Rockshot, Standingpalm, Software, Shoot!

Scenario Summary
In November 2022, while Qatar was hosting the FIFA World Cup, staff at the Ras Abu Fontas noticed a water-cooling issue within the plant. The staff managed to contain and resolve the problem in 11 hours but did not release a notice to the public. Information was later leaked, causing mass panic buying of water in Qatar, especially within the migrant community, and backlash online in the Twittersphere. Qatar Electricity and Water Company hired Fenghuang Labs, a Chinese company, to investigate the attack. Fenghuang Labs blamed the US based on prior attacks on Yuma software capabilities analyzed by the Chinese threat intelligence community. In the second round, it was unveiled that the backdoor in Yuma software was developed by a CIA asset working for Nikara Solutions in China.
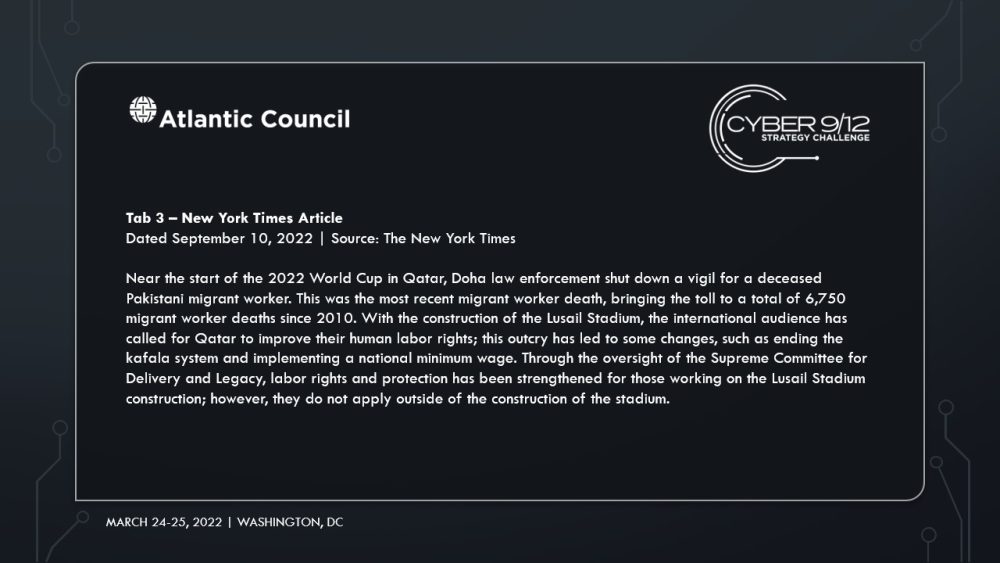
In Intelligence Report I, competitors are introduced to the initial attack and its immediate aftermath. During the 2022 FIFA World Cup kickoff, Qatar Energy and Water Company’s Ras Abu Fontas desalination plant experienced a disruption of their temperature sensors, preventing the water from reaching high enough temperatures, resulting in a low water yield. This malfunction inhibited the plant from meeting the high demand for water from the World Cup attendees. Ras Abu Fontas employees were informed by their Security Operations Center manager that malware caused the sensors to malfunction. The plant received approval to tap into the water reserves and restored the sensors to working order by using backups of the software that controls the sensors. This restoration occurred 11 hours after the activity commenced. While the plant did not release information about the attack, social media was quickly populated by news and rumors surrounding the attack at the plant. Rumors amplified the angry sentiment that the water disruption disproportionally affected the migrant worker community. This community, which comprises a substantial portion of Qatar’s population, was involved in building the infrastructure required to host the 2022 World Cup.
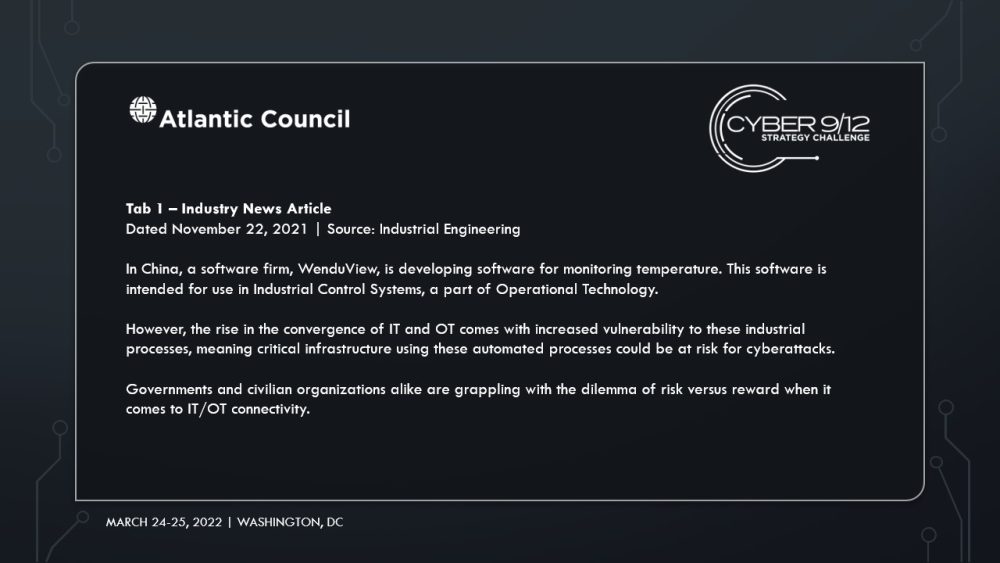
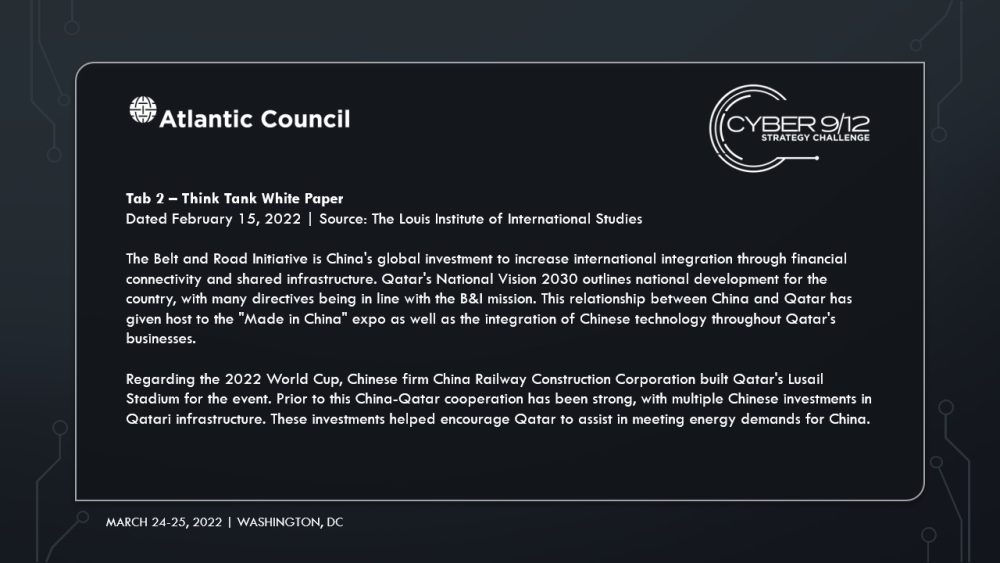
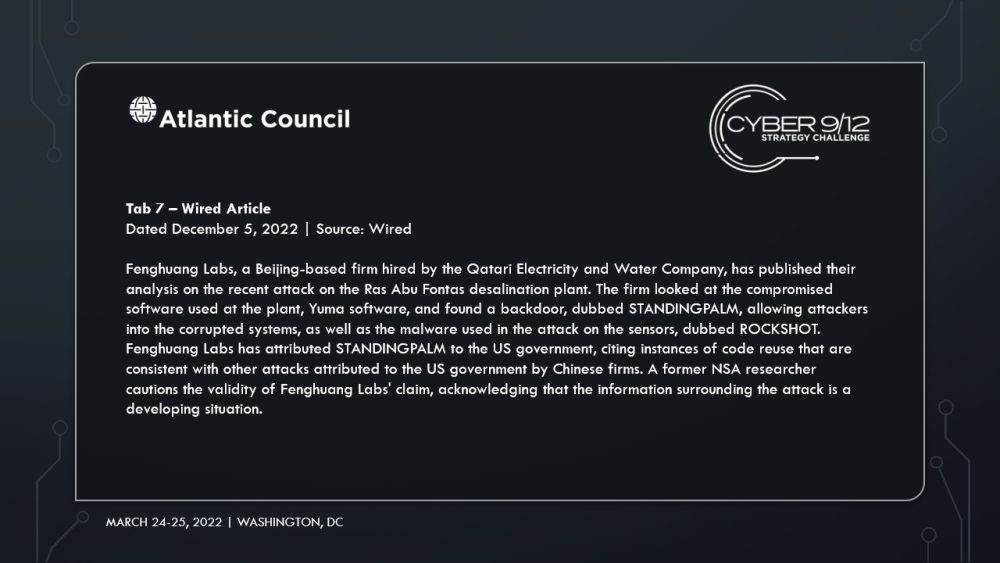
Fenghuang Labs, a Beijing-based incident response firm, was hired by Qatar to investigate the attack. Chinese-Qatari relations are strong due to China’s economic involvement with the Gulf States through the Belt and Road Initiative. Fenghuang Labs claimed that the software used by Ras Abu Fontas, Yuma software, had a backdoor, dubbed STANDINGPALM, allowing the malware that affected the sensors, dubbed ROCKSHOT, to be installed on the plants systems. Fenghuang Labs attributed the attack to the US government, and cited previous attacks attributed to the US government as being consistent in nature with this attack. The lab also noted that many companies around the world using Yuma also contain STANDINGPALM. In response to this accusation, France’s OCLCTIC informed the US government that they will be monitoring the evolution of the investigation of the attack. Both the US and Emirati governments offered their support to Qatar.
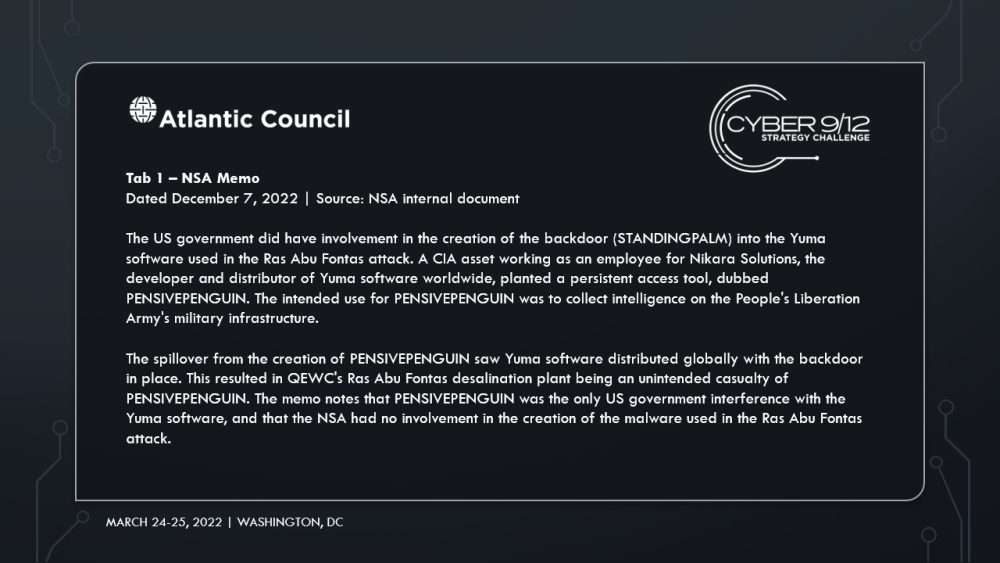
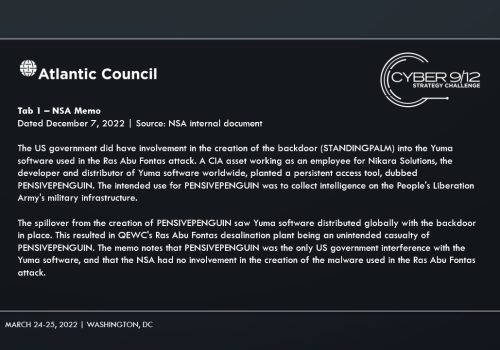
In Intelligence Report II, competitors were provided with further information on the aftermath of the initial attack. In a briefing, the NSA internally disclosed within the US government that STANDINGPALM, known as PENSIVEPENGUIN within the US Government, was a backdoor planted by a CIA asset working within Nikara Solutions for the purposes of collecting intelligence on the People’s Liberation Army’s military infrastructure. The memo stated that Qatar was not an intended target of PENSIVEPENGUIN and that the attack was committed by a non-US Government actor, and that the destructive payload used in the attack was not created by the NSA. A news article published after the initial attack in Qatar reports that Nikara Solutions created a patch for STANDINGPALM, but only distributed it within China, leaving other nations vulnerable to attacks. In Qatar, an American citizen working for the Ras Abu Fontas plant was detained for allegedly being linked to the Ras Abu Fontas attack.
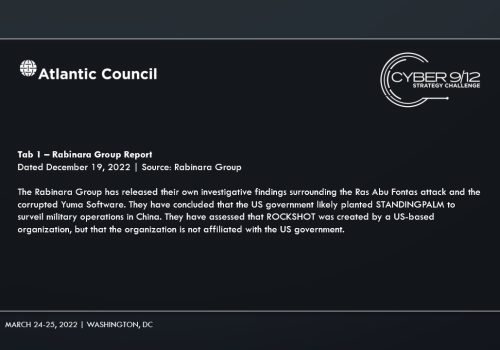
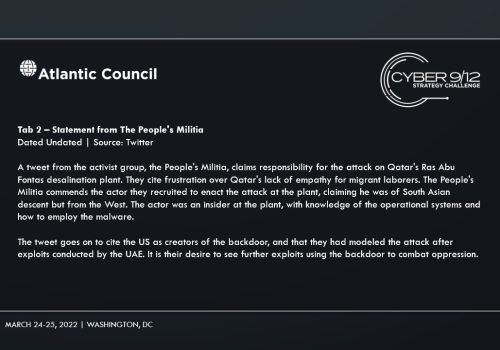
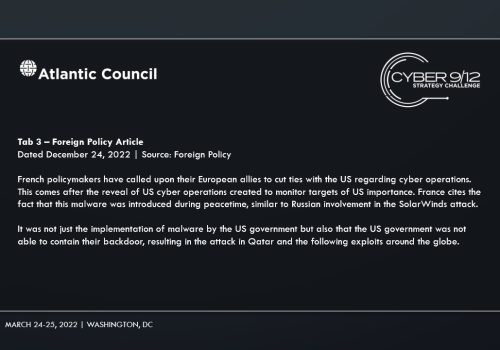
In Intelligence Report III, competitors learned that an organization known as the Rabinara Group published their own analysis of the attack and assigned attribution for STANDINGPALM to the US government. In a final Twitter post, the People's Militia claimed responsibility for the attack on Ras Abu Fontas, and cited their frustrations with the maltreatment of migrant workers in Qatar as the reason for their attack. The People’s Militia also alluded to an operative of theirs who was instrumental in the attack as being of South Asian heritage. France called for its European allies to cease any collaboration or involvement with the US government in cyberspace and cited US cyber operations and how the backdoor vulnerability was exploited outside of US containment, as reasons for ceasing joint cyber operations.
From March 25 to March 26, 2022, participants analyzed how they can best A) respond to allegations of US responsibility in the attack, B) retain control of cyber vulnerabilities, and C) maintain international partnerships with Qatar and France.
Below we feature the policy analysis and recommendations of a handful of teams who succeeded in advancing to the semi-final and final rounds of the 2022 Washington, DC competition.
Find the complete scenario here.
Intelligence Report I
Intelligence Report I Top Recommendations
Intelligence Report I Policy Options

American University Cyber sQuad
Team members: Laila Abdelaziz, Kady Hammer, Taylor Kerr, Alex Neubecker
Cyber sQuad from American University categorized their recommendations into four courses of actions: investigate, mitigate, communicate, and anticipate. The team provided packages of policy recommendations for the immediate term (72 hours), short term (1-6 weeks), and long term (2+ months).
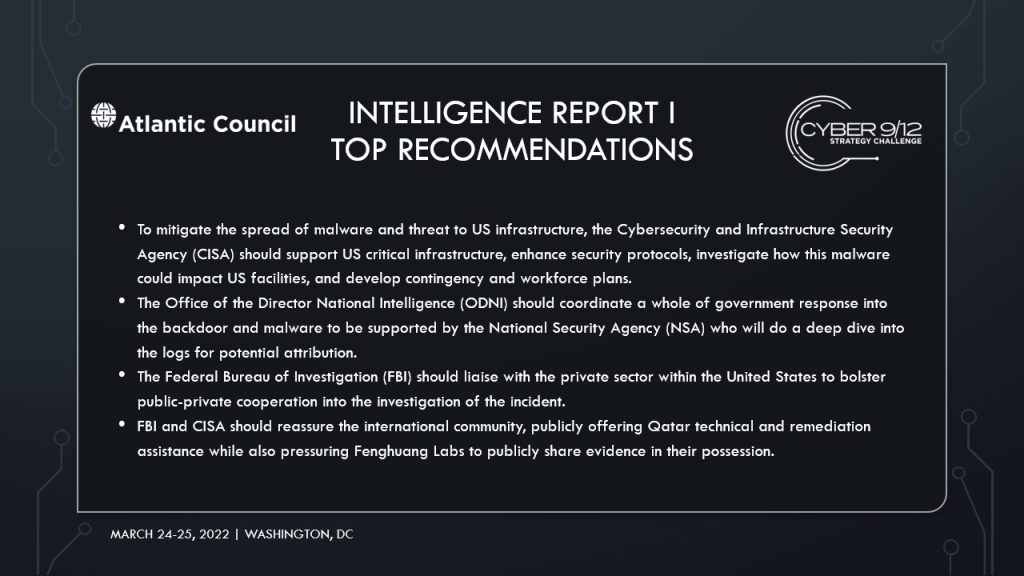
The investigation category called for the Office of the Director of National Intelligence (ODNI) to coordinate a whole government response into the backdoor and malware supported by the National Security Agency (NSA) performing a deep dive into logs for potential attribution. For mitigation, the Cybersecurity and Infrastructure Security Agency (CISA) must mitigate potential spread of the malware and backdoor access to later provide open-source patches and resiliency of critical infrastructure. AU’s Cyber sQuad also stressed that communication coordinated by the Department of State (DOS) with US allies and media was critical to smoothing a variety of international tensions. Building on the communication pillar, the anticipate category recommended proposed proactive alerts and the readying of CYBERCOM Protection Teams in case of further backdoor and malware proliferation.
Read AU Cyber sQuad’s Intelligence Report I written policy brief and decision document.

Harvard University Ghost in the Shellcode
Team members: Winnona DeSombre, Michaela Lee, Emma Plankey, Bethan Saunders
Harvard University’s Ghost in the Shellcode offered three levels of policy recommendations but endorsed their middle policy package entitled “Aid and Attribution Diplomacy.” This policy package aims to provide solutions for domestic resiliency, concrete steps to engage France and Qatar, and mitigate diplomatic spillover of allegations against the United States.
Aid and Attribution Diplomacy presents four deliverables. First, it calls for the DOS and the Federal Bureau of Investigation (FBI) to publicly issue a joint statement affirming that the US government is utilizing available resources to investigate the attack. Ghost in the Shellcode recommends the US Intelligence Community work amongst themselves in a classified manner to attribute the actors. Next, the team suggests the FBI engage private sector partners within the US to support the investigation. The final policy recommendation is to have USAID ship bottled water to the regions to assist with the ongoing shortage of supply. The team recognized that while this set of policy recommendations would smooth tensions with French and Qatar, it might increase tension with the Chinese government. The investigation into attribution might aggregate Chinese actors who already attributed the incident to the US government.
Read Ghost in the Shellcode’s Intelligence Report I written policy brief and decision document.

New York University APT 2785 (aka PURPLE APPLE)
Team members: Shagun Nayar, Louie Reckford, Chadwick Shroy, Alastair Whitehead
APT 2785 (aka PURPLE APPLE) from New York University developed policy recommendations that sought to decrease uncertainty by gaining a deeper understanding of the risks, demonstrate that the US was a responsible cyber actor, and limit China’s ability to exploit the situation. To do so, the team broke down their approach into three categories: understand, prepare, and reassure.
To understand, APT 2785 called on USCYBERCOM and the Central Intelligence Agency (CIA) to investigate the origins of STANDINGPALM and ODNI to investigate the origins of ROCKSHOT malware to reach a potential attribution. To prepare, the team tasked CISA and the Environmental Protection Agency (EPA) with drawing in relevant private sector knowledge to conduct vulnerability assessments into Yuma software and provide a remediation strategy, with the EPA promoting it to the public. Next, APT 2785 suggests the FBI and CISA reassure the international community, publicly offering Qatar technical and remediation assistance while also pressuring the Chinese to publicly share evidence in their possession. The last step for reassurance called for the US government to use classified military and diplomatic channels to reassure allies it was not involved, and it will share information about the attack when more is uncovered.
Read APT 2785’s Intelligence Report I written policy brief and decision document.

University of Colorado, Boulder ZeroDarkNerdy
Team members: Andrew Nadas, Emmeline Nettles, Katherine McDonald, Nadin Al Milaify
ZeroDarkNerdy identified five pillars of concern and proposed policy actions for each pillar through core actions (short term), expansionary (long term), and escalatory recommendations. The team identified critical risks to address as: the spread of the malware/threat to US infrastructure, international reputation impacts, regional stability, US citizens and installations in Qatar, and humanitarian concerns.
To mitigate the spread of malware and threat to US infrastructure, the team called on CISA to support US critical infrastructure, enhance security protocols, investigate how this malware could impact US facilities, and develop contingency and workforce plans. To deter further detrimental reputation impacts, it was recommended that DOS through the Bureau of Cyberspace Digital Policy should reaffirm norms and deny US involvement. To promote regional stability, the US should offer resources like the FBI and ODNI to support Qatar’s investigation and bolster other potential critical infrastructure protections. To protect US citizens and installations, it is critical to investigate airbases and plan for contingencies of evacuation. Finally, to address humanitarian concerns, the team called on the White House and other US organizations to release statements on human rights, labor rights, immigration rights, and potential push Qatar to release a statement condemning the action as well.
Read Zero Dark Nerdy’s Intelligence Report I written policy brief and decision document.
Intelligence Report II
Intelligence Report II Top Recommendations
Intelligence Report II Policy Options

American University Cyber sQuad
Cyber sQuad from American University organized their recommendations into three components: investigate, remediate, and anticipate.
Focusing on the immediate term, in the investigation section, the team tasked the FBI, Department of Justice (DOJ) and ODNI to draw in support from the larger intelligence apparatuses, both foreign and domestic. The FBI and DOJ were recommended to outreach to Qatari law enforcement and investigate the People’s Militia and other US threat actors in efforts to uncover the threat through a multinational push. ODNI was tasked with calling in the US Intelligence Community to investigate foreign actors, attribute the malware, and obtain a copy of the malware for backdoor patching, continuing to bolster partnerships into the long run. In the next step of remediation, the President of the United States (POTUS) would communicate with leaders in France and Qatar to repair relationships by offering FEMA, CYBERCOM, and National Guard assistance. In the longer term, both were tasked with continuing to bolster multinational relationships. Other US based agencies were tasked with coordinating patch development. The last step of anticipation called for proactive measures in the form of alerting the private and public sector entities of the incident so they might fortify their resilience. In addition to these recommendations, the team associated risk levels of their recommendations.
Read Cyber sQuad’s Intelligence Report II decision document.

Harvard University Ghost in the Shellcode
Ghost in the Shellcode from Harvard University’s Kennedy School in the second part of the competition prioritized protecting US critical infrastructure, ensuring resilience of the global economy, regaining trust with US allies, and preventing the sacrifice of priorities in the cyber domain. To achieve these strategic goals, the team presented a policy package named “Respond” aimed at providing solutions for domestic and global resiliency, creating avenues for engagement with France and Qatar, and developing opportunities to regain trust without the sacrifice of cyber capabilities.
To achieve these objectives, the FBI was tasked with launching a public investigation into domestic organizations leveraging STANDINGPALM and the US national who abetted the attack. DOS was responsible for translating Yuma patching guidance into 50+ languages that CISA was to draft vulnerability guidance on. DOS and the White House were to liaise with Qatari and European officials to repair international relationships.
Read Ghost in the Shellcode’s Intelligence Report II decision document.

University of Colorado, Boulder ZeroDarkNerdy
ZeroDarkNerdy narrowed their scope for their final decision document focusing on three rather than five components. Zeroing in on intelligence remediation, building global resilience, and communications planning, the team proposed three minimal risk policy packages.
For intelligence remediation, the group brought in the Central Intelligence Agency (CIA) to connect with their asset and ensure saftey and ability to continue missions. They called for the larger Intelligence Community to conduct assessments of short- and long-term effects on national security. To build global resilience, CISA was called to secure critical infrastructure domestically and abroad through CERT cooperation. DOS and USAID were to offer long term work force development for international cooperation support. To bolster communications, ZeroDarkNerdy called on the White House and DOS to deny malware implementation allegations and promote to the public that the US government is bolstering cybersecurity to protect US assets. Further, the group suggested CISA, FBI, and Environmental Protection Agency (EPA) develop a joint task force for information sharing and coordinating efforts to repair water supply.
Read ZeroDarkNerdy’s Intelligence Report II decision document.

New York University APT 2785 (aka PURPLE APPLE)
In four lines of effort, APT 2785 calls for the US National Security Council to reassert, recover, repair, and restore following the second Intelligence briefing.
In pursuit of the reassertion strategy, APT 2785 recommends that as a responsible cyber actor, the United States should engage with the United Nation’s Security Council (UNSC) to establish cyber rules for great powers going forward. The recovery component of the strategy is colored by repairing critical relationships. APT 2785 focuses on drawing on US diplomatic channels of DOS to spearhead diplomatic talks for the Gulf states and USAID to re-establish Qatari water reserves. DOS is also tasked with messaging UAE and DOD smoothing relations with the French in an overall effort bolster relationship. To repair, APT 2785 focuses on patching malware both domestically and abroad through CISA, EPA, and NSA cooperation. In the restoration component of APT 2785’s strategy, the team recommends a review of lessons learned, calling for DOS to request consular access to the US citizen, an update on the US Intelligence Communities’ collection capabilities, and overall review by CISA and the FBI.
Read APT 2785’s Intelligence Report II decision document.
Intelligence Report III
Intelligence Report III Briefings
American University – Cyber sQuad
New York University – APT 2785 aka PURPLE APPLE PURPLE APPLE
University of Colorado, Boulder – ZeroDarkNerdy
Intelligence Report III Top Recommendations