepts
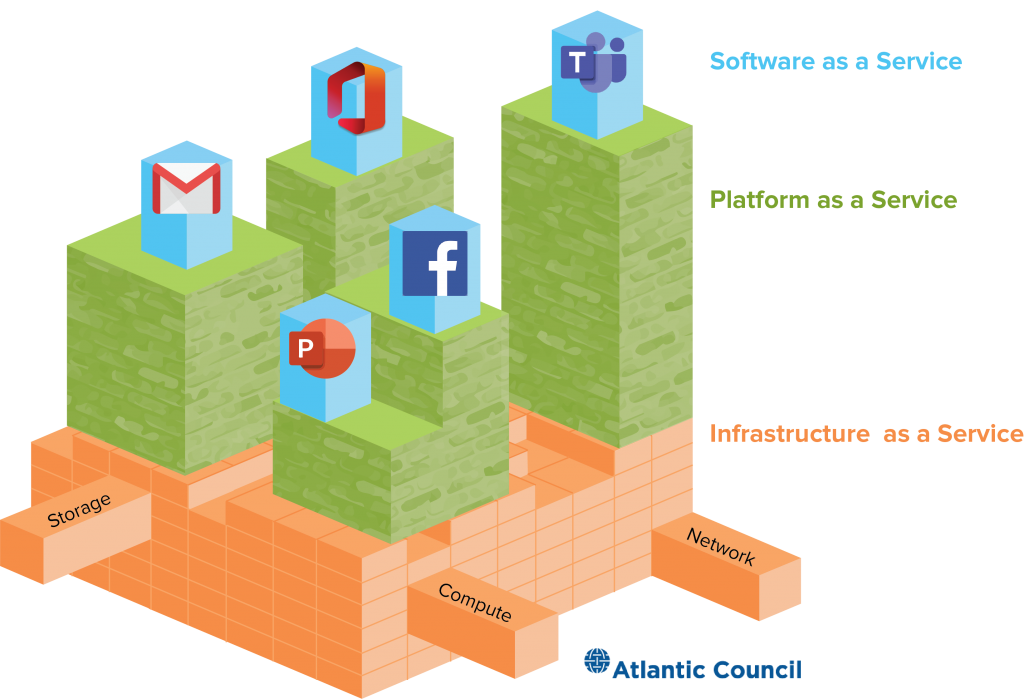
Illustrating cloud service models
Building cloud services looks a bit like assembling Lego blocks. Like a toy store, cloud service providers rent out assorted Lego blocks for users to build customized systems while also offering ready-to-use designs built pre-assembled. At the bottom of this stack of blocks is Infrastructure as a Service (IaaS) which sells the basic computing pieces: storage, processing, network bandwidth, and just enough software to tie them all together. Users have a lot more work to build, maintain, and manage all of these blocks but also get to be much more selective about which blocks they use and where. Platform as a Service (PaaS) sells these prefabricated combinations of blocks in the shape of different computing services—machine translation or tools to process credit card information from point-of-sale systems. These PaaS services provide functionality to software developers and customers looking to connect existing applications to cloud services. SaaS looks most akin to the software you might find on a laptop— word processors, email clients, and chat apps. Cloud providers manage the computing infrastructure and services behind SaaS offerings, giving users comparatively less control or ability to configure but maximum gloss and functionality.
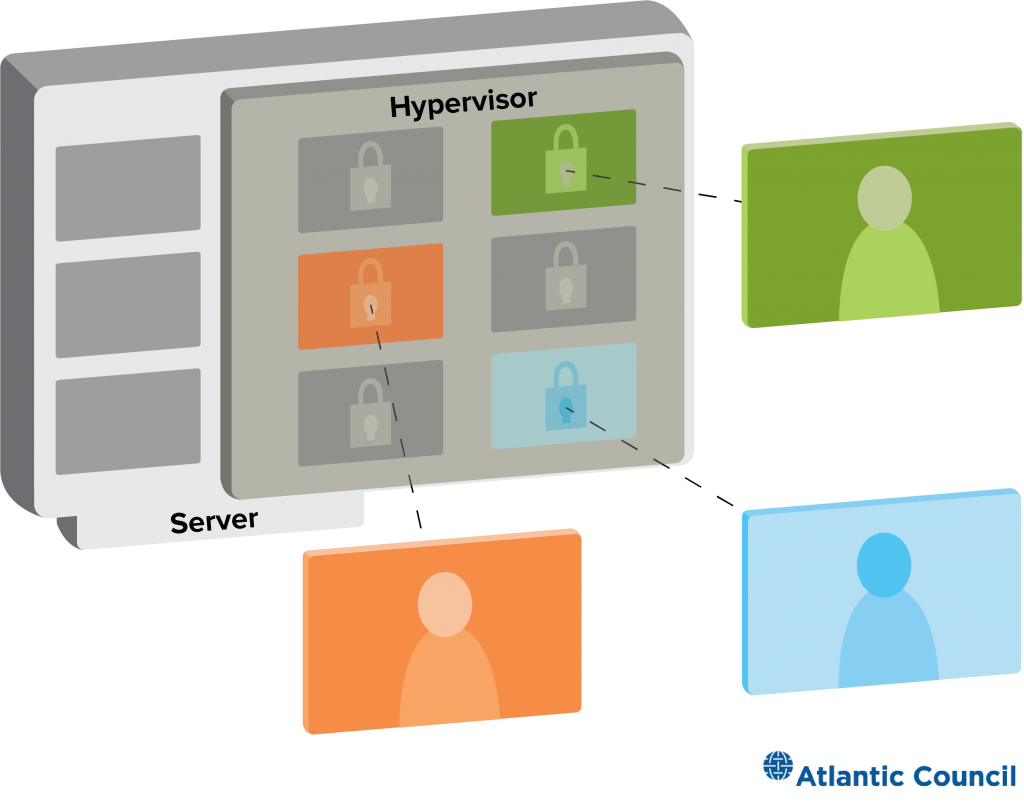
Illustrating the multi-tenant model
At the root of the majority of cloud computing is the shared services model, where many users reside on a single physical machine. Multitenancy is the term used to describe shared use, while the technology that makes it possible is called a hypervisor: software that supervises a computer and divides up its resources—processor time, memory, storage, networking bandwidth, etc.—like cake at a birthday party where every partygoer is blindfolded. Everyone gets to enjoy their slice of cake, unaware of those around them enjoying their own portions, too. The hypervisor keeps each user separate, giving them a turn to use the computer while creating the appearance that each is alone on a single machine. The hypervisor is critical to keeping users isolated from one another. Flaws in the hypervisor software can enable attackers to escape from their slice of the computer into that of other users or, worse, into the host machine’s operating system controlled by the cloud provider.
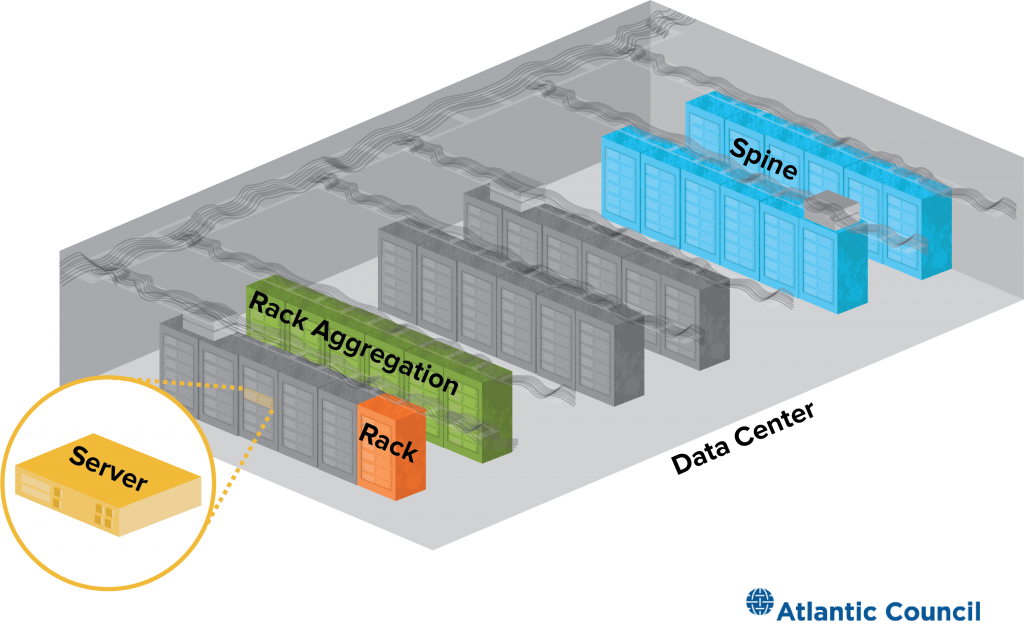
Components of a data center
Cloud services are supported by a network of data centers. Each contains thousands of servers organized into racks, which are collected into spines. At each level, there are multitudinous network connections to minimize the distance (and thus the time) it takes for information to travel from one server to another.
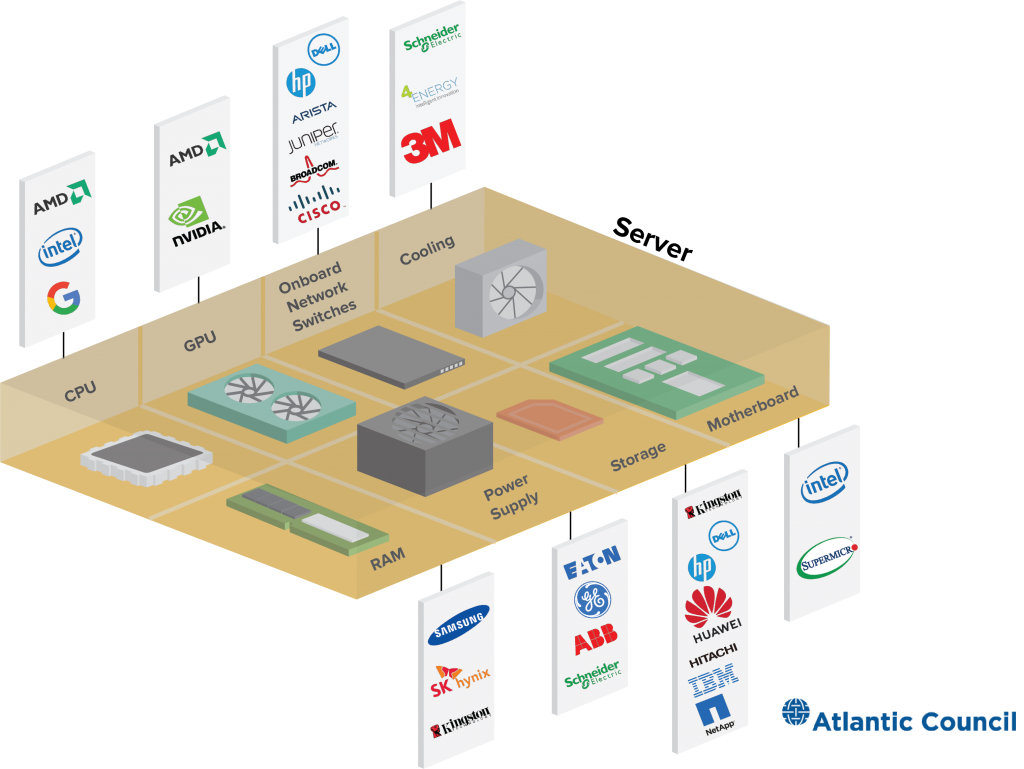
Data center server supply chain
Cloud computing is already a pervasive infrastructure and an important source of supply chain risk. Major cloud providers aggregate the risk from commodity computing and networking technologies by purchasing processors, server boards, networking switches, routers, and more in galactic quantities. Each of these chips, cables, software packages, and servers comes with potential vulnerabilities. Cloud services rely on massive quantities of software, including code developed by third parties and open-source projects.
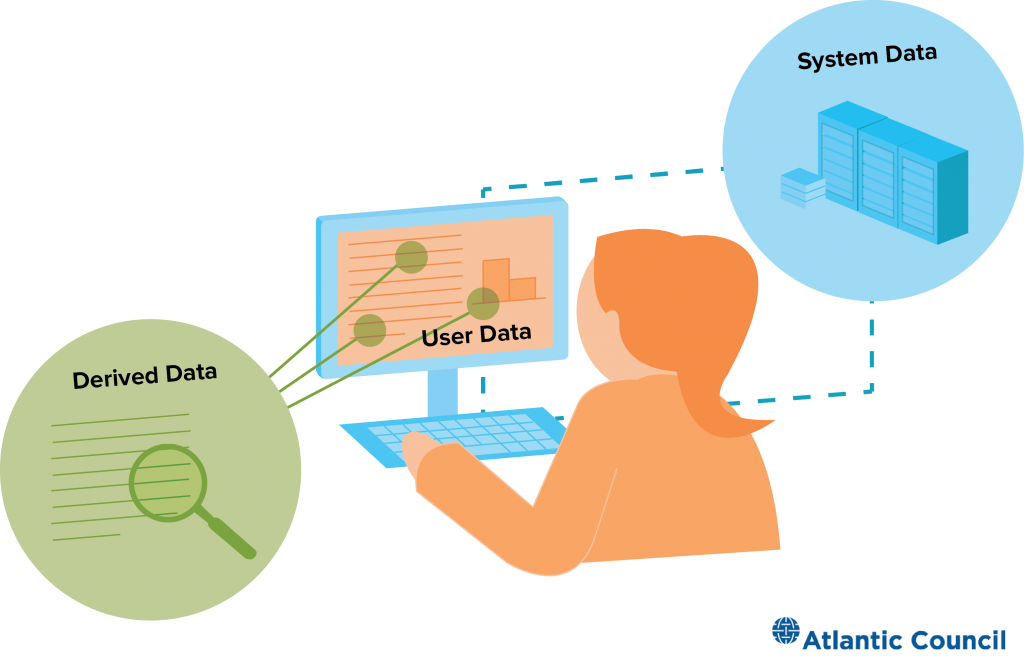
Illustrating data types in the cloud
It is challenging to talk about cloud computing without discussing data. For all its metal and concrete infrastructure, snazzy code, and marketing materials, cloud computing often comes down to managing huge volumes of data. Three categories are helpful:
- User data, what the customers of a service store in the cloud: emails, tax files, design documents, and more.
- Derived data, which allows cloud providers to learn about how users access and interact with these files: which documents do users from an office in Berlin tend to access first and should they be stored nearby to reduce latency?
- System data, or what cloud providers learn about their systems from the way users consume services: what causes a spike in processor utilization or a drop in available bandwidth to a data center or a security alert for malware?
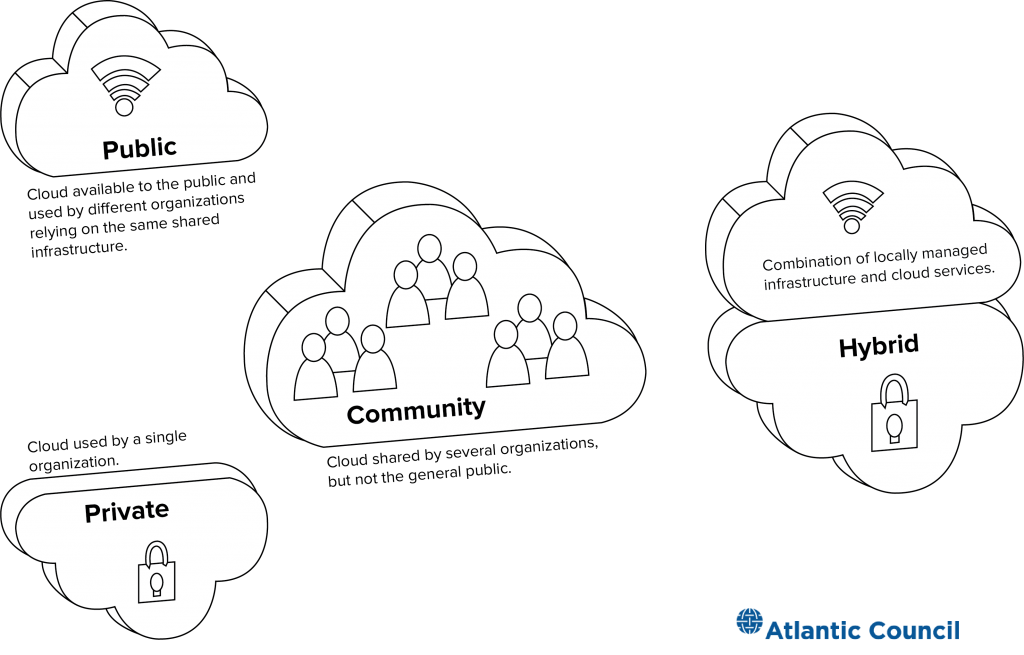
Cloud deployment models
While the public cloud is the most dominant form of cloud computing, there are other deployment models. Private clouds take the same design of infrastructure and management systems but deploy them for only one organization, operated either by the provider or that consuming organization. Community clouds are effectively public clouds whose tenants are users of multiple associated organizations, like Microsoft’s Azure Government—accessible to federal agencies as well as state and local governments but not the private sector. The economics of cloud computing improve as the user base grows, so public cloud deployments tend to have the widest variety of services and the most cutting-edge features. One of the biggest sources of growth in private and community clouds are national security and intelligence agencies, including in the United States and in the UK, as these groups have expressed discomfort with their lack of control over the public cloud’s security standards and inherent multitenancy.

The Atlantic Council’s Cyber Statecraft Initiative, part of the Atlantic Council Technology Programs, works at the nexus of geopolitics and cybersecurity to craft strategies to help shape the conduct of statecraft and to better inform and secure users of technology.