A Disaster to Entertain Poseidon and Ruin Christmas

Scenario Summary
This scenario takes place from October – December of 2022 and focuses on maritime cybersecurity and how non-state actors can sow chaos and congest critical shipping lanes with severe global economic ramifications. The scenario takes places in three acts – the first delivered to students 10 days before the competition commences, the second provided to semi-finalist teams at the end of Day 1, and the third is given to finalist teams 15 minutes before the final round.
The scenario proceeds through a series of escalating security events with challenging political constraints on response (Chinese partners on incident response, uncoordinated vulnerability mitigation, and interagency confusion over lines of responsibility). It concludes with the discovery of a state actor exploiting the chaos to ship a do-it-yourself dirty bomb kit through the impacted region to a distant buyer.
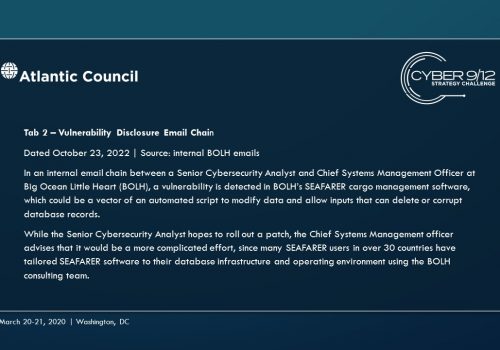
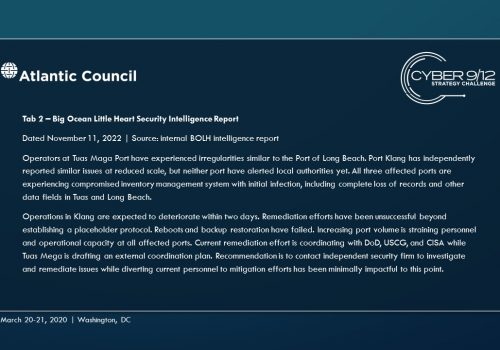
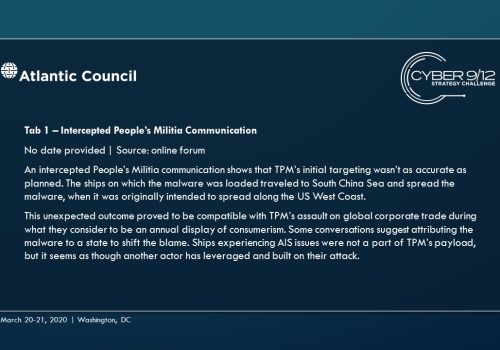
The principle antagonist is a non-state group based in the United States called The People's Militia (TPM), a call back to the same group active in the 2019 New York Cyber 9/12 Strategy Challenge Scenario. In this scenario, the main cyber capability employed by TPM is a piece of malware targeting manifest record keeping systems, starting on two ships managed by private firm Big Ocean Little Heart (BOLH). This malware compromises the integrity of inventory databases, wiping them in whole or in part and using leave-behind ransomware to frustrate efforts to restore from backup. The malware spreads from ships to ports with the manifest record keeping systems as the main infection vector. Over time, this malware begins to spread to other systems at the affected ports.
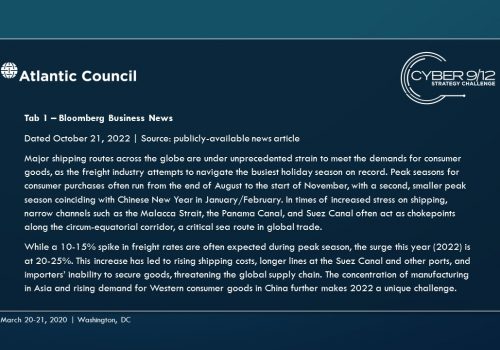
The early injects focus on establishing the current economic importance of the Strait of Malacca chokepoint and reintroducing TPM as an actor. We use a series of news articles to demonstrate that the lead up to the holiday season is a particularly busy time for shipping in the region as global shipping volume skyrockets. Using an interview recording with The People’s Militia’s leader and view into an encrypted web forum discussion, we establish how the People’s Militia has expanded both the focus and scope of their operations, detail their basic ideology, and explain why they have become acutely interested in developing and utilizing offensive cyber capabilities.
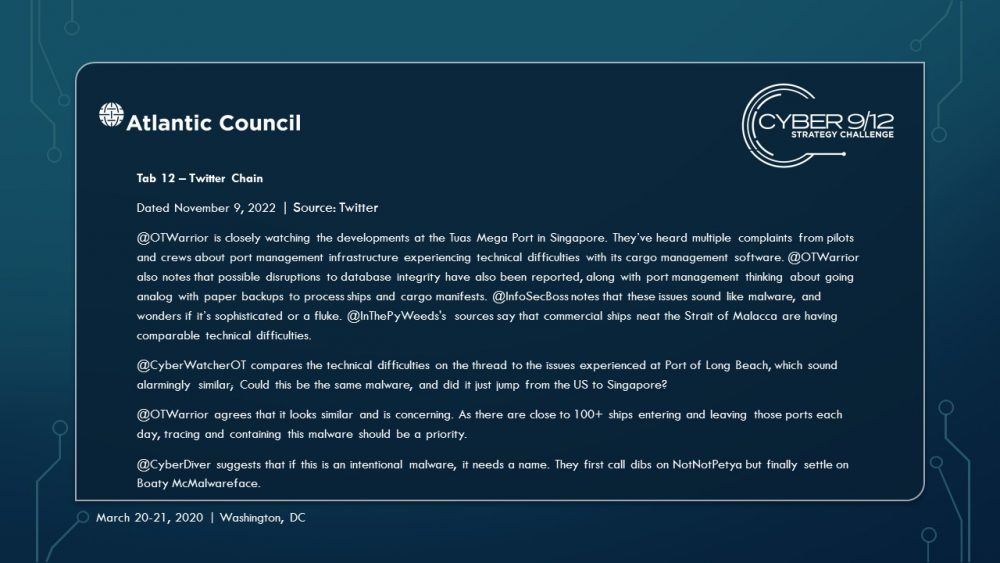
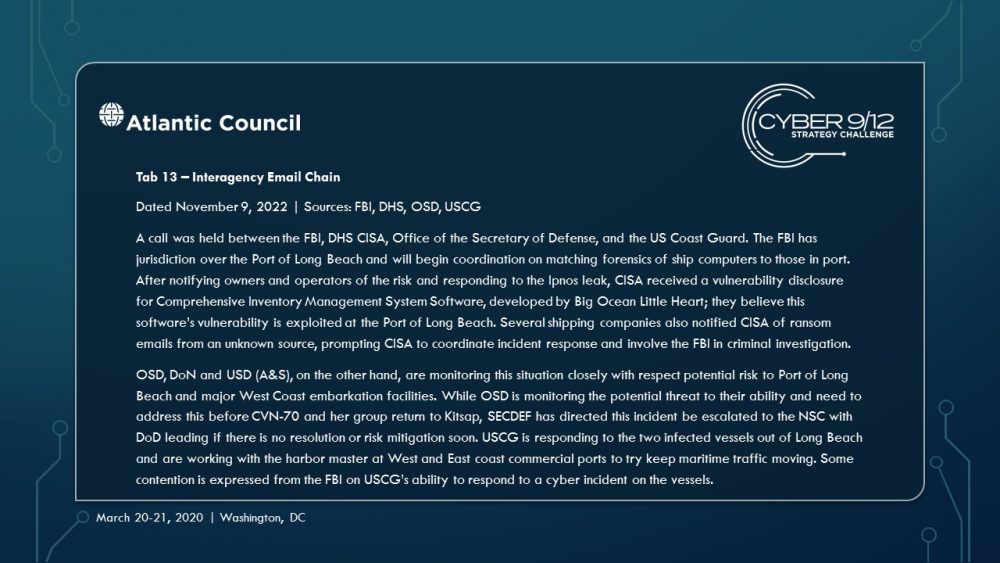
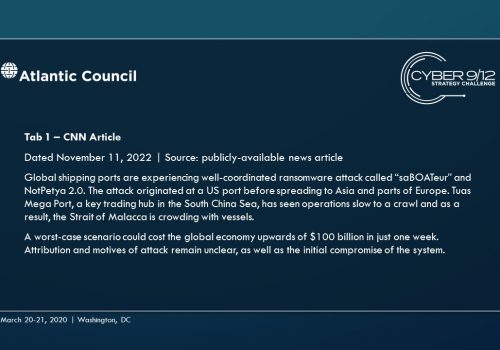
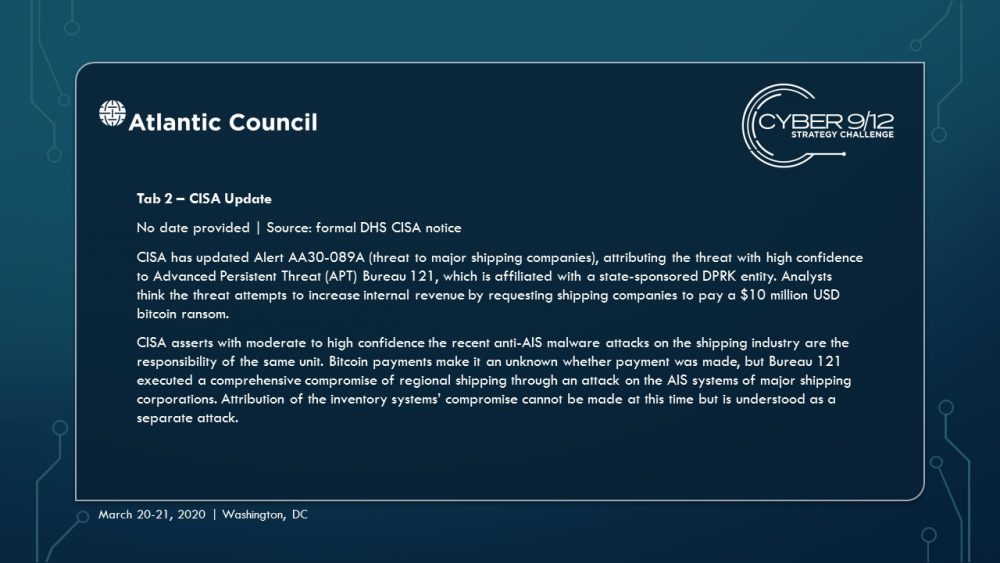
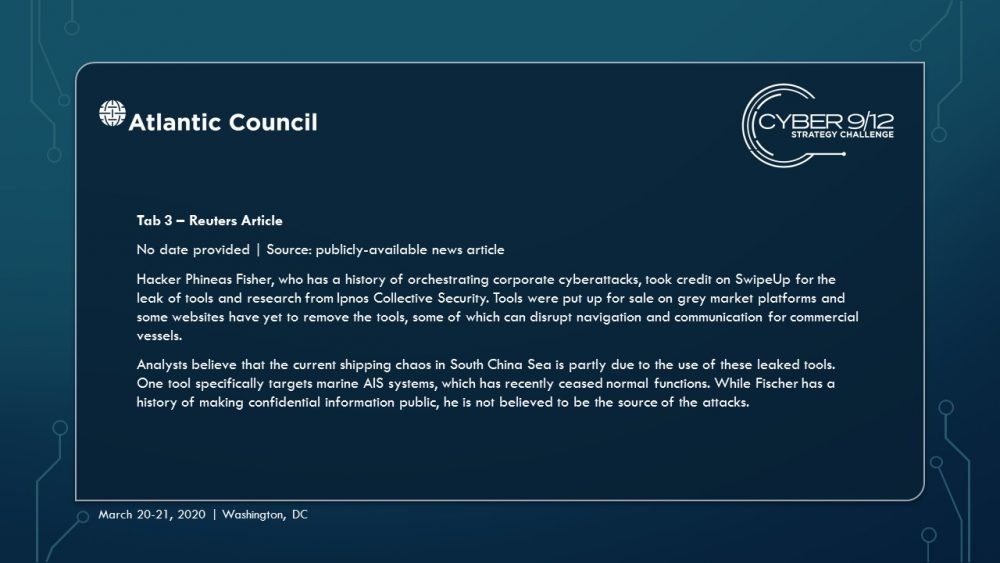
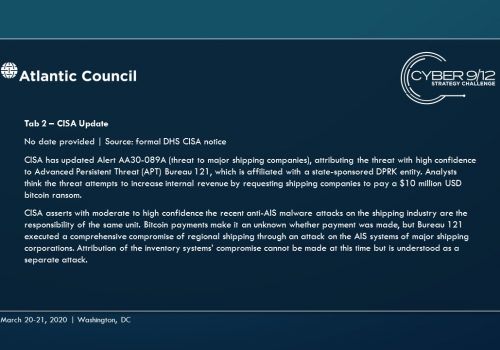
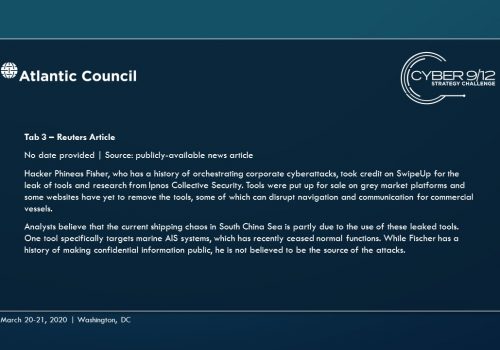
Move 1 concludes with several important developments. First, a currently unknown actor – North Korea – blackmails several commercial shipping firms with the supposed “capability to wildly disrupt and destroy your navigation capabilities.” Concurrently, a well-known hacktivist leaks a suite of offensive maritime cyber tools and research focusing on maritime cybersecurity. Finally, the initial effects of TPM’s malware begin to manifest, raising questions within the US Government (USG) about how to respond and who should lead this response.
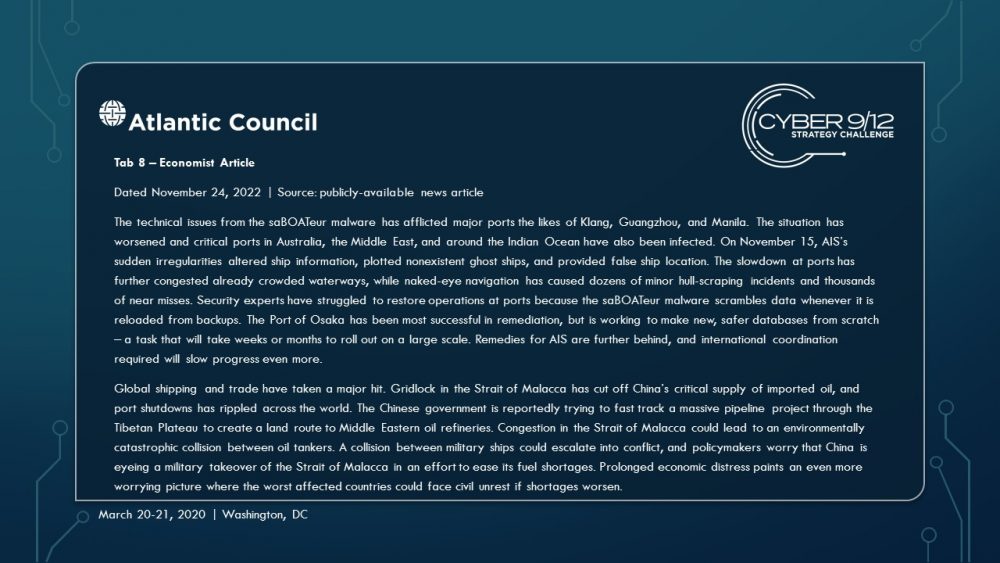
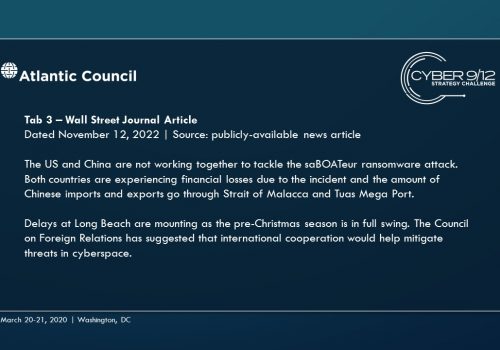
As the effects continue to spread throughout the global port network as these ships travel across the region to the South China Sea (the malware spreads organically), international trade slows, causing global economic harm. Attempts to resolve the effects of the malware triggers leave-behind ransomware in several systems, severely complicating and obstructing incident response. These effects are compounded by a simple but disruptive attack on the integrity of data from the Automatic Identification System (AIS), executed by North Korea using the leaked tools from the maritime cybersecurity firm, which further complicates navigation and forces manual watch standing in major shipping lanes particularly the Strait of Malacca, which have already grown immensely congested.
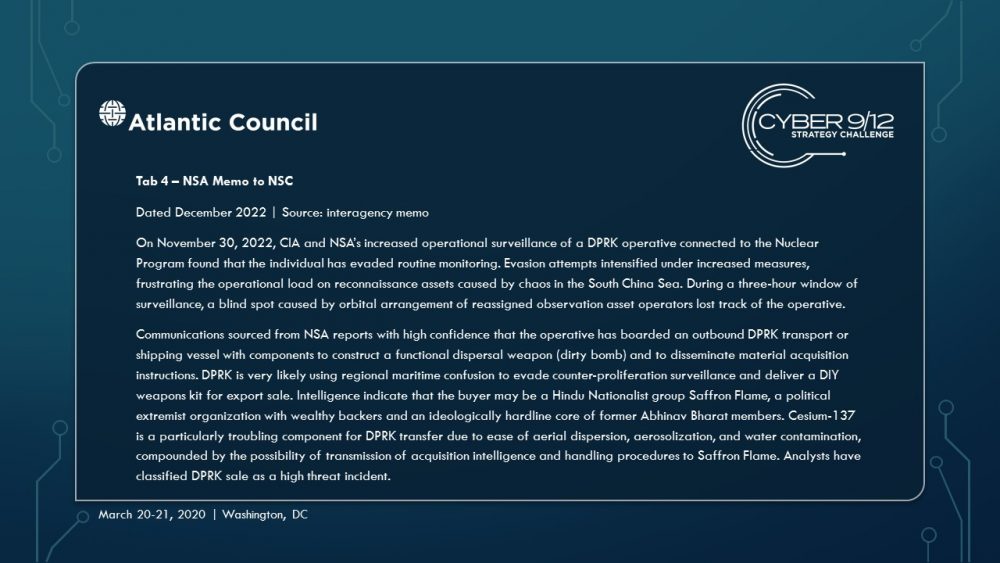
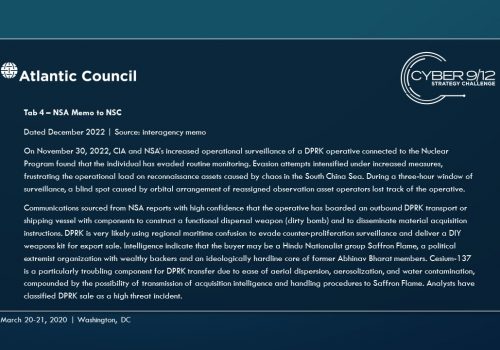
Finally, North Korea loads a dirty bomb kit on to a ship, taking advantage of the AIS failures to move the device components to a Hindu ultra-nationalist group looking to acquire and use a capability independent of the mainline defense establishment. The ship includes high value personnel from the North Korean weapons program whose disappearance triggers an escalating series of alerts and reporting from the Intelligence Community. At this time, a private People’s Militia communication is also discovered, which identifies the group as the main actor behind the primary global malware.
Students must therefore analyze how they can best A) respond to the ongoing cyber and economic crisis, B) interact with all actors involved to ensure the best solution for all actors (but specifically US and China), and C) block the proliferation event.
Below, we feature the policy analysis and recommendations of a handful of teams who succeeded in advancing to the semi-final and final rounds of the 2020 Washington, DC competition.
Find the complete scenario here.
Intelligence Report I
Intelligence Report I Top Recommendations

Intelligence Report I Policy Options

American University AU Cybernauts
Team members: Jordan Bresnahan, Shana Brouder, Matthew Dean, Julia Rapp
The AU Cybernauts of American University proposed three escalating policy options and recommended the adoption of one policy option, titled “Getting Ahead of SEASIQ,” which instructs the US Department of Homeland Security (DHS) to lead an Interagency Task Force (ITF) to coordinate both public & private sector efforts on the investigation/response to the crisis. The National Security Council (NSC) should leverage diplomacy to expand contact with key partners in the Association of Southeast Asian Nations (ASEAN) region to alert the possible spreading malware & potential disruption to shipping logistics.
The ITF will 1) perform forensic analysis on infected USB device to ascertain what actions the malware carries out, how it spreads, identify the C2 servers, & TTPs to obtain a comprehensive assessment of recommended remediation actions, 2) coordinate with private sector to develop alternative methods to SEAFARER & how they could be implemented, & 3) communicate updates to relevant state & local governments. While the other policy options provided remedial actions and tangible escalation, AU Cybernauts recommended moving forward with “Getting Ahead of SEASIQ” due to its ability to capitalize on agency/department advantages.
Read AU Cybernaut’s Intelligence Report I written policy brief and decision document.

Columbia University Couldn’t Hack It 2.0
Team members: John Dees, Sarah Husain, Sarah Quirk, Virpratap Vikram Singh
Couldn’t Hack It 2.0 of Columbia University recommends that NSC explore a combination of two of their proposed policy options. To contain spread, DHS and its Cybersecurity and Infrastructure Security Agency (CISA) must liaise with BOLH to ensure logging out of SEAFARER accounts are underway. US Coast Guard (USCG) should contact the affected three vessels using satellite phones to redirect to nearest US port for system inspections, while Department of State (DoS) warns authorities in Manila and coordinates strategic partners. USINDOPACOM will investigate if Military Sealift Command use SEAFARER and the Naval Criminal Investigative Service (NCIS) Cyber will screen US Navy port facilities.
To preserve safety, Department of Transportation (DOT) will increase manning on all US-flagged commercial ships, while DHS require merchant vessels have enough crew to navigate using paper charts. USCG should conduct manual inspections of incoming containers, while State Department should assist the Singaporean government with vessels experiencing navigational challenges in Straits. To mitigate economic disruption, State Department should direct US Embassy in Singapore to divert shipping vessels for non-essential trade to Sunda and Lombok Straits. We should explore options for US foreign assistance, and request Federal Bureau of Investigation (FBI), Transportation Security Administration (TSA), and Customs and Border Protection (CBP) officers stationed at the US Embassy in Singapore to assist Singaporean port facilities with malware cleaning and manual cargo verification.
Read Couldn’t Hack It 2.0’s Intelligence Report I written policy brief and decision document.

Georgetown University STIA Stingers
Team members: Carlos Aramayo Rana, Elizabeth Bujwid, Hannah Hess, James Plewniak
Georgetown University’s STIA Stingers proposed a policy option with a public-private approach, combining a DHS-led government response in coordination with private stakeholders including Microsoft, who supports the operating system that runs SEAFARER; Symantec, for security expertise; and Cisco Talos, for forensic investigation. They attempt to move away from a zero-defect approach to focus on strategic thinking, agility and innovation. Private partners will be tasked with developing an immediate solution to patch to the Windows vulnerability. These companies will also contribute to a mitigation process formulation led by DHS to train SEAFARER users in cyber hygiene procedures.
Beginning immediately, shipping companies should cross-reference software manifests with paper manifests, through facilitating inter-state, agency, and public-private communication. DoS will liaise with other impacted countries, and National Security Agency (NSA) and FBI will attempt to attribute the attack. In the short-term, DoS should facilitate an international response that corresponds with the DHS-led effort to unite our partners under a clear set of common objectives, while DHS, NSA, FBI cyber teams, alongside USCYBERCOM, engage with the private sector and international partners to coordinate technical responses, build resilience, deter future attacks and work on attribution. In the long-term, the FBI criminal investigation and Department of Justice (DoJ) should prosecute and indict parties found responsible to elicit deterrence and reinforce boundaries.
Read STIA Stingers’ Intelligence Report I written policy brief and decision document.

Indiana University Still Cool With Whatever
Team members: Kaitlyn Colin, Oyedotun Oyesanmi, Jared Stancombe, Ryan Walsh
Indiana University’s “Still Cool with Whatever” offered three recommendations in the order of priorities. The first recommendation (within the next 24 hours) calls upon USCG to investigate threats to physical and cybersecurity at Port of Long Beach and the Maritime Transportation System (MTS) in coordination with US Government, CISA, State, Local, Tribal and Territorial authorities (SLTT); and private industry. Then, they recommend the review of personnel records to identify any potential affiliations with foreign terrorist organizations, while the Maritime and Port Security-ISAO (MPS-ISAO) will provide threat intelligence. Recommendation 2, (within the next 48-72 hours) recommends CISA coordinate asset response with USG and SLTT to support maritime stakeholders’ response to cargo management software vulnerability and ransomware threats.
US-CERT will work with the software vendor to mitigate the software vulnerability; ICS-CERT within CISA and the National Cybersecurity and Communications Integration Center’s Hunt and Incident Response Team (NCCIC HIRT) will help identify ICS systems that are compromised; CISA will work with maritime companies to strengthen systems and networks against physical and cyber threats; and USCG will support the aforementioned agencies to inform maritime staff. Finally, recommendation 3 (within the next week) suggests that Intelligence Community partners will provide intelligence and support to relevant USG and SLTT agencies for law enforcement investigations, critical infrastructure protection, and global threat intelligence.
Read Still Cool With Whatever’s Intelligence Report I written policy brief and decision document.
Intelligence Report II
Intelligence Report II Top Recommendations

Intelligence Report II Policy Options

American University AU Cybernauts
AU Cybernauts of American University developed three stages of interventions. In the short-term (2-8 weeks), they recommend invoking PPD-41, with CISA requesting relevant stakeholders immediately change all passwords, halt utilizing data backups, and increase monitoring of DPRK financials. Diplomatically, DoS will hold a bilateral meeting between DPRK and China discussing reasons for raising its threat level. DoS will leverage ASEAN to facilitate international cooperation, and its relationship with Japan to share information on SEAFARER replacement systems. Domestically, president will address to the nation on cyber incident information and reassurance.
In the medium term (3-6 months), DHS will help BOLH remediate, while the Office of the Director of National Intelligence (ODNI) will coordinate all-source intelligence assets to monitor known major threat actors to assess attribution and possible preparations for additional cyber exploitation. Cyber Command will defend forward when sufficient credible and verifiable intelligence corroborates with high confidence attribution for the saBOATeur and AIS intrusions. U.S. ambassadors to the United Nations (UN) will address General Assembly on saBOATeur attribution when available and the International Maritime Organization (IMO) to publish formal protocols established during AIS outages.
In the long term, DHS will fund a public-private partnership to create alternative to SEAFARER, while DoS will facilitate the creation of more reliable AIS system administered by the IMO and share intelligence collection assets including space, undersea based, or high altitude UAV to maintain shipping operations.
Read AU Cybernauts’ Intelligence Report II decision document.

Columbia University Couldn’t Hack It 2.0
Columbia University’s Couldn’t Hack It 2.0 found it necessary for the NSC to coordinate an interagency approach. First, the FBI will investigate potential US-based threat actors and gather intelligence on North Korea through the NSA. Next, the NSC will engage trade associations and an ICT supply chain risk management task force through CISA to protect supply chains and manage the shipping crises.
The NSC will also work with the IMO to issue regulations on AIS through USCG, while all merchant vessels in US waters will be sanitized and ordered to follow IMO guidance on cyber risk management to prevent the spread of the malware. Diplomatically, the US should engage Chinese government to coordinate a USG-Chinese response to port congestion, and begin dialogue with South Korea, Japan, India, and Australia through security cooperation agreements. Mirror the Port of Osaka’s response through the development of new systems and public private partnerships. Last, unlock Federal Emergency Management Agency (FEMA) emergency grants to bolster cybersecurity incident response.
Read Couldn’t Hack It 2.0’s Intelligence Report II decision document.

Georgetown University STIA Stingers
Georgetown University’s STIA Stingers recommended three options assessing risks and benefits for each. First, immediate engagement with the most severely affected states (China, the Philippines, Malaysia, and Indonesia) is recommended, as well as communication on the extent of damage, intended USG response, and progress towards attribution and patching. Risks of this policy include loss of classified sources and methods, and delay of execution.
Second, ships should immediately cease relying on AIS, while the Federal Maritime Commission (FMC) and IMO disseminate information to mariners and harbormasters and instruct them to rely on shipboard navigation equipment’s and V/UHF radio transmission for hailing. The risk of this option is the possibility of maritime collisions—especially of large, difficult to maneuver, vessels such as oil or LNG supertankers, and especially in a choke point or port.
Option three recommends CISA lead effort to understand both the malware and threat actor(s) and mitigate new threats. CISA will leverage NSA and USCYBERCOM to advance technical responses, build resilience, and deter future attacks. CISA will coordinate with the private sector to develop and disseminate patches and work towards attribution, while supporting DoJ’s gathering of evidence if possible. The risk of this option is the administrative burden to CISA and economic costs of delay.
Read STIA Stingers’ Intelligence Report II decision document.

Indiana University Still Cool With Whatever
The Indiana University’s Still Cool With Whatever recommended three courses of action. A cyber Unified Coordination Group (UCG) should be established to coordinate the response to recent maritime cyber incidents. The FEMA Administrator should activate the FEMA National Response Coordination Center (FEMA NRCC) to Level 2. Finally, DoS, DOT, Department of Commerce (DOC) should continue to work with partners to coordinate a global economic response. The response can be organized from severe to medium priority. In severe priority (12-24 hours), cyber UCG will conduct an asset response in coordination with NCCIC, FEMA NRCC will be activated to level 2, and DoS will work with with Indonesia, Malaysia, and Singapore on an economic response. In High Priority (24-36 hours), INDOPACOM will protect US maritime interests, ODNI will monitor the Pacific region, and DoT will coordinate with IMO. In Medium priority (36-48+ hours), USCG will coordinate with racom implementation and the US Trade Representative will coordinate with ASEAN on economic response.
Read Still Cool With Whatever’s Intelligence Report II decision document.
Intelligence Report III
Intelligence Report III Briefings
Columbia University – Couldn’t Hack It 2.0
Georgetown University – STIA Stingers
Intelligence Report III Top Recommendations
Columbia University – Couldn’t Hack It 2.0
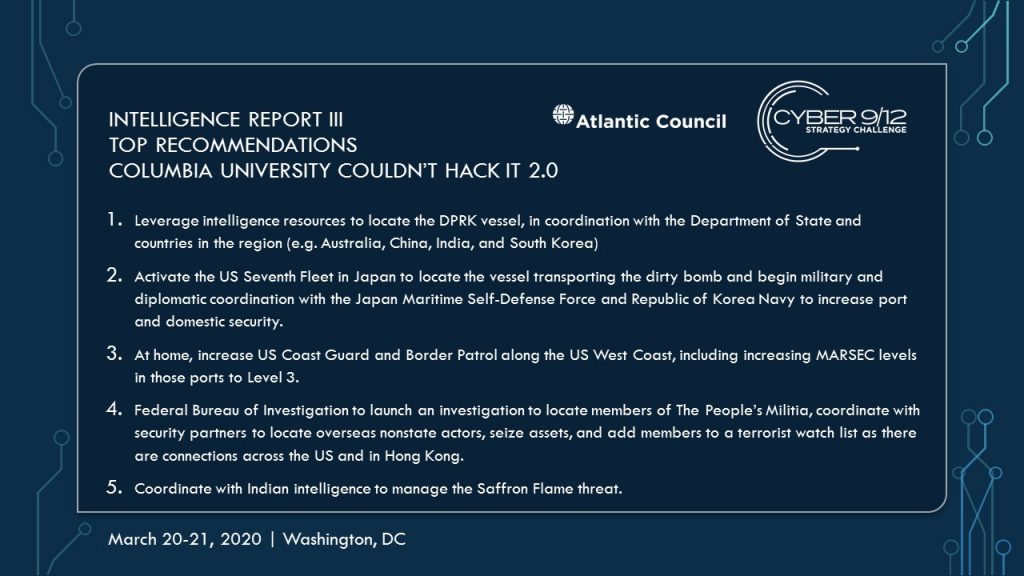
Georgetown University – STIA Stingers