Operationalizing integrated deterrence: Applying joint force targeting across the competition continuum
Table of contents
- Introduction: Why the United States needs a new targeting model better suited for cooperation
- Expanding the joint force’s competitive mindset
- Operationalizing integrated deterrence: A new model for targeting and effects
- Explaining the model of a modified targeting and effects process
- I. Placement and access
- II. Focused understanding
- III. Options
- Targeting throughout the competition continuum
- Harnessing data to improve the targeting and effects process
- Data
- Sense
- Make sense
- Act
- Using the competition space to prepare for high-end armed conflict
- Shaping the environment
- Shaping across the physical and virtual domains
- Capability development
- The way forward
- Culture: Adapting the joint force’s mindset to global problems across the competition continuum
- Incorporating all instruments of power
- Embracing the global nature of problem sets
- Technology and data: Building a resilient and holistic data architecture
- Authorities, rules of engagement, and risk: Updating DOD guidelines and standards
- Conclusion
- About the authors
Introduction: Why the United States needs a new targeting model better suited for competition
In these times, business as usual at the department is not acceptable.
Traditional joint force deterrence is no longer sufficient: a near-singular focus on armed conflict and platform-based capability development fails to deter strategic adversaries like China and Russia from their pursuit of strategic objectives while simultaneously increasing the risk of war. Simply owning the most advanced weaponry, while ceding ground in the competitive space left of conflict, is not enough to meet US deterrence needs, nor is it sufficient to ensure the joint force prevails in conflict. Expanding the joint force’s construct for targeting and effects generation will enable the Department of Defense (DOD) to more effectively deter future conflict while simultaneously shaping the environment to the joint force’s advantage in conflict should deterrence fail.
Why the twenty-first century security environment merits an updated approach
Today’s security threats span the competition continuum, cut across theaters and domains, and are intensified through the application of emerging technologies. The joint force faces challenges spanning the full competition continuum from high-end conflict to gray zone competition, including cyber threats and economic coercion, to cooperation. Technological advancements have changed the character of threats, the types of activities that the DOD can conduct, the speed at which it can act, and expanded its notion of physical and non-physical tools and effects. Specifically, the evolution of the cyber domain has enabled the joint force to gain access to non-physical spaces and generate options to achieve effects in a matter of milliseconds. The realities of twenty-first century competition drive the need to confront adversaries across a global contact layer to counter malign activities and proactively advance US strategic objectives. In other words, actions in one theater or domain can generate options and lead to outcomes in distant corners of the globe.
Moreover, the joint force faces a far more sophisticated adversary in China—qualitatively and quantitatively—than it did in countering violent extremist organizations over the past two decades. Strategic competition requires a significant mindset shift to effectively harness the effects of multiple instruments of power in a global, multi-domain, and coherent manner. DOD doctrine acknowledges this, but the department and joint force have yet to fully operationalize it.
While many activities executed along the competition continuum can enable success in conflict, specific operations, activities, and investments are necessary to ensure joint force superiority in direct combat, especially considering the criticality of combined arms warfare with allies and partners, as well as the seamless integration of multi-domain fires and effects. joint force activities must continually pursue positional advantage across the competition continuum to achieve the necessary balance between deterrence and conflict preparation. Yet, currently, the level of attention to and investment in preparation for armed conflict inhibits the joint force from leveraging the vast data, tools, and authorities at its disposal to prevent such conflict from occurring in the first place.
How joint force operations can meet an evolving threat landscape
The joint force must update its approach to targeting and effects generation to respond to the range of security challenges at hand, else it risks losing without going to war. Success across the full competition continuum will be enabled by the joint force’s ability to effectively harness data and a wide spectrum of tools and authorities with speed, precision, and lethality. This necessitates a deeper and more informed understanding of adversary capabilities, the operating environment, the interconnected nature of the physical and virtual domains, and the range of data sources available to operators. By “expanding its competitive mindset and competitive approach”1US Joint Chiefs of Staff, Joint Concept for Competing, February 2023, https://s3.documentcloud.org/documents/23698400/20230213-joint-concept-for-competing-signed.pdf. —to include and integrate tools, information, and actions that span the competition continuum—the joint force can exploit this understanding to apply the right effects to the right problems at the right times, advancing strategic objectives and maintaining informational, decisional, and combat dominance. An expanded competitive mindset will allow the joint force to view competition not as an inevitable march toward future conflict, but rather as a persistent effort to gain and maintain positional advantage across all domains.
The joint force is designed to excel at crisis response; it must make a deliberate mindset shift to plan prior to impending crisis (and prevent such scenarios from occurring in the first place). However, while the urgency of evolving the joint force’s targeting framework is evident across doctrine and policy,2DOD guidance and Joint Doctrine, such as the integrated deterrence concept nested within the National Defense Strategy and the Joint Concept for Competing, recognize that security challenges facing the United States span the competition continuum. See Joint Chiefs of Staff, Joint Concept for Competing, February 10, 2023, https://s3.documentcloud.org/documents/23698400/20230213-joint-concept-for-competing-signed.pdf, and US Department of Defense, 2022 National Defense Strategy, 2022, 8-11, https://media.defense.gov/2022/Oct/27/2003103845/-1/-1/1/2022-NATIONAL-DEFENSE-STRATEGY-NPR-MDR.PDF. the joint force has not yet taken to scale an assertive approach to dominating across the competitive space. Doctrine included in the DOD’s 2022 National Defense Strategy (NDS) and the Joint Concept for Competing, for instance, make clear that the department and joint force are thinking about strategic competition more broadly, yet operationally—through authorities, combatant commands, and collaboration with different agencies and allies—DOD and the joint force have yet to fully realize integrated deterrence.
Explainer: Targeting and effects generation
Targeting: Traditional joint or dynamic targeting is “the process of selecting and prioritizing targets and matching the appropriate response to them.” In this paper, targeting is an enabler of options, characterized as a continuous activity that furthers the pursuit of objectives by addressing critical intelligence and operational requirements and shaping the environment through a multitude of proactive means. Targeting includes everything from illuminating human networks and key actors, to finding and fixing mobile capabilities, to identifying cyber access vectors and vulnerabilities.
Effects: While conventionally viewed as the “finish” of the targeting cycle—the kinetic fire or kill—effects generation here refers to the employment of instruments of national power (individually or in concert) to achieve a desired outcome. This ranges from traditional kinetic military fires to information operations, cyber tools, and electronic warfare, to targeted economic sanctions and law enforcement actions, to diplomatic démarche or other means of localized leverage.
What this report sets out to achieve
Operationally, the joint force has not adapted to an era of strategic competition, which requires targeting across theaters and domains, the entire competition continuum, and leveraging the range of data sources at its disposal. Doing so requires the joint force to stitch together the data, tools, and authorities needed to achieve global objectives—rather than viewing missions as constrained to a singular region or ends, as has been the status quo.
This report outlines a framework to leverage existing targeting models to more assertively and deliberately compete by: 1) incorporating an expanded use of military and interagency capabilities; 2) leveraging expansive public and private data and harnessing it for effect through emerging technologies; and 3) smartly balancing priorities and weight of effort related to competition and conflict preparation. The authors offer key action areas for implementation at scale.
Expanding the joint force’s competitive mindset
To achieve unity of effort, the joint force must seek opportunities to integrate its operations and activities in time, space, and purpose with the activities of interorganizational partners, proxies, and surrogates.
While the Pentagon recognizes it must adopt a new mindset to prevail across the competition continuum, it continues to approach targeting and fires through a lens of armed conflict. Traditional approaches to targeting and fires still prevail across the joint force despite the recognition of a need to expand them. Traditionally, the joint force aligns “sensors to shooters” (i.e., targeting) to inflict damage on enemy personnel, materiel, or infrastructure (i.e., fires or effects generation). This sentiment is expressed through variations of the targeting cycle, whether it be the dynamic targeting kill chain (Find, Fix, Target, Track, Engage, Assess) or the Special Operations Forces-preferred cycle (Find, Fix, Finish, Exploit, Analyze, Disseminate). These processes lend well to a temporal and kinetic approach to targeting and fires—exemplified by strikes on violent extremist organization (VEO) leadership networks or disabling mobile surface-to-air threats as part of a layered suppression of enemy air defenses effort—yet they are insufficient for generating the nonlethal and continuous effects necessary in today’s expansive security environment. This traditional approach to targeting and fires is incongruent with current DOD realities, given “most joint force activities occur in the context of cooperation and competition below armed conflict.”4Joint Chiefs of Staff, Joint Warfighting, Joint Publication 1 (JP 1), July 2019, II-13.

As the DOD recognizes through its integrated deterrence concept, the joint force’s tool kit expands beyond the military arsenal, and solely relying on traditional approaches for targeting and effects is limiting. As articulated in the NDS, integrated deterrence campaigning calls for the joint force—in alignment with and often in a supporting role to other instruments of power found across the interagency—to execute “logically linked” activities to advance “strategy-aligned priorities over time” in order to counter or complicate competitors’ coercion across the globe.5US Department of Defense, 2022 National Defense Strategy, 1. Linking activities across global campaigns require a high level of understanding of competitors’ intent and capabilities and their underlying geopolitical realities, enabled by prolonged access across multiple domains, which creates options to leverage multiple effects in achieving desired ends. For example, developing an understanding of how China’s coercive economic activities in Africa and Latin America support its broader global ambitions can inform the breadth (and complexity) of US response options. While the joint force typically excels at responding to crises, single-purpose platforms and the constant rotation of forces often prohibit the long-duration stare that integrated deterrence requires for proactive campaigning left of crisis.
Operationalizing integrated deterrence: A new model for targeting and effects
To achieve integrated deterrence, this paper outlines a model for operationalizing it. The joint force must meld the existing framework for joint targeting with a model that places a premium on gaining placement and access in a domain or region, enabling a focused understanding of an entity of interest, to facilitate a range of options for the joint force to execute in concert with other instruments of power, whether in a supported or supporting role. Each layer includes the concepts of persistence, local distinction, and global relevance, and can be in a near-constant state of change based on the sensing environment. For example, security cooperation with a partner in Southeast Asia requires access, understanding, and options that are: 1) persistent, to ensure ongoing understanding and to achieve effects over the long term; 2) locally distinct based on regional and local considerations; and 3) globally relevant, acknowledging that awareness and action related to one country affects global dynamics and goals. This layered model is represented in Figures 1 and 2 and further described below.
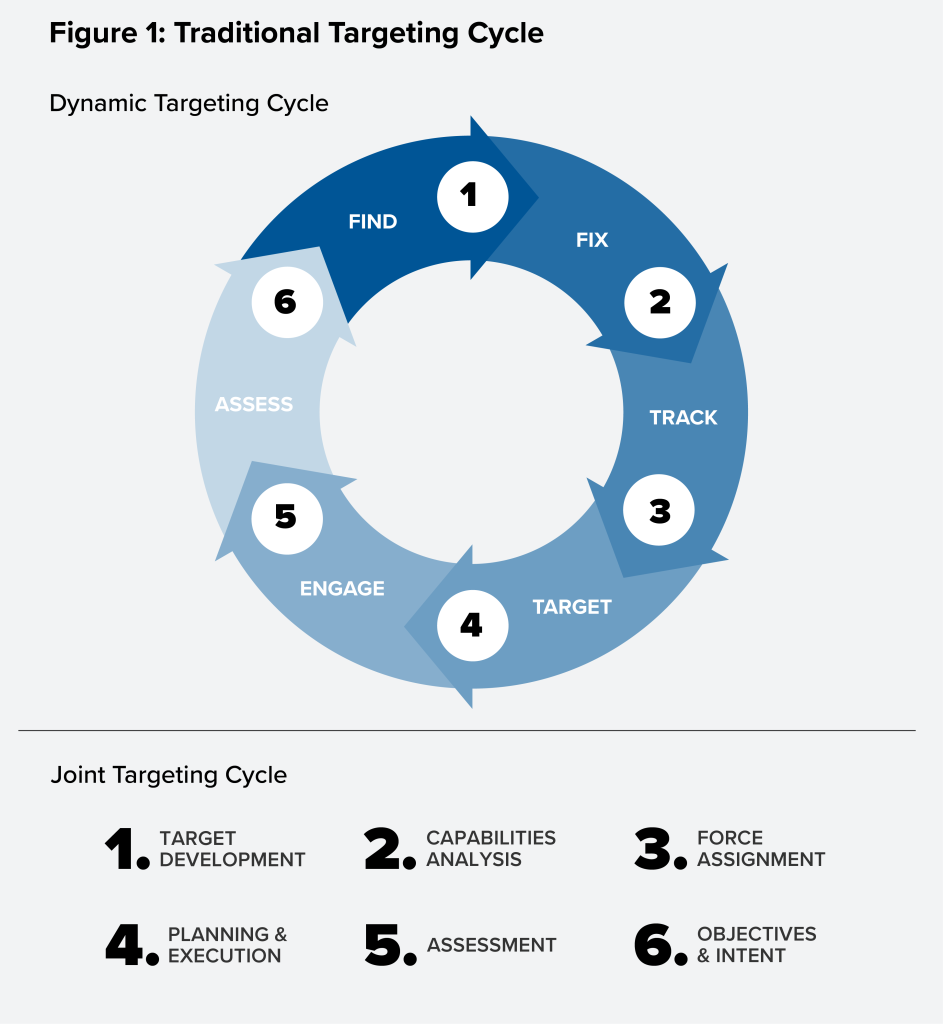
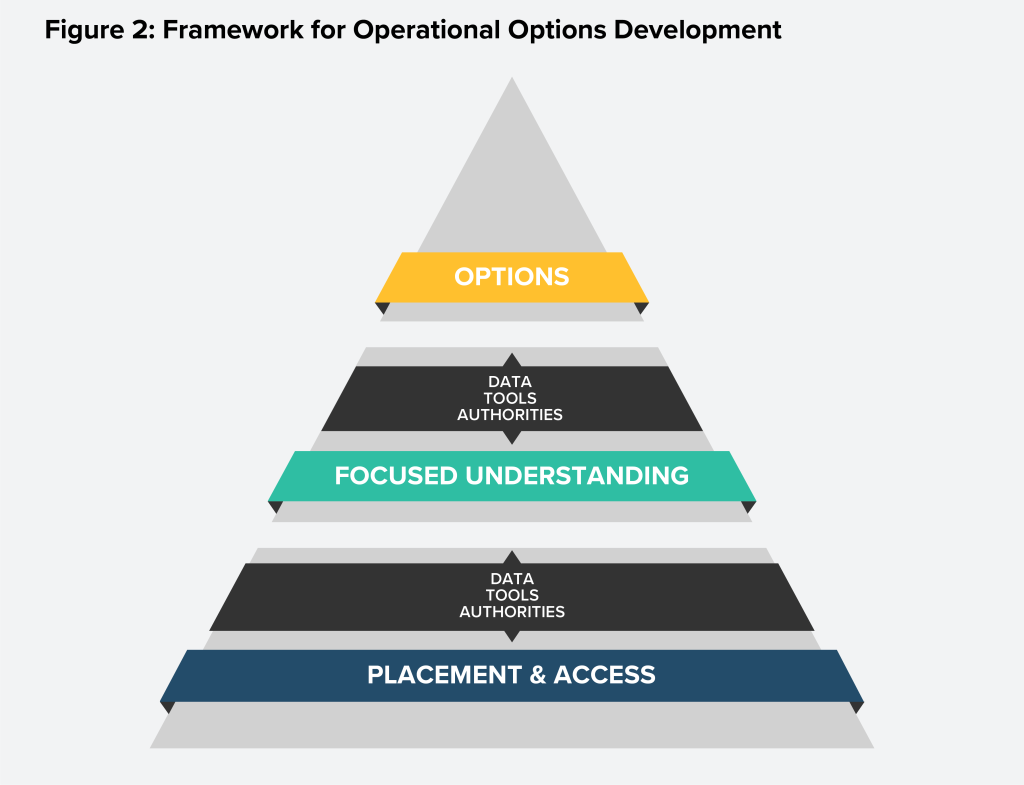
Integrated Deterrence Targeting. The figures above convey the elements of the joint targeting cycle and the dynamic targeting process (figure 1), with a philosophical and nonlinear pyramid approach to developing options for complex problems (figure 2). These two frameworks must be fused together to operationalize integrated deterrence. The joint force’s traditional targeting cycle must be informed by a foundation of situational awareness. Data, tools, and authorities are all necessary mechanisms to establish situational awareness.
Placement and access
virtual and/or physical proximity to an entity of interest
Focused understanding
situational awareness and perception of an entity (actor and/or location) and how it fits into broader geostrategic missions
Options
potential pathways forward to respond to a complex problem set and achieve outcomes, informed by focused understanding and placement and access
Explaining the model of a modified targeting and effects process
Adopting this layered model is critical for two reasons. First, the complex, global, and multi-domain problem sets the DOD faces today necessitate options that are similarly sophisticated in nature and cut across the competition continuum. By prioritizing a deeper and more comprehensive understanding of problem sets, the joint force is presented with a wider array of options to address key challenges. Such focused understanding is possible when the near-infinite amount of data available across the public and private sectors is transformed into usable information and, ultimately, intelligence.
Second, a new competitive mindset requires broadening the joint force’s tool kit beyond traditional military effects. The joint force has the authority to, and does, execute non-kinetic targeting, albeit insufficiently, yet it prioritizes kinetic fires as part of the traditional targeting cycle. Fusing kinetic and non-kinetic fires is critical not only from a deterrence perspective but also, more significantly, to enable victory in armed conflict. Yet, alone, the military instrument of power is insufficient for the problem sets germane to integrated deterrence. While the joint force has significantly advanced its organic non-kinetic capabilities, it primarily leverages kinetic effects, which neglects other instruments of power, disincentivizes creative thinking, and leads to poor integration with interagency partners.6Cesar Augusto Rodriguez, Timothy Charles Walton, and Hyong Chu, Putting the “FIL” into “DIME”: Growing Joint Understanding of the Instruments of Power, Joint Force Quarterly, April 2020, https://apps.dtic.mil/sti/pdfs/AD1099537.pdf. A high degree of awareness of the capabilities and authorities that other instruments of power bring to the table is critical such that they can be synchronized with, or amplified by, joint force activities at all echelons.
The process of generating placement and access, focused understanding, and options is not linear, and each stage can and should inform the others over time. Specific placement and access may be generated to understand a particular problem in a sophisticated manner such that novel options can be developed. Similarly, focused understanding may drive the need for additional or alternative access to close critical intelligence gaps and inform options. Likewise, commanders may demand options to address a particular problem, which in turn will inform the planning process to generate the necessary access and understanding. Below is an overview of the three foundational elements of the pyramid.
I. Placement and access
To develop the focused understanding required for integrated deterrence, the joint force cannot stare at problems from afar. Placement and access are foundational to developing an enhanced understanding of the problem sets facing the United States. Placement and access, however, does not necessarily mean physical proximity of the military to a particular interest area—it also encompasses virtual presence and can be developed by the joint force, interagency partners, and allied counterparts. It also implies some degree of usability, sustainability, and repeatability; simply visiting a location or gaining virtual access to a network does not equate to true placement and access. Rather, that access must be repeatable if it is temporal in nature, sustainable over operationally relevant time periods, and usable for alternate purposes such as data collection, security cooperation, or reception, staging, onward movement, and integration. Placement and access can be enhanced by leveraging data from a multitude of sources to enable the joint force insight into digital networks of value to access, or the nature of key partnerships required for physical access. Additionally, enhancing existing authorities and making them more flexible would allow units pursuing a mission set in one area to adapt and undertake additional mission sets that may be valuable for a broader or global mission set.
Evolving the joint force approach to placement and access will open a range of opportunities given the interconnected nature of global problem sets. For example, France’s historical security cooperation and counterterrorism activities in the Sahel region of West Africa, during the 2010s, could have also served as an access vector to increasing understanding of the growing threat of Russian private military corporations (PMC) like Wagner Group in the region. This physical proximity can enable a deeper understanding of Wagner’s activities in the region, potentially driving requirements for further physical or virtual access or informing options in line with global campaign plans to counter Russian malign influence. Critically, the joint force must explore means to creatively exploit access when mission convergences exist—units or platforms deployed for one purpose, such as countering VEO, may enable access vectors to support another mission, such as strategic competition, and vice versa. While clarity of primary and secondary objectives of missions would need to remain, the makeup of units and task forces, and the requisite authorities given to them, should be meaningfully considered to capitalize on mission convergences. Not only does this approach create efficiencies with respect to endeavors like security cooperation, but it also offers the opportunity to obfuscate strategic intentions.
II. Focused understanding
Focused understanding of an actor, environment, or relationship is required to solve complex problems, not only due to the sophisticated capabilities of strategic adversaries but also because integrated deterrence campaigns are global in nature. Transregional, multi-domain problems cannot be thoroughly addressed in compartmentalized and only localized ways. Rather, the joint force must stitch together regional understandings based on local access and conditions with broader knowledge informed by other global touch points. The roles of partners, both interagency and international, are critical in developing focused understanding. Not only do they enable multi-domain access, but they also provide unique perspectives. The vast amounts of commercial and government data can and should be harnessed and fused to improve focused understanding of actors and problem sets. While data from traditional sources is immensely valuable, open-source information—organized into actionable information—can drastically improve understanding of patterns and behavior. For example, social media data may help inform US forces of the presence of an adversarial force’s covert presence in a country that may be hard to identify or find evidence for using other means. Ultimately, the fusing of different data sources more consistently can help understanding across the competition continuum.
Building on the previous example, to address Wagner Group’s activities in the Sahel, the joint force should first understand how those activities tie into Russia’s global campaign to secure influence and create instability through expeditionary PMC activities. A holistic understanding of Wagner’s activities across the Sahel, Central Africa, Latin America, Syria, and Eastern Europe presents a more informed picture of the totality of the problem, as well as the associated pressure points, vulnerabilities, and opportunities. Moreover, the local US country team, elements of the intelligence community, French forces, and host-nation partners will all view the Wagner problem in different lights, which can enhance the joint force’s perspective and is necessary in developing viable options leveraging all instruments of power.
This combination of regional and global understanding, enabled by joint force and partner access and capabilities, ultimately informs a far greater range of options than is achieved strictly through a regional military lens, which has been the status quo. Critically, focused understanding better informs risk assessments at echelon, abating risk aversion frequently seen at higher levels of command authority that are farthest removed from the tactical edge.
III. Options
Senior leaders and commanders typically request a range of options to address problems, both to allow flexibility and enable sound decision-making in light of strategic priorities and risks. The Joint Concept for Competing calls for the joint force to:
Identify approaches that enable it to apply its military capabilities proactively, and differently in some cases, to gain influence, advantage, and leverage over adversaries to establish the necessary conditions to achieve strategic outcomes.
While doctrinally this is clear, today’s traditional approach to targeting and competition limits the most effective suite of options from being generated. More-nuanced options may place the joint force in a supporting role to other departments and agencies: for example, conducting traditional manhunting activities (via military authorities) to enable a diplomatic action such as a démarche (via Department of State authorities). The level of sophistication required to achieve what the Joint Concept calls for, especially across activities below armed conflict, makes both risk and efficacy assessments challenging. It is far more difficult to quantify the effectiveness of a campaign to counter Chinese regional influence—for example, assessing long-duration efforts to obstruct effort by the People’s Republic of China (PRC) to secure access, basing, and overflight—than it was to measure the success of kinetic drone strikes during the Global War on Terrorism. This challenge is met not only by prioritizing focused understanding but also by parlaying that understanding into a range of options that may be locally distinct but support global campaign plan objectives.
Ultimately, options for senior decision-makers are developed to achieve outcomes that are in service of more-aspirational objectives. Again, examining Wagner activity, a desired outcome of an operation could be to deny Wagner’s ability to securely communicate between several outstations across the Sahel. The aspirational objective is to critically degrade Wagner’s ability to conduct and sustain expeditionary activities globally.
Targeting throughout the competition continuum
This model for the generation of options for complex problems must be melded with an adaptation in the application of traditional joint force targeting processes. Joint targeting is not solely reliant on joint force tools, capabilities, and authorities; it can and should incorporate other instruments of power—by collaborating across departments and agencies—to bolster data and inform understanding, as well as “identify, develop, and affect targets to meet commander objectives.”8Joint Chiefs of Staff, Joint Targeting, Joint Publication 3-60 (JP 3-60), September 2019, II-8 – 11-9.
Take, for example, a PRC network in Latin America that facilitates command and control of dual-use infrastructure. Here, data could be harnessed from the intelligence (e.g., National Security Agency) and diplomatic (e.g., Department of State Regional Security Office) instruments of power to identify a particular local criminal network that facilitates relevant PRC contracting activities. Host-nation law enforcement can then apply pressure on the criminal network to share information about the PRC actors with whom it engages routinely. Over time, this information can help generate several options to gain access to the objective network through Special Operations Forces-enabled cyber activities. Throughout, the military (e.g., Military Information Support Operations) and diplomatic (e.g., Department of State Global Engagement Center) instruments of power can expose malign PRC practices through information operations to positively shape narratives in line with strategic objectives. The joint targeting cycle could be leveraged multiple times for:
- Employing traditional manhunting techniques to find and fix specific local criminal actors of interest, develop their pattern of life, then using non-kinetic fires to register their phones with specific networks that enable intelligence access to key digital data.
- Leveraging data obtained through financial (e.g., Treasury Department Office of Foreign Assets Control) instruments of power to target specific institutions that enable transactions between local criminal networks and the PRC. This data can be correlated with intelligence derived from the activities above, as well as populated to other portions of the joint force focused on countering PRC dual-use activities to further global understanding of their tactics, techniques, and procedures.
- Conducting intelligence preparation of the cyber environment to find and fix key nodes that are vulnerable to offensive cyber fires (e.g., US Cyber Command), as well as to bolster and amplify information operations that counter local PRC propaganda strategies.
The myriad of joint targeting activities outlined above not only enable specific tactical actions but also inform or further placement and access that continuously matures the collective understanding of the operating environment. Given the nature of strategic competitors, much of this understanding can be exported to other locations to bolster awareness and enable the linking of activities in a logical way as outlined in the NDS. At the center of this process is data, and as stated by former Deputy Secretary of Defense David L. Norquist, “our ability to fight and win wars requires that we become world leaders in operationalizing and protecting our data resources at speed and scale.”9Department of Defense, DOD Data Strategy, September 2020, i, https://media.defense.gov/2020/Oct/08/2002514180/-1/-1/0/DOD-DATA-STRATEGY.PDF.
Harnessing data to improve the targeting and effects process
Data is a strategic asset that must be operationalized in order to provide a lethal and effective joint force.
The joint force’s ability to leverage data at speed and scale, predicated on its adoption of emerging technologies such as artificial intelligence (AI), enables this framework for targeting and effects generation. Data informs the nature of required access, feeds the focused understanding process, and enables the development of well-informed options that artfully balance desired outcomes with strategic risk. However, raw and unstructured data in isolation does not create a decisive advantage. Rather, it must be harnessed for effect, transforming data into both information and intelligence that is usable and accessible at the speed of relevance.

While the importance of data is nothing new, the joint force must grapple with the explosion of available data spanning all domains, sectors, and sources. Technologies such as AI and machine learning (ML) present meaningful ways to navigate this near-infinite amount of data. The 2020 DOD Data Strategy envisions the department as a “data-centric organization that uses data at speed and scale for operational advantage and increased efficiency,” with particular focus on enabling all-domain operations, more rapid and informed decision-making, and organizational business analytics.11US Department of Defense, DoD Data Strategy, 2. Moreover, AI makes determinations and finds data connections in ways humans alone cannot, encapsulating everything from making obvious connections more rapidly (e.g., using satellite data to geolocate battlefield equipment) to identifying valuable datasets overlooked by humans (e.g., how commercial shipping telemetry data can enable deeper understanding of the PRC’s fifth-generation [5G] infrastructure development in Africa).
Data
Data is obtained by a variety of automated or manual and physical or virtual means. Any entity that can obtain data is considered a sensor. Data becomes information once put into context prescribed with meaning by the observer. Often, the meaning prescribed by the observer can be adapted as understanding of the environment grows, making particular datasets more or less useful. The process by which information is transformed into intelligence is complex and combines both art and science as described in JP 2-0 Joint Intelligence:
- Intelligence fuses and evaluates information from multiple sources to provide the most accurate assessment possible of the current state of the operating environment.
- From current assessments, intelligence draws predictive estimates of the full range of potential alternative future states of the operating environment.
- To inform decisions, intelligence illuminates how the operating environment may react to different friendly options under consideration.12Joint Chiefs of Staff, Joint Intelligence, Joint Publication 2-0 (JP 2-0), May 2022, I-2.
The flow from data to intelligence—known as the processing, exploitation, and dissemination (PED) cycle—is illustrated in Figure 3, overlaid with the targeting framework from Figure 2.
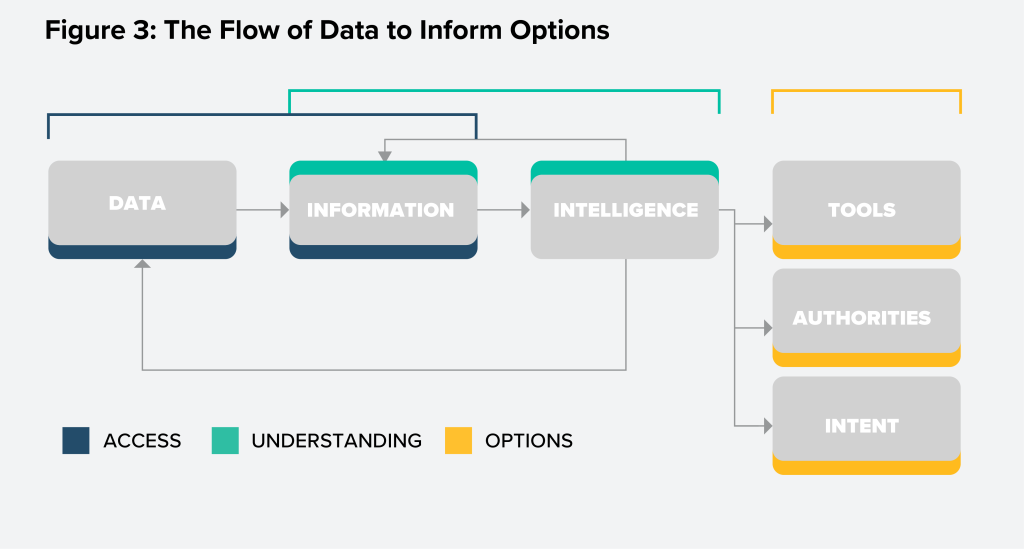
The nature of today’s security environment necessitates the execution of PED at greater speed and scale than is achievable by humans alone. Particularly, the operating environment below armed conflict—which encompasses most joint force activities—places a premium on scale. To effectively compete globally and deter China and Russia, large quantities of data must be triaged and transformed into intelligence to inform transregional and multi-domain activities that are logically linked. In contrast, armed conflict—the highest-risk joint force activity—places a premium on speed. Rapidly processing and disseminating targeting data, effectively integrating kinetic and non-kinetic fires against mobile targets, and incorporating virtual capabilities that can affect adversary nodes within milliseconds would be impossible without AI/ML and human-machine teaming. The Joint All-Domain Command and Control (JADC2) concept describes the importance of this flow from data to intelligence based on the requirement for “joint force commanders to ‘sense,’ ‘make sense,’ and ‘act’ in the operational environment.”13US Department of Defense, Summary of the Joint All-Domain Command and Control (JADC2) Strategy, March 2022, 4, https://media.defense.gov/2022/Mar/17/2002958406/-1/-1/1/SUMMARY-OF-THE-JOINT-ALL-DOMAIN-COMMAND-AND-CONTROL-STRATEGY.PDF. While this paper is not focused on the JADC2 and Joint All-Domain Operations (JADO) concepts, the employment of this paper’s updated targeting and effects process would support the more rapid implementation of JADO/JADC2 across the joint force.
Sense
The joint force must consider nearly all entities to be sensors, ranging from sensitive intelligence collection activities to open-source commercial datasets. Adopting a more competitive mindset requires the joint force to democratize data, allowing for a wide array of data-gathering streams to interact with AI algorithms trained to produce usable information. Much attention is placed on gathering data from the tactical edge, yet the edge can take many forms across physical and virtual spaces, regions, and domains. Critically, leveraging nonmilitary instruments of power, as well as allied and partner sensors, can both increase and diversify the data gathered. The role of commercial data is invaluable, with the private sector often having access to people, places, and things that are difficult, if not impossible, for overt government entities to replicate. However, while nontraditional data sources are crucial to building global situational awareness, the DOD does not currently have the communications infrastructure to integrate data from these various inputs at speed and scale—this change must be accelerated.
Make sense
Making sense of the operating environment correlates to the process depicted in Figure 2. The importance of AI/ML becomes paramount here, such that the joint force can achieve automation of prediction at speed and scale, while reserving judgment for human decision-makers on or in the loop. Ultimately, larger and more diverse datasets correlate to more sophisticated training of AI/ML algorithms, increasing the precision of predictive modeling to inform human decision-making. Analysis of the nature of adversary activities—and the subsequent options to address them—may look quite different when viewed through a whole-of-government versus strictly military lens. Furthermore, allies’ and partners’ perspectives on problem sets, especially those close to home, offer invaluable information to complement the joint force’s understanding of the operating environment.
Act
Taking action is a data-driven endeavor—not only in regard to the appropriate action but also the expected adversary reaction and the associated risks. Data-informed decision-making, given its bias toward empiricism, helps challenge assumptions, drive rigorous planning, and enable more-decentralized and potentially faster decision-making. Indeed, the focus of this framework is to utilize access-enabled understanding, coupled with sophisticated data-harnessing techniques, to ultimately provide commanders with a range of well-informed, data-driven options to act. It should be emphasized that to act does not signify finality of the process. As stated in the Joint Concept for Competing, “strategic competition is an enduring condition to be managed, not a problem to be solved.”US Joint Chiefs of Staff, Joint Concept for Competing, 7. In fact, the “act” could be a decision to develop further placement and access to address critical intelligence gaps, or to submit requirements to inform further capability development for an unaddressed operational need.
The process of sensing, making sense, and acting is continuous. The speed by which this process plays out is variable based on the nature of the domain, location along the continuum, commander’s intent, and both local and global risk considerations. Deliberate planning and preparation of the operating environment, to include the establishment of relationships and infrastructure, deployment of sensors, and data architecture, and other such activities are necessary to enable this process to occur with speed downstream. In particular, active conflict places a premium on achieving maximum speed for this process, which simultaneously necessitates extensive preparation and autonomy.
Using the competition space to prepare for high-end armed conflict
Victorious warriors win first and then go to war, while defeated warriors go to war first and then seek to win.
Conflict preparation is the persistent, locally distinct, and global sensing of the target ecosystem. It is a dynamic process that constantly generates and updates the integrated targeting planning and execution decisions. Prevailing in armed conflict is the ultimate basis for the existence of the joint force, and places a significant premium on preparation to maintain a position of advantage, inform capability development, and hold adversaries at risk. Armed conflict exists on the far-right side of the competition continuum and represents the most consequential activity the joint force must prepare for and, when called upon, execute. While often referred to in sterilized terminology, a clear description of armed conflict—the application of violence to destroy an enemy’s will and means to resist—serves to highlight the care and attention that preparation for conflict requires. While any type of conflict requires serious attention, high-end armed conflict against a peer adversary represents the most potentially dangerous scenario for which the joint force must prepare. While the objective of integrated deterrence is to deter conflict from occurring in the first place, it is equally about shaping the environment to ensure joint force dominance should deterrence fail. As outlined in Joint Publication 3-0, “while commanders conduct activities of cooperation and adversarial competition, they are still preparing for armed conflict.”15Joint Chiefs of Staff, Joint Campaigns and Operations, Joint Publication 3-0 (JP 3-0), June 2022, xxx.

Conflict preparation is a balancing act. The joint force must weigh concerns of strategic risk and escalation management: “Tilting the competitive balance too far in one’s own favor will affect an adversary’s decision-making and behavior, but the effect may be vertical or horizontal escalation, not compliance.”16Joint Chiefs of Staff, Joint Concept for Competing, 22. Smartly preparing for conflict to create and maintain advantage over an adversary can be a campaign in its own right and must involve shaping activities as well as capability development. These activities will often nest within an overarching integrated deterrence campaign, but at times these endeavors may diverge, at which point the balance of priority and weight of effort must be considered. For example, winning a conflict to defend the Panama Canal would be a clear priority of the United States. However, preparation for such a conflict is not assigned the same weight of effort as, for example, the defense of Taiwan, which is being treated as a high-likelihood event by the Pentagon today.
The United States will not achieve a decisive warfighting advantage against a near-peer competitor through sheer mass or weapon systems alone—rather, the victor will be the military that stacks the deck in its advantage before conflict erupts. Russia’s current war in Ukraine highlights the severity of high-end armed conflict involving near-peer competitors. While great wartime effort is aimed at bolstering sustainment through industrial base and supply chain modernization, operational activities will eventually be curtailed to whatever pace can be sustained through resupply. The joint force’s future advantage will hinge on its ability to: 1) advantageously shape the environment and 2) field capabilities with greater speed, precision, and lethality than its adversary.
Shaping the environment
Shaping the environment is crucial to securing a position of advantage across multiple domains left of conflict. In the context of targeting and effects generation, activities to shape the environment must center around closing critical operational and intelligence gaps associated with a prioritized target list tied to operational plans. These activities are intended to enhance precision and lethality of engagement and shorten the kill chain once armed conflict begins. In line with the framework espoused in this report, focused understanding of the enemy’s order of battle, critical infrastructure, battle management tactics, techniques and procedures, and standard operating procedures is key to establishing and maintaining a prioritized target list. In this way, portions of the joint targeting cycle are accomplished prior to conflict, informing weaponeering recommendations across kinetic and non-kinetic effects, as well as the requirements necessary to develop new capabilities to counter enemy systems for which the joint force does not yet possess a solution.
Moreover, shaping activities can be geared toward increasing resiliency in the joint targeting process. Much attention is given to the challenges of contested, degraded, and operationally limited (CDO) environments and how they complicate traditional means by which the joint force projects combat power. Peer adversaries can contest environments in a multitude of ways such as anti-access/area denial capabilities, electromagnetic interference, countering space situational awareness, and defensive cyber operations. Shaping activities must prioritize alternate means of accomplishing warfighting functions given the potential for primary means to become denied or degraded. Ironically, the CDO nature of Russia’s war in Ukraine has led to a much more conventional and analogue fight than anticipated. This highlights the importance of bolstering resiliency through shaping operations, as peer adversary denial capabilities may effectively cancel out one another’s high-end platforms.
Shaping across the physical and virtual domains
As is the case throughout the competition continuum, the contact layer for armed conflict is both physical and virtual. Traditional physical targets include surface-to-air missile systems, radars, maritime vessels, and command posts, and they exist in quantities of hundreds or thousands; virtual targets include network nodes tied to communication systems, power infrastructure, situational awareness, and early warning, and they are quantified in the millions. When expanding the battlefield to the virtual domain, synchronization of kinetic and non-kinetic effects can lead to significant advantages across the joint warfighting functions17The joint warfighting functions include command and control, information, intelligence, fires, movement and maneuver, protection, and sustainment. and with regard to the principle of mass.
Gaining a competitive advantage traditionally depends on availability and posture: the forces available, and on what timeline, are determined by their current posture. In the physical world, this construct presents challenging time-distance problems when considering global conflicts, raising questions for both escalation management as well as force preservation. The virtual world can alter this paradigm by enabling virtual mass, leveraging cyber operations to hold adversary networks and capabilities at risk at unprecedented speed and scale. Even modest impact on adversary capabilities executed on this scale of mass and speed can complicate the enemy’s risk calculus and mitigate some risk associated with physical force flow into theater. Given the challenges of logistics and sustainment, efficiencies gained through the employment of virtual capabilities provide a significant advantage during a protracted conflict. Saying this, virtual capabilities are not a silver bullet and effects delivered through cyberspace are insufficient in isolation during armed conflict, and often require large up-front investment in time and resources.
The evolution of virtual targeting and effects, to include the integration with physical targeting and fires, drives a greater premium on shaping the environment prior to conflict. To hold millions of virtual targets at risk instantaneously necessitates significant preparation of the environment. Indeed, a multiyear campaign built around access and understanding—by, with, and through regional allies and partners—may be necessary to simply gain access to the right adversary networks. Development and installation of cyber capabilities would be executed in parallel, with the associated development and intelligence gaps feeding back into the overall campaign approach. Shaping campaigns can provide the decisive advantage once armed conflict begins, all while informing the joint force of its own potential vulnerabilities and thus allowing for continued defensive hardening in stride.
Capability development
While fielding innovative and advanced technologies is critical to maintaining a decisive battlefield advantage, technology (whether platform or software-based) does not on its own equate to capability.18Tate Nurkin, The Five Revolutions: Examining Defense Innovation in the Indo-Pacific Region, Atlantic Council, November 20, 2020, https://www.atlanticcouncil.org/wp-content/uploads/2020/11/Five-Revolutions-Report.pdf. Rather, it is the combination of technology, tactics, and training that creates a true capability—for instance, the United States sells fifth-generation fighter jets to other nations, but those nations do not instantly gain the capability to execute low-observable deep strike operations. Technology development must be informed by an understanding of the operating environment, the capabilities of adversaries, and the nature by which the joint force executes operations. To that end, furthering capability development is an objective for the campaigning framework outlined in this paper.
Training AI/ML algorithms often emulates or requires real-world data, further underscoring the need for capability development to harness data for effect. While great strides have been made in emulation for training, the real world offers the most significant data, which is accessible through robust campaigning activities across the joint force in concert with interagency and international partners. The integration of emerging weapon system technology such as hypersonics, lasers, and space-based fires is equally critical. Capabilities such as JADC2 seek to establish the necessary datacentric architecture for seamless integration of information and effects, which span employment times from milliseconds to hours. However, without AI/ML-driven predictive capabilities in the loop, joint force commanders will be challenged to make appropriate targeting and weaponeering decisions amid a large-scale conflict, creating significant risk with respect to sustainment, logistics, and force protection. Without a similar distribution of situational awareness, authority, and capability to the tactical edge, the joint force will not be able to field a credible combat force in a CDO environment where being disconnected from higher headquarters is the norm.
Lastly, while security cooperation is a foundational activity underlying integrated deterrence, the execution of high-end combined arms warfare with allies and partners requires a great deal of specific investment. This includes years of combined training, exercises, and rehearsals to create a dependable capability, especially when factoring in the complexity of integrating emerging technology. Incorporating allies and partners into the joint force-led scheme of maneuver will be critical to maintaining an advantage in targeting and effects generation. However, information-sharing hurdles, disparate rules of engagement, authorities, and cultural considerations must be ironed out in advance of conflict such that the full force of allied firepower can be realized. Ensuring that key allies are fielding capabilities that are JADC2 compatible will be critical to achieving the shared situational awareness required for a common operating picture. Making strides of this nature and fielding a combat-credible combined force will not be accomplished through sporadic exercises, key leader engagements, or exchanges; the joint force must train with allies and partners in the same manner with which it trains internally.
In sum, high-end conflict with a peer adversary presents the most difficult and high-risk challenge, and it requires specific attention given the gravity of its nature. When adequately prioritized, preparation for armed conflict prescribes a unique set of requirements for the joint force and its partners to execute during cooperation and competition and across multiple domains and instruments of power, which at times may overlap or diverge from deterrence. Shaping activities of this nature fall expressly within the proposed proactive targeting and effects framework given that, in the event of war, “these capabilities will shape the environment to ensure combat dominance and our ability to end any conflict on our terms.”19Department of Defense, Summary of the Irregular Warfare Annex to the National Defense Strategy, October 2020, 1, https://media.defense.gov/2020/Oct/02/2002510472/-1/-1/0/Irregular-Warfare-Annex-to-the-National-Defense-Strategy-Summary.PDF.
The way forward
If we don’t change – if we fail to adapt – we risk losing the certainty with which we have defended our national interests for decades. We risk losing a high-end fight.
Implementing change is no easy task, especially when considering the massive scale of the joint force. Nonetheless, a tidal wave of contemporary strategies, guidance and policy documents, and service visions all speak to the urgent need for change. Culture—coupled with procedural and technological changes—will be key to enabling sustainable adoption of a new approach.
Culture: Adapting the joint force’s mindset to global problems across the competition continuum
First, to deter armed conflict the joint force must adopt and operationalize the competitive mindset shift outlined in recent strategic doctrine. While armed conflict is never desirable, regardless of scale, high-end warfare between nuclear-armed peer competitors is of such gravity that deterring it from ever occurring is crucial. General Mark A. Milley’s assertion that “traditional joint force deterrence” is “less effective,” alludes to the notion that owning the most sophisticated or greatest quantity of weaponry is inadequate on its own as a deterrent.21Joint Chiefs of Staff, Joint Concept for Competing. Moreover, while an adversary’s belief in the joint force’s will to act is critical to deterrence, it cannot solely revolve around direct military force given escalation concerns. Rather, adopting a more proactive and creative approach to strategic competition can simultaneously deter malign behavior while complicating, confusing, and frustrating adversary decision-making. The spectrum of views on Russia’s war in Ukraine are informative in this regard: Some highlight US and NATO success in arming Ukraine in its valiant campaign to oppose Russia’s invasion, whereas others view the ongoing war as “a direct result of the West’s lack of resolve and failure to credibly deter Russia” from waging war on the European continent more broadly, regardless of NATO borders.22Liam Collins and Frank Sobchak, “U.S. Deterrence Failed in Ukraine,” Foreign Policy, February 20, 2023, https://foreignpolicy.com/2023/02/20/ukraine-deterrence-failed-putin-invasion/. This latter sentiment pushes the force to adopt cultural change in order to deter future conflicts. Of course, the United States cannot deter all conflicts from occurring. However, well-informed global campaign plans can and should inform the prioritization of operational activities tied to certain potential conflicts the joint force deliberately seeks to deter.
Incorporating all instruments of power
The joint force need not abandon its traditional strengths; rather, it ought to smartly evolve its approaches to incorporate all instruments of power to expand access, fuel understanding, and generate a range of options regardless of location within the competition continuum. Increased training and education on the nature of authorities and tools that the various instruments of power can bring to the fight is critical for joint leaders. In this way, entities like the State Department or Intelligence Community do not simply represent “concurrence” boxes that must be checked to get military operations approved. Rather, they can be incorporated as partners that offer unique access vectors, diverse understanding, and a variety of tools to support or be supported by military actions, whether at the tactical, operational, or strategic levels. As described in this framework, adopting this change bolsters the joint force’s capability to target within any domain, and similarly expands the nature of effects, fires, and actions available to achieve desired outcomes.
Joint Interagency Task Forces (JIATFs) exemplify this approach and could be scaled to enable joint targeting and effects generation. Scaling a similar approach to that of the JIATF, however, requires cultural adaptation. JIATFs are tailor-built to address singular problems and combine multiple instruments of power—and their accompanying authorities and capabilities—under a single chain of command to create unity of effort. However, unity of effort does not necessitate unity of command: The joint force can lead the integrated deterrence effort without being in charge, and it often does play a supporting role to its interagency counterparts. This requires senior leaders to establish a culture that moves beyond “coordination” and “deconfliction” and toward “collaboration.” Increased organizational trust, built upon real-world operational experiences, will increase trust both across departments and in the disparate datasets produced across the instruments of power, ultimately amplifying the predictive capabilities of the AI architecture this framework is reliant upon. Moving toward collaboration is similarly critical as it pertains to enhancing the aggregate power among allies and partners.
Embracing the global nature of problem sets
The joint force must also embrace the concept of a global, multi-domain contact layer. When viewing the world solely through the lens of armed conflict, the joint force focuses narrowly on Russia in Europe and the PRC in the Indo-Pacific. Targeting and effects generation in Latin America, Africa, or the Arctic are then insufficiently regarded as supporting, complementary, or niche efforts rather than as potential key components of integrated deterrence. Many operational efforts—such as security force assistance, building a partner’s combat capability, gaining access, and illuminating vulnerabilities of an adversary’s capabilities—require significant time and resource investments. Senior leaders must understand why, for example, a multiyear effort to gain placement and access in Equatorial Guinea fits within the global campaign to counter PRC malign influence; otherwise they will be less likely to resource it (in this case, Equatorial Guinea is a candidate for the establishment of what would be the PRC’s first Atlantic naval base).23David Vergun, “General Says China Is Seeking a Naval Base in West Africa,” US Department of Defense, March 17, 2022, https://www.defense.gov/News/News-Stories/Article/Article/2969935/general-says-china-is-seeking-a-naval-base-in-west-africa/ As such, combatant commanders who lead global campaign plans, such as the global campaign plan for China, should prioritize regularly communicating their priorities to other combatant commands when activities take place in another geographic area of command. This is especially important when activity falls under the authority of a different combatant command.
Generating senior leader understanding is a by-product of cultivating a joint force that thinks with a competitive mindset. As former Chairman of the Joint Chiefs of Staff General Joseph F. Dunford recognized, the United States “think[s] of being at peace or war…our adversaries don’t think that way.”24Dunford: Challenges Require More Than ‘Buying New Hardware,’ Association of the United Stated Army, October 10, 2016, https://www.ausa.org/news/dunford-challenges-require-new-hardware. Altering the “peace or war” mentality to a deeper understanding of activities across the competition continuum—and adopting a strategy of proactive targeting harnessing all instruments of power—is necessary to simultaneously deter aggression and effectively prepare for conflict. Combatant command force structure changes; intergovernmental professional training, education, and exercises; and in-garrison and deployed intergovernmental cross-pollination are beyond the scope of this paper but are among concepts worth exploring to enable cultural changes at scale.
Technology and data: Building a resilient and holistic data architecture
The DOD must build a robust and extensive data architecture, fusing private sector data with government data, and build frameworks and standards to harness it into actionable information. Data fuels everything from access and understanding, to options, targeting, and analysis, to predictions and recommendations. For data to be usable, however, it must first be accessible. Accessibility must occur at echelon given the nature of CDO environments and the expectation that severed links between the tactical edge and higher headquarters elements will be the norm, not the exception.
The joint force needs a data architecture in line with, and as a central component of, the JADC2 concept that aggregates data from all sensors across all domains to enable a proactive framework for targeting and effect. The architecture must encompass the tactical edge, fusing commercial and government-procured data across a spectrum of classification levels. In line with the DoD Data Strategy, such an architecture must make data visible, accessible, understandable, linked, trustworthy, interoperable, and secure.25US Department of Defense, DOD Data Strategy. The DOD must involve the private sector in the process of building this architecture and consider how interoperability standards and technologies can be integrated and kept up to date. Not only will this help the joint force accelerate the PED cycle and act on intelligence, but it will also allow the joint force to operate across the scale of attribution to mitigate the operational and counterintelligence risks inherent to strategic competition.

Moreover, the joint force must explore how classified intelligence can safely be used to facilitate AI/ML algorithmic training. Otherwise, it may inadvertently incur risk to sources, methods, or exquisite platforms. Alternatively, with the appropriate mechanisms, AI/ML algorithms can be trained to reach similar conclusions as classified analysis using only open-source data. This will greatly enhance the joint force’s ability to export capabilities to allies and partners without concern for security-sharing agreements or classification obstacles.
Authorities, rules of engagement, and risk: Updating DOD guidelines and standards
DOD guidelines and standards must be updated to harness all tools of national power and to enable combatant commands to prioritize global issues alongside their regional areas of responsibility. For distribution of data to achieve the desired effect, the joint force must explore changes in the distribution of authorities, rules of engagement, and the nature of assessing risk. While a lack of authorities is frequently cited as a barrier to accomplishing operational activities, it is often the cumbersome means by which to access existing authorities that stands in the way. If a joint force commander (JFC) can exercise kinetic strike authority at their level but require permission from several echelons higher to execute information operations, the JFC will increasingly rely on kinetic effects. Authorities often lack clear processes by which subordinate commanders can quickly access them. Similarly, when authorities are reserved at the highest echelons, the approval authority is farthest removed from the problem, lacks adequate understanding, and often leads to excessive risk aversion. This plays out with the array of authorities germane to the joint force and will only become more complex and burdensome when expanding the aperture to include other instruments of power. At a minimum, when the National Command Authority delegates authorities to combatant commanders, there ought to be a standardized and coherent process by which subordinate echelons of command can access them efficiently. Additionally, an effective JADO/JADC2 operating environment that collects, disseminates, and harnesses data requires more effective coordination across the US services and manufacturers. The development of standards must be pursued to advance capabilities that are interoperable across the joint force and with US allies. Doing so will help improve the speed and precision of the targeting cycle.
Second, streamlining the approach to accessing authorities goes hand in hand with updating the joint force’s rules of engagement. These concepts help mitigate the concerns around disparate joint force elements operating with degraded or nonexistent contact with higher headquarters elements. Rules of engagement allow for commanders to lead through intent instead of specific guidance, facilitating more rapid and creative localized targeting and effects generation. Distribution of authorities and associated rules of engagement could transform a unit’s guidance from “employ electronic warfare (EW) effects against Russian ORLAN-10s” to “disrupt Russian ISR below 5,000 feet AGL.” The former is prescriptive and limiting; the latter is intent based, provides greater flexibility, and informs the necessary capabilities for the tactical edge to operate autonomously for longer periods of time.
Finally, the department must rethink the way it assesses risk in light of integrated deterrence and a global contact layer. Making informed decisions on risk management is a key underpinning of this framework. Yet, risk assessments are traditionally conducted in a temporal manner: the risk associated with a particular activity, in a particular location, with a particular target. Risks associated with strategic competition are not, however, suited to traditional ways of thinking. Competing with adversaries across a global contact layer requires considering how local risk ties into strategic risk, whether that be transregional or trans-domain. This is further complicated by the imperative to effectively prepare the joint force for combat. If, for example, a particular PRC capability presented a significant problem for the joint force’s ability to execute a contingency response plan, significant investment may be required to mitigate the threat. This may lead to a scenario in which the joint force assumes greater risk elsewhere in the globe to gain access to locations where the PRC has proliferated similar capabilities to increase understanding and develop options for use during crisis. A similar situation could arise where the joint force makes the decision to reveal a capability it would otherwise hold in reserve to complicate an adversary’s decision-making and risk calculus, thus enhancing deterrence. Maturing the joint force’s ability to assess risk in this manner must begin with data-informed understanding, shared consciousness, and unity of effort across all instruments of power.
Conclusion
Cultivating a joint force that enables and supports a whole-of-government approach to integrated deterrence is a daunting yet achievable vision, requiring transformational leadership to achieve. “Humans are more important than hardware,” and how leaders harness the joint force’s enduring strategic advantage of human capital will dictate whether success is achieved.26US Special Operations Command, “SOF Truths,” https://www.socom.mil/about/sof-truths. This paper has outlined a vision to update the way the joint force conducts targeting and effects generation for an era of strategic competition. Evolving the joint force’s model for targeting and effects will require adopting a mindset shift that sees competition as key to setting the conditions for, and ideally avoiding, armed conflict. To truly operationalize integrated deterrence, the joint force must embrace targeting and effects across the competition continuum, leveraging the range of tools at its disposal across its domestic and international counterparts, and avoiding a solely military or kinetic lens. Moreover, through the power of AI, the DOD can harness data for effect and fuel the proactive, continuous, and global campaigning required for integrated deterrence.
Sponsored By

This report was generously sponsored by Lockheed Martin Corporation. The report is written and published in accordance with the Atlantic Council Policy on Intellectual Independence. The authors are solely responsible for its analysis and recommendations. The Atlantic Council and its donors do not determine, nor do they necessarily endorse or advocate for, any of this report’s conclusions.
About the authors

Gen James E. Cartwright, USMC (ret.)
Former Vice Chairman of the Joint Chiefs of Staff, US Department of Defense
The views expressed in this academic research paper are those of the author(s) and do not reflect the official policy or position of the US government or the Department of Defense. In accordance with Air Force Instruction 51-303, Intellectual Property—Patents, Patent Related Matters, Trademarks and Copyrights, 1 September 1998, this research paper is not copyrighted but is the property of the United States government.

Forward Defense, housed within the Scowcroft Center for Strategy and Security, generates ideas and connects stakeholders in the defense ecosystem to promote an enduring military advantage for the United States, its allies, and partners. Our work identifies the defense strategies, capabilities, and resources the United States needs to deter and, if necessary, prevail in future conflict.


