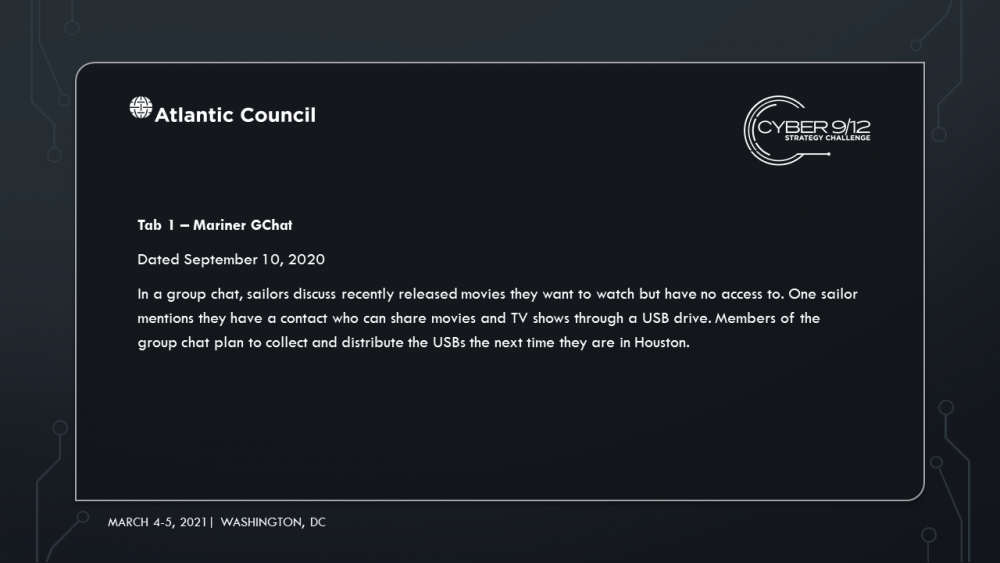
It’s the Pirated Life for Me: Software, Sanctions and the Deep Blue Sea

Scenario Summary
This scenario takes place from February – July of 2021 and focuses on how compromised software supply chains and maritime cyber operations can create economic, humanitarian, and international security crises. The scenario takes place in three acts – the first delivered to students 10 days before the competition commences, the second provided to semi-finalist teams at the end of Day 1, and the third is given to finalist teams 15 minutes before the final round.
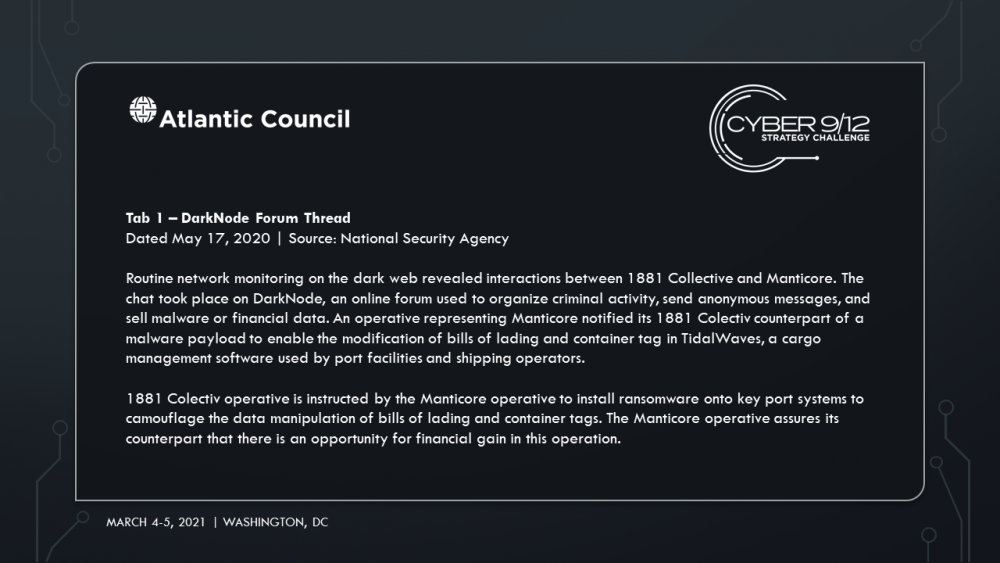
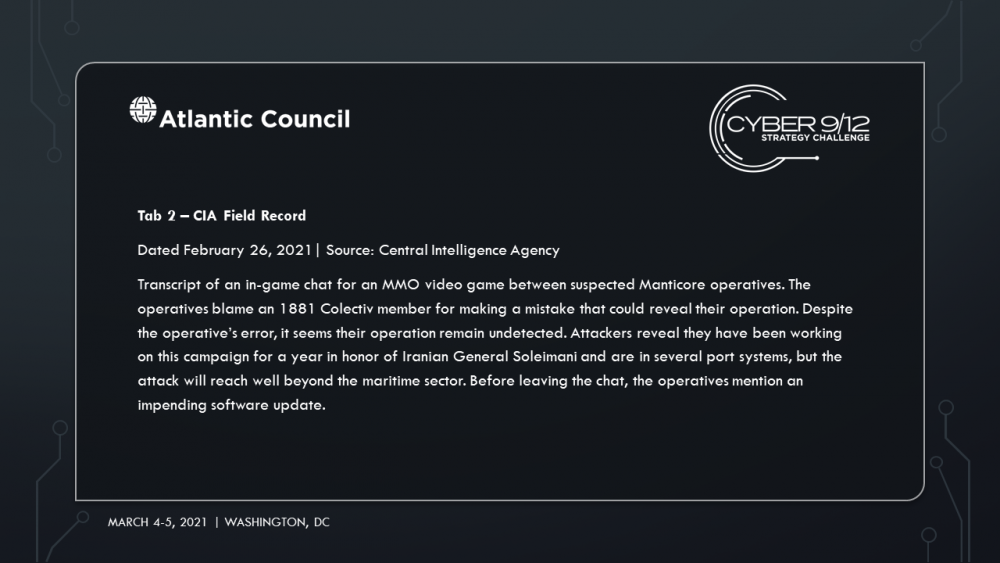
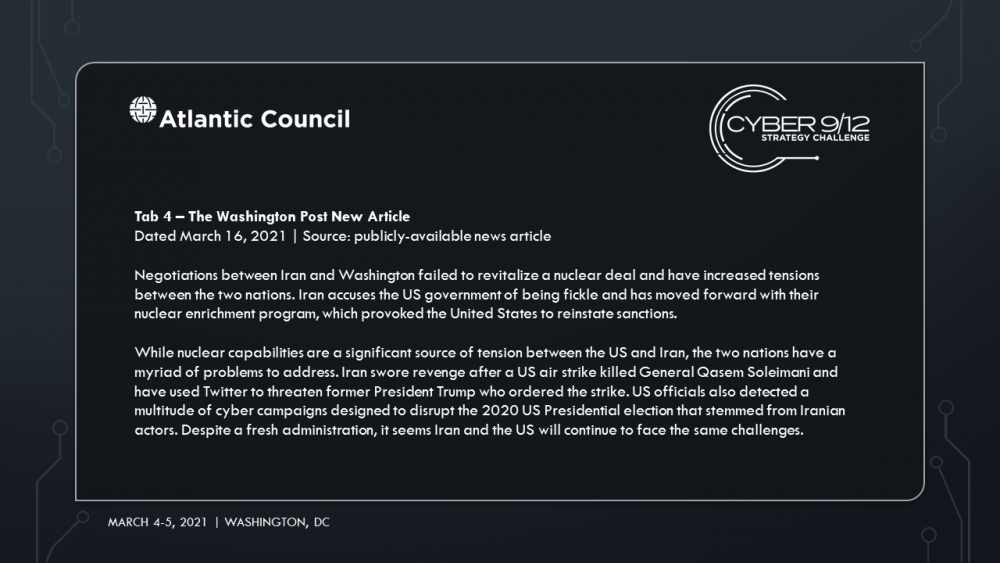
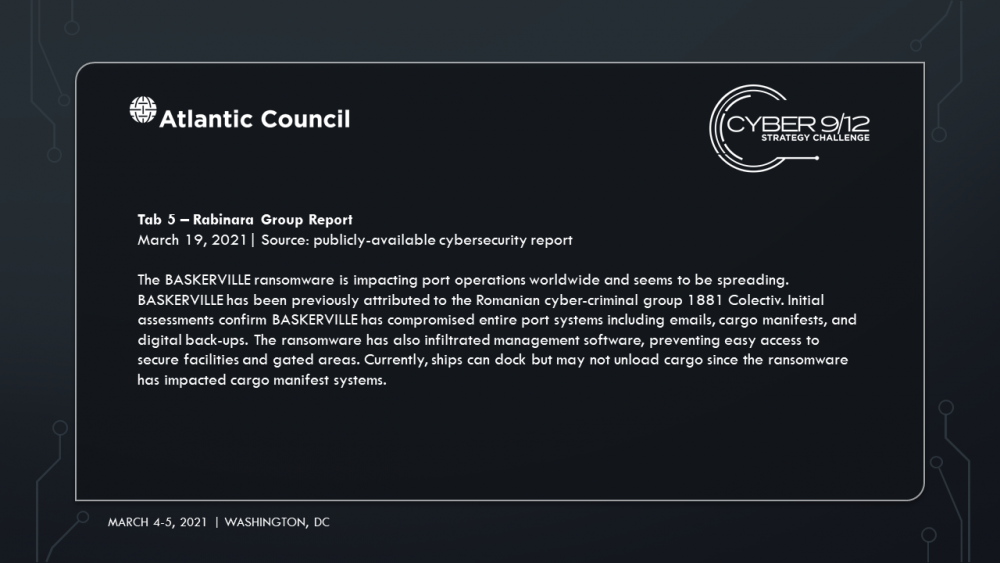
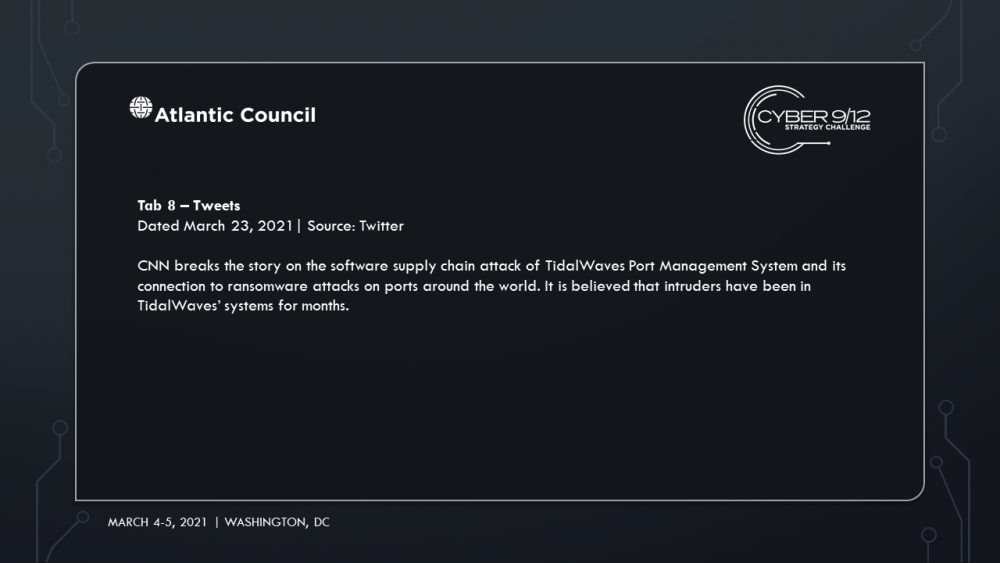
In this scenario, Manticore, a state-backed APT, devised and directed a year-long covert cyber campaign aiming to attack the global shipping and petroleum sectors. The campaign began in January of 2020 in response to the assassination of General Qasem Soleimani but concludes as failed nuclear negotiations between Iran and the United States precipitate new sanctions on Iran. Manticore compromises an open-source library that provides key management software used by major container management software company TidalWaves. Manticore hijacks TaidalWaves’ updates, lacing it with malware that provides them with widespread access to systems, and eventually secure administrator access of entire ports across the world, including the Port of Houston, Port of Corpus Christi and Port of Harcourt in Nigeria. Finally, the group deploys malicious code that will allow them to alter data to modify bills of lading and container tags used by TidalWaves, the container management software.
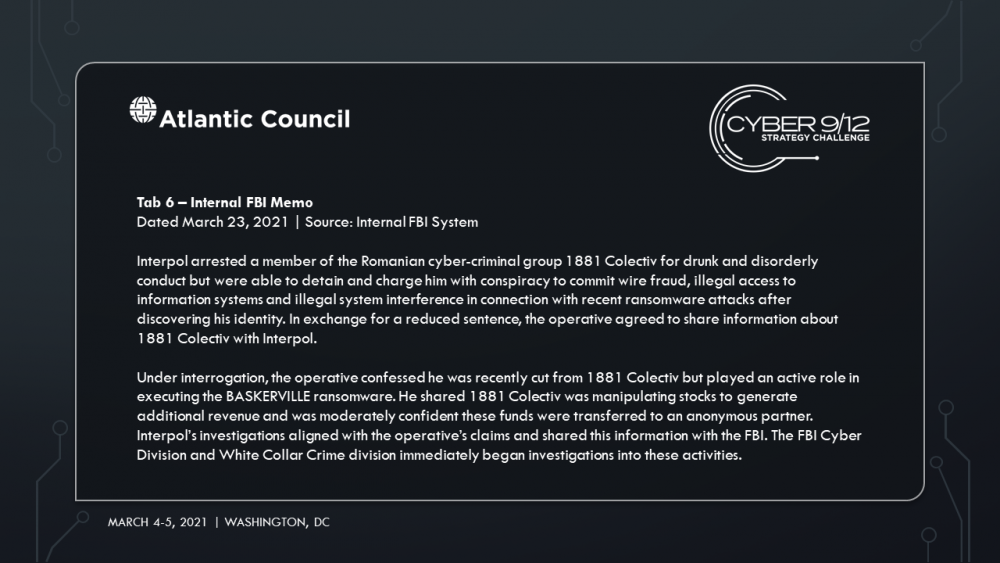
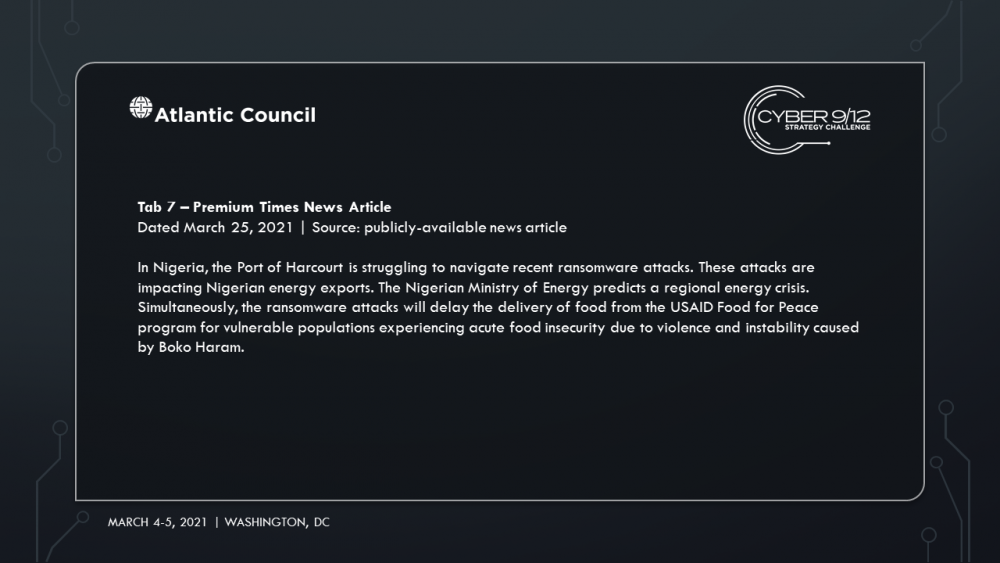
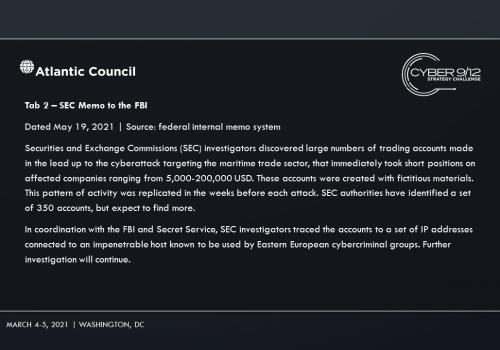
Manticore manipulates data and strategically shorts key stocks before attacks are launched to illicit funds. They hire 1881 Colectiv, to hide their data manipulation and allows them to keep the majority of the ransom. Amid the chaos, Iran subverts sanctions and reroutes critical resources to its shores. Move 1 concludes with a reporter breaking the news of the TidalWaves infection, and increased media concern that infections in the Port of Harcourt could result in a regional energy crisis and food insecurity among vulnerable populations impacted by Boko Haram as food aid shipments struggle to be delivered through the port.
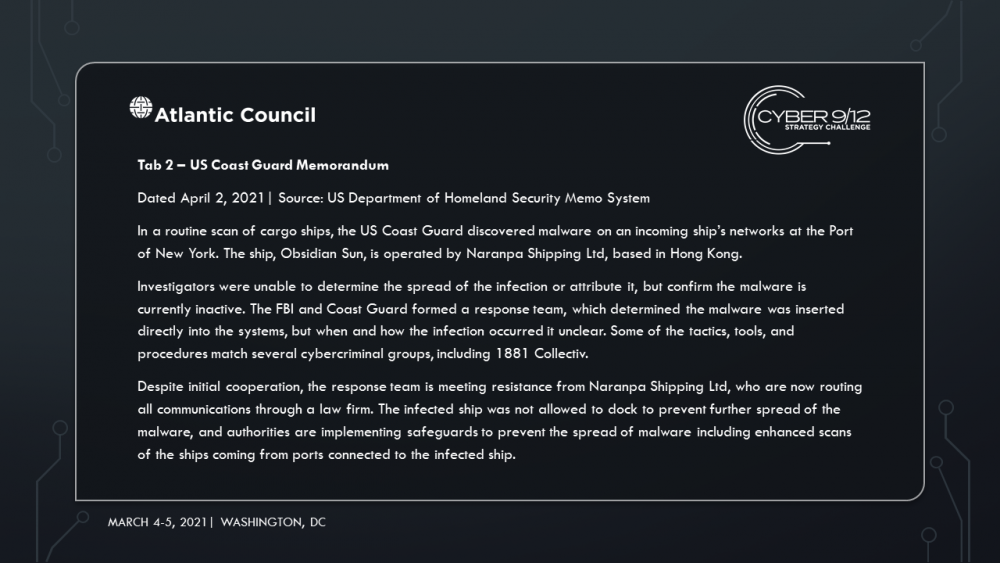
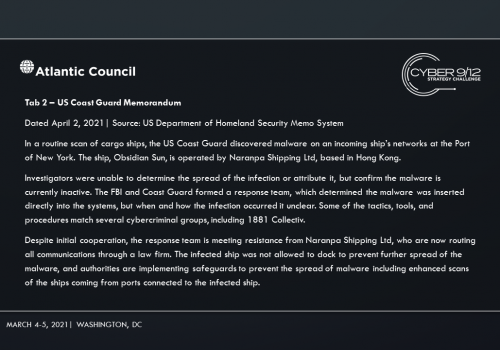
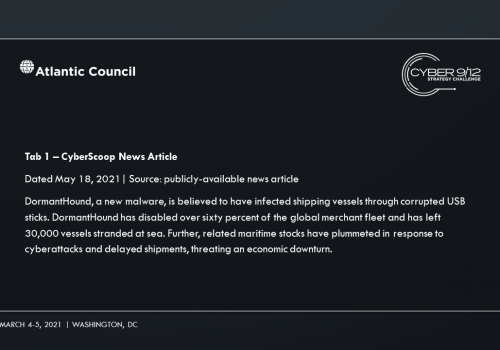
In Move 2, semifinalists learn that 1881 Colectiv developed and distributed DormantHound. DormantHound lays inactive until triggered by 1881 Colectiv’s command and control infrastructure. Once activated, the malware will spread across ships threatening to wipe all data should the campaign be discovered. It is first detected at the Port of New York when a scan of a ship’s systems by the US Coast Guard reveals the malware – at that moment it is unclear as to how many vessels have been infected.
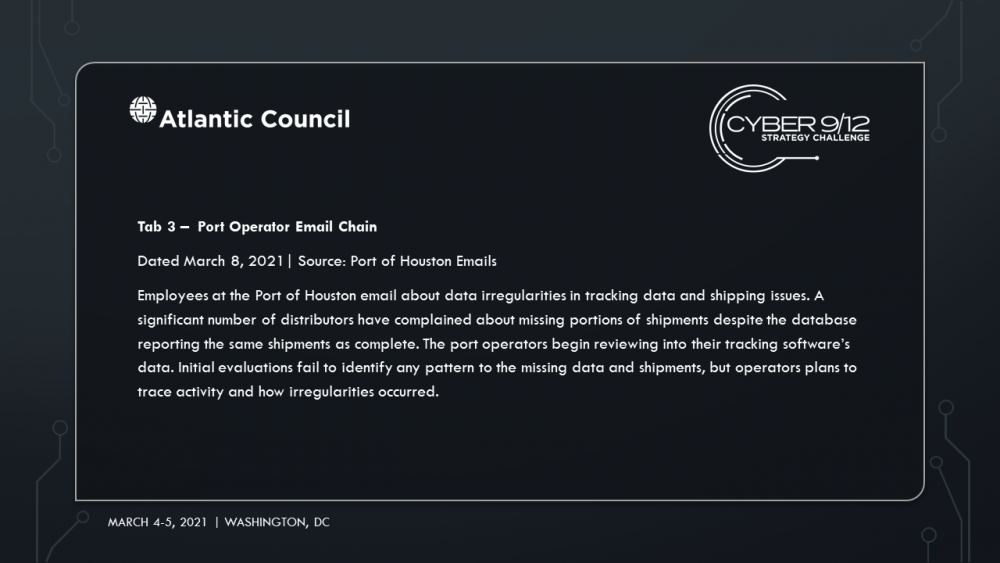
The ransomware attack commences in Port Harcourt as well as in ports in the US and Europe. While it adversely impacts business operations, shipping operations aren’t immediately affected allowing vessels to load and unload cargo. Several customers report that containers have not arrived, despite reassurances from customer service that they did, indeed, arrive.
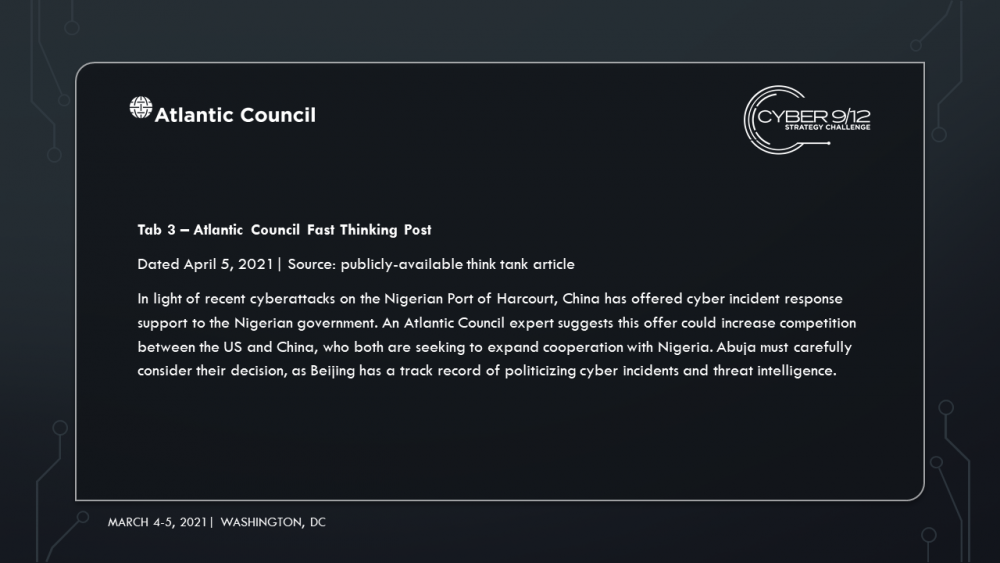
The Nigerian government scrambles to respond to the ransomware on Port Harcourt while local rumors circulate online that the attack was orchestrated by Ghana, an energy competitor in the region who may have attempted to undermine one of Nigeria’s most profitable sectors with its growing cybercriminal element. Facing an impending energy crisis and food shortages across states with vulnerable populations impacted by the Boko Haram insurgency, Abuja considers incident response support offered by the Chinese government. A Chinese DFIR team publicly reports on the breach and highlights an exploit tied back to the 2016 Shadow broker releases. The US political establishment accuses China of politicizing the threat intelligence.
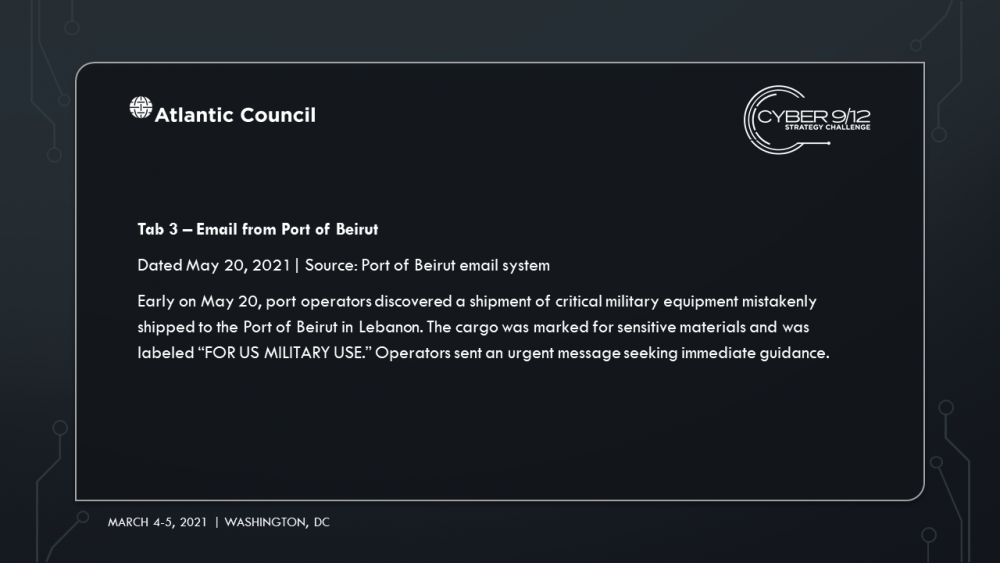
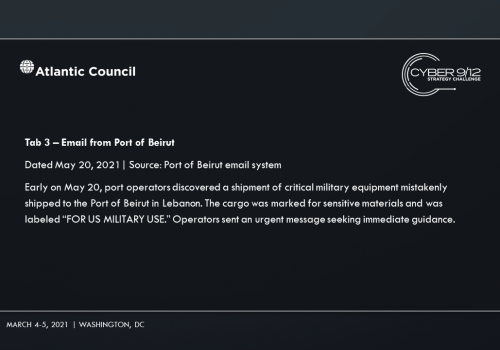
As the ransomware takes down port systems and shipping companies, additional criminal groups look to get involved by leveraging the communication disruption to target major distributors and manufacturers to pay using fake invoices and other low-capability cybercrimes. The secondary attacks are heavily publicized in the press and US defense companies have reported missing containers to the federal government that are attributed to “logistical errors.” The most concerning misplaced shipment is equipment for a surface-to-air missile (SAM) system.
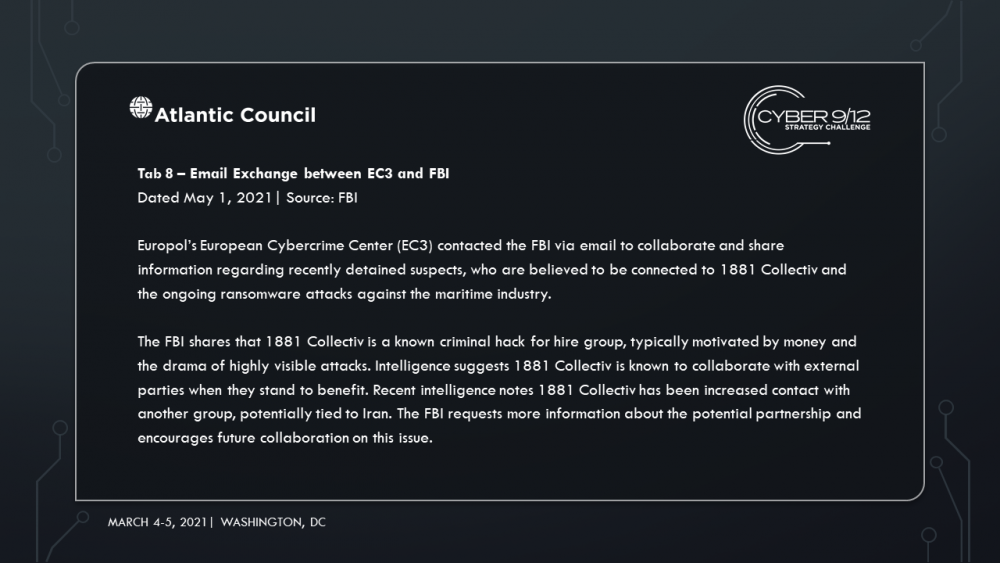
Europol’s European Cybercrime Centre (EC3) arrests a handful of leadership figures from 1881 Colectiv linked to the development and execution of the ransomware attacks. Amidst the arrests, a member of 1881 Colectiv posts the ransomware kit online. Word gets out that the kit is available, resulting in a ransomware free-for-all around the world but especially in Western Africa as criminal groups there continue to use the ransomware to target local offices of US companies while vendors struggle to patch legacy systems.
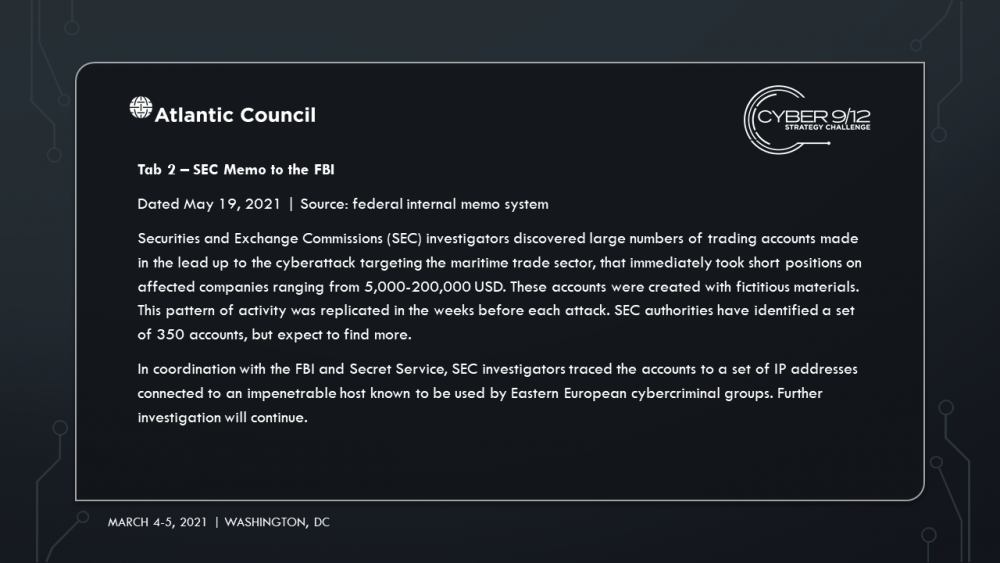
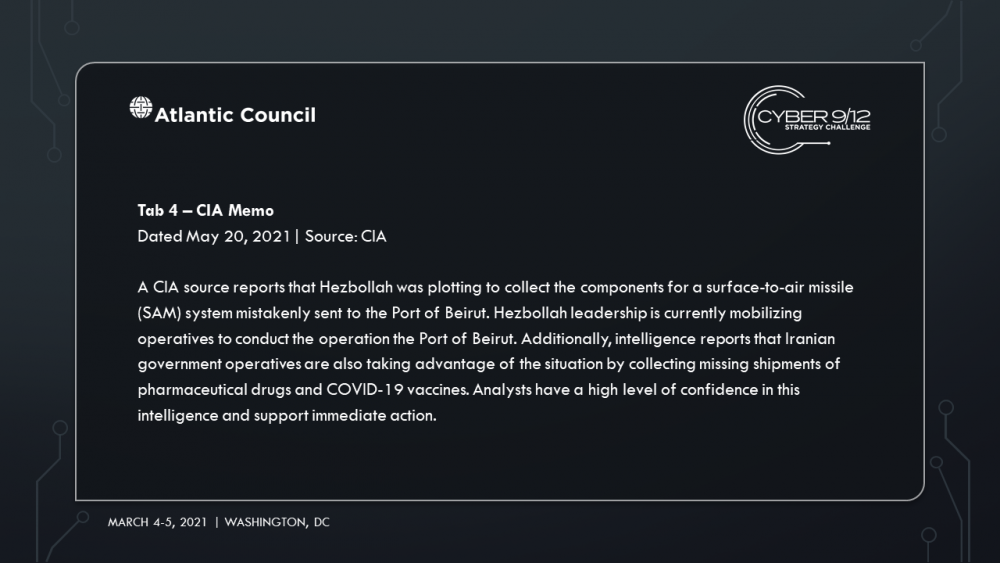
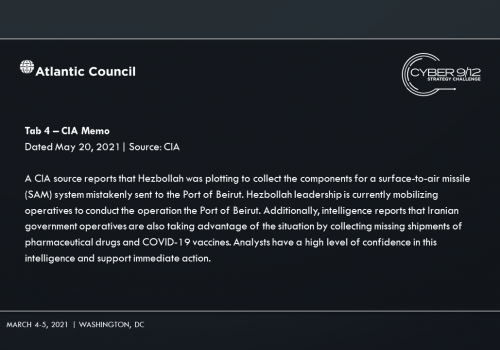
In the final move, competitors learn that several weeks later, DormantHound has been activated knocking 60% of affected ships offline, debilitating the maritime transportation sector and spurring an economic crisis. The various attackers and attribution are revealed through the records of several industrial stocks that were sold short prior to the initial set of ransomware attack disclosures. A freight company is notified of a shipping error of equipment for a SAM system that has been tracked to the Port of Beirut in Lebanon. Intelligence reports that operatives associated with Hezbollah are attempting to collect the equipment.
Students must analyze how they can best A) respond to the ongoing cyber, economic, and security crisis, B) counter China’s support to Nigeria, and C) prevent the missiles from being stolen.
Below we feature the policy analysis and recommendations of a handful of teams who succeeded in advancing to the semi-final and final rounds of the 2021 Washington, DC competition.
Find the complete scenario here.
Intelligence Report I
Intelligence Report I Top Recommendations
Intelligence Report I Policy Options

American University CrtlAltElite
Team members: Evan Gertler, Arsene Frederic Jr., Elizabeth Marge, Christopher Rodriguez-Molina
CtrlAltElite from American University proposed four recommendations that aimed to contain malware, attribute actors, respond multilaterally, and communicate effectively.
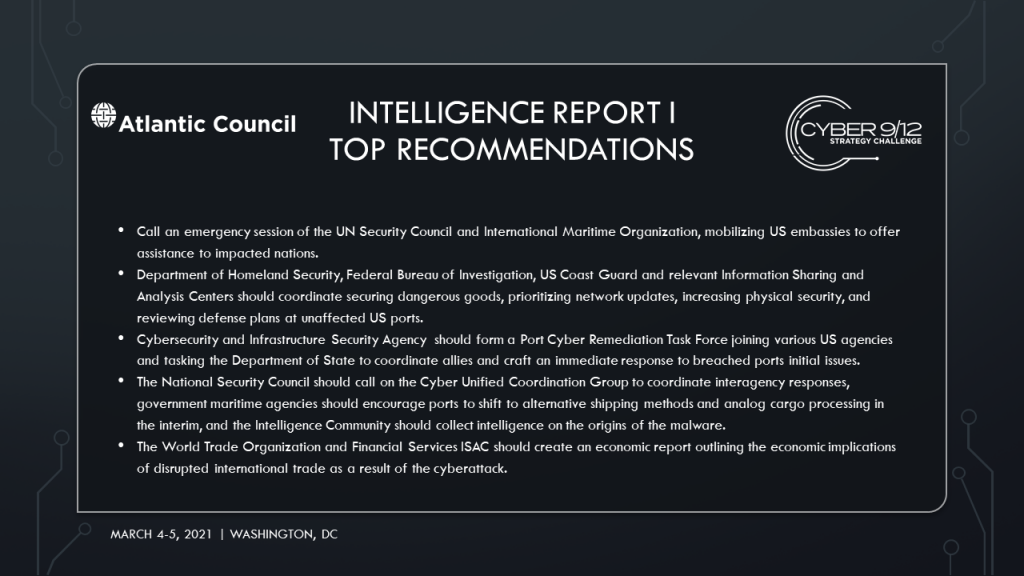
They advised establishing a task force composed of local Federal Bureau of Investigation (FBI) Cyber Task Force agents, Cyber and Infrastructure Security Agency (CISA), Customs and Border Patrol (CBP), Immigration and Customs Enforcement (ICE), the United States Computer Emergency Readiness Team (US-CERT), Maritime Cyber Emergency Response Team (M-CERT) and USCG. The task force will help contain malware at infected ports, urge ports to initiate a Disaster Recovery and/or Business Continuity Plan as needed, and reach out to TidalWaves to identify and notify breached customers. Next, the National Security Council (NSC) should task the Intelligence Community (IC) to investigate the relationship between hackers, find missing cargo, and threat hunt forward into adversarial networks. Additionally, the team recommended calling an emergency session of the UN Security Council and International Maritime Organization, mobilizing US embassies to offer assistance to impacted nations. The final policy recommendation was to ensure effective communication by centralizing communication through the NSC and a designated CISA representative to speak with media outlets.
Read CtrAltElite’s Intelligence Report I written policy brief and decision document.

Columbia University Cyber Knight Riders
Team members: Eli Clemens, Danielle Murad Waiss, Louis Jarvers, Sabrina Otness
Colombia University’s Cyber Knight Riders created six categories of escalating policy recommendations incorporating domestic and international resources to mitigate and prevent further damage. To improve understanding of the situation, the US IC should consult with Five Eyes and other international partners, have the FBI cooperate with ENISA, and collect intelligence from US and International Port Authorities. FBI and CISA should partner with TidalWaves to investigate the extent of the intrusion and collaborate technical mitigation. Various offices in DHS, FBI, USCG and relevant Information Sharing and Analysis Centers (ISACs) should coordinate securing dangerous goods, prioritizing network updates, increasing physical security, and reviewing defense plans at unaffected US ports. Threats to the energy supply and transportation capabilities must also be reviewed and secured by the Department of Transportation (DOT) and Department of Energy (DOE).
Two higher risk policy options recommend 1) initiating cooperation with European allies to disrupt the cybercrime group and assess reinforcement mechanisms to Iran for potential future use, and 2) task USCYBERCOM to assess disruption and preemptive defense options through Defend Forward/Persistent Engagement hard evidence.
Read Cyber Knight Riders’ Intelligence Report I written policy brief and decision document.

New York University NYU Cyber
Team members: Amanda Tobey, Elisa Fox, Hallie Stern, Lorenz Cohen
NYU Cyber offered three levels of policy recommendations, but suggested government officials move forward with their mid-level policy package titled “Bravo.” The Bravo policy package aims to mitigate the impact on shipping, contain the malware, and investigate the origins of the attacks. It includes five specific actions assigned to actors across the US government and private sector. As a baseline, the NSC should call on the CUCG to coordinate interagency responses, government maritime agencies should encourage ports to shift to alternative shipping methods and analog cargo processing in the interim, and the IC should collect intelligence on the origins of the malware. After these initial actions, the USCG should deploy officers to manage maritime traffic while the IC investigates missing goods. At the technical level, NYU Cyber recommended tasking US-CERT and contractors to develop initial software patches for infected ships and ports, have CISA suggest cyber hygiene changes for ports, and leverage a Federally-Funded Research and Development Center (FFRDC) to research distributed ledger technology.
Read NYU Cyber’s Intelligence Report I written policy brief and decision document.

Tufts University FSociety
Team members: Matthew Brophy, Jackie Faselt, Katy Mayerson, Andrew Seligson
F-Society presented a two-pronged policy response with escalating long and short-term options to respond, reinforce and retaliate against adversaries. This framework mobilizes a whole-of-government approach and recommends the NSC initiates the CUCG to lead and coordinate the escalatory framework. CISA should form a Port Cyber Remediation Task Force joining various US agencies and tasking the Department of State (DOS) to coordinate with allies and craft an immediate response to breached ports initial issues. In the longer term, CISA and MTS-ISAC will lead US port reinforcement though a coordinated information-sharing and protect additional infrastructure. Initial remediation efforts should be led by DOJ and will impose financial and legal costs on the cyber threat actors.
Read FSociety’s Intelligence Report I written policy brief and decision document.

Utah Valley University W0LV3R1NES
Team members: Mark Driggs, Alex Heitzmann, Andrew Jensen, Hunter Karr
Utah Valley University’s W0LV3RINES crafted national and international policy recommendations with escalatory contingency plans. At the national level, the FBI, DHS, and other IC agencies should coordinate immediate intelligence gathering on infected US ports, and prioritize intelligence collection on suspected cyber adversaries, with the option to involve international partners. CISA should 1) issue reports to the MTS-ISAC, 2) deploy and operate technology for affected parties and offer mitigation protocols to other entities. Additionally, the FBI should establish and lead a national cyber taskforce that includes staff from the infected ports, academic experts, and MTS-ISAC representatives in accordance with the Cyberspace Solarium Commission. Internationally, DOS and CISA should immediately establish international lines of communication with partners and create an international taskforce with all impacted ports worldwide. To address the economic implications of disrupted international trade, the World Trade Organization (WTO) and Financial Services ISAC (FS-ISAC) should publish an economic report outlining the impacts of the cyberattack.
Read W0LV3RINES’ Intelligence Report I written policy brief and decision document.
Intelligence Report II
Intelligence Report II Top Recommendations

Intelligence Report II Policy Options

American University CtrlAltElite
In response to the escalating situation, CtrAltElite developed an array of policy solutions for immediate, near, and long-term action. The first set of recommendations focuses on containing malware by scanning all commercial and military port and ship systems for indicators of compromise, engaging private-sector security firms to assist in technical investigation and forensic analysis of port breaches and activating Army National Guardcyber units to assist in active defense of port networks. Next, the IC must investigate the cyber adversaries and missing military equipment, and request FBI presence at Europol interviews of cyber operatives in order to improve attribution. Internationally, US embassies should be directed to offer US assistance to impacted nations’ ports and instruct Central Intelligence Agency (CIA) and National Geospatial-Intelligence Agency (NGA) to coordinate the ongoing shipping surveillance operations with Five Eyes partners.
To enhance multilateral cooperation, the US should propose “Baskerville Resolution” in the UN IMO aimed at updating maritime security frameworks to include cybersecurity. Finally, to ensure effective communication the executive branch was tasked to 1) form a panel of US government officials from impacted sectors to hold a press conference on the attack’s implications, 2) disseminate technical findings through the M-ISAC, MTS-ISAC, MPS-ISAO and VirusTotal, and 3) engage Nigeria and Ghana to mitigate security concerns and support their recovery.
Read CtrlAltElite’s Intelligence Report II decision document.

Columbia University Cyber Knight Riders
The Cyber Knight Rider’s determined the escalating crisis called for the creation of “PORTSIDE,” a temporary interagency working group, with members from the FBI, USCG, National Cybersecurity and Communications Integration Center (NCCIC), Office of the Director of National Intelligence (ODNI), Corporate Office Properties Trust (COPT), port operators, and MTS-ISAC. Meanwhile, CISA will coordinate with affected ports, TidalWaves, and PORTSIDE to ensure physical and cyber security of systems. The Department of Defense (DOD) and Department of Homeland Security (DHS) will search for missing goods and assess current shipments, and communication. Federal Emergency Management Agency (FEMA) should support these efforts by granting emergency funds to protect ports against physical attacks, partnered with the deployment of the National Guard to secure ports. Port authorities must prioritize shipments, track ships from affected ports, isolate infected ships, remove malware in order of national priority. To protect the economy, the Departments of Treasury and Energy must secure US oil and energy supplies, prepare monetary and fiscal policy options for potential supply chain shocks, and coordinate with the comptroller to ensure price and financial stability.
Looking abroad, DOS should ensure US support of Nigerian government, identify shipment re-routes, and address Romania, European Union and NATO for cooperation on investigation and disruption of cybercrime groups. Finally, the government must issue a public statement outlining the ongoing situation and government actions, followed by updates on US response and mitigation to ensure the American public is well informed.
Read Cyber Knight Rider’s Intelligence Report II decision document.

Tufts University FSociety
FSociety recommended relying on the interagency Port Cyber Remediation Task Force they established in round one to partner with the International Maritime PPP to immediately respond to new crisis developments. In the short term, they recommended the IC partner with international intelligence allies to collect intelligence on the urgent threats. To reinforce security and retaliate in the long-term, FSociety presented two policy strategies for decisionmakers to follow or create a hybrid solution. Option one tasked CISA, US-CERT and DOS to reinforce infrastructure resiliency and create a response center, while USCYBERCOM, National Security Agency (NSA), and NATO created a multi-domain countermeasures retaliation plan. The second option recommended CISA and National Institute of Standards and Technology (NIST) partner with State and local agencies to reinforce the infrastructure hygiene initiative, while the DOT, NSA, and DOJ worked with INTERPOL and EUROPOL to launch an international cybercrime takedown campaign.
Read FSociety’s Intelligence Report II decision document.

New York University NYU Cyber
NYU Cyber recommended their “Bravo” policy package which combines baseline cross-government action with responses to match the elevated threats. To begin, the CUCG must brief the NSC, the MTS-ISAC and US Maritime Administration (USMARAD)
will promote the switch to analog cargo processing, the FBI and INTERPOL will investigate the origins of the actor behind this incident and missing goods, while CISA manages communications plans and Countering Foreign Influence Task Force (CFITF) counters the disinformation campaign. Other fundamental actions include the President calling the leaders of involved countries to support diplomatic actions, and task an FFDRC to research distributed ledger technology and updated cyber hygiene for ports.
After these actions have been completed, the team recommends mobilizing the Navy and Air Mobility Command to secure critical goods and patrol ships. On the technical side, CISA will issue a bug bounty, international Computer Security Incident Response Teams (CSIRTS) and contractors will develop a patch, and USCYBERCOM will engage will allies to Defend Forward. To defend the economy, the Securities and Exchange Commission (SEC) will suspend trading on specific stocks and the World Bank will assist impacted developing economies.
Read NYU Cyber’s Intelligence Report II decision document.

Utah Valley University W0LV3R1NES
Utah Valley University’s W0LV3R1NES recommended short-term and long-term policy responses with escalatory contingencies. First, the Unified Coordination Group should be established to coordinate between government and private sector as they investigate and respond to the cyberattacks. CISA should partner with a research agency to provide the victims of the cyberattack with effective mitigation strategies and workarounds for impacted systems. Next, the CIA and NGA should be tasked with working with impacted US defense contractors to resolve issues with missing missile components. Meanwhile, the DOJ and FBI should prepare to indictment members of 1881 Colectiv while working to establish clear attribution. Finally, the DOT should establish domestic economic damage assessment caused by the attacks.
Looking ahead, the USCG and USMARAD must monitor tracking systems to identify and track ships corrupted with malware. Additionally, impacted companies should coordinate with CISA and the FBI to ensure proprietary sensitivity as they initiate a full launch of the software patch. CISA will also be tasked with sharing the adversaries’ TTPs to mitigate further spread of the ransomware, and partner with the DOS to prepare cyber assistance recommendations for a Nigerian assistance package. Finally, the US will partner with the United Nations Humanitarian Air Service in Nigeria to deliver United States Agency for International Development (USAID)shipments and mitigate further damage.
Read W0LV3R1NES’ Intelligence Report II decision document.
Intelligence Report III
Intelligence Report III Briefings
Utah Valley University W0LV3R1NES
Columbia University – Cyber Knight Riders
Tufts University – FSociety
Intelligence Report III Top Recommendations